Verify Json Web Token
This policy verifies the JSON Web token provided. If the token value has been tampered with or the token is wrong, it will not allow the user to access the resource.
Configuration
The properties that have to be configured to use the policy are described below.
Property | Description |
Basic | |
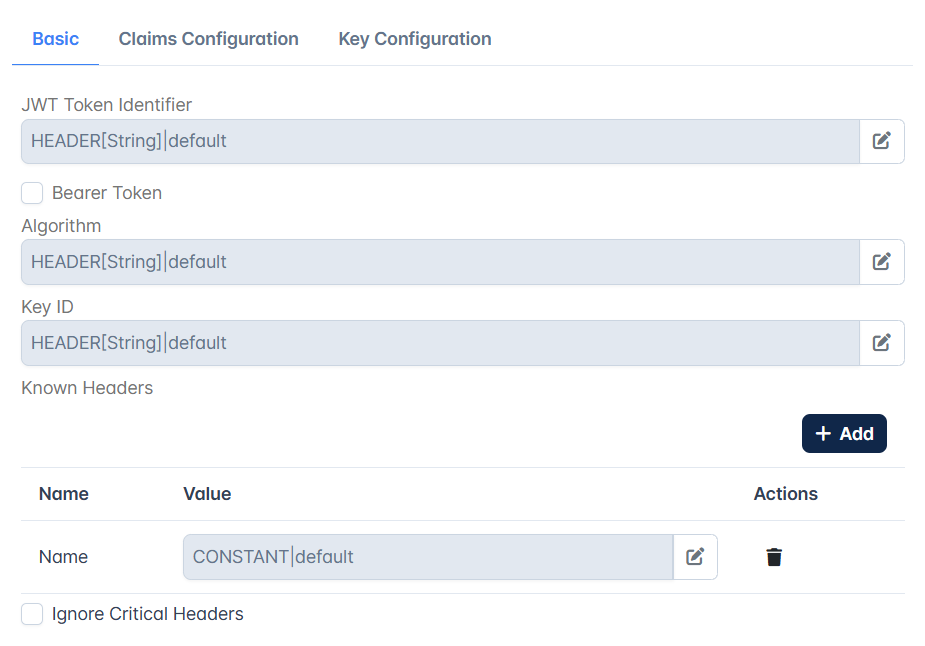
JWT Token Identifier | Configure the Message Part Identifier with the source as header/Query parameter/context variable/constant through which the JWT is passed. |
Bearer Token | If the JWT to be verified is being sent in the request's "Authorization" Header as a bearer token, then enable this property. |
Algorithm | Specifies the encryption/signed algorithm which was used to encrypt/sign the JWT provided in the JWT Token Identifier property above. Supported algorithms are HS256, HS384, HS512, RS256, RS384, RS512, PS256, PS384, PS512, ES256, ES384, ES512 , NONE. Provide any of the above-mentioned algorithm values as input to be used to verify the token. |
Key ID | The Key ID value corresponding to the algorithm (specified in the Algorithm property above) as provided in the Json Web Keys or the keys exposed in the Keys URL (described below). |
Known Headers | Verify JWT policy examines "crit" parameter in the JWT header, if present, and checks that each value listed under "crit" contained in JWT provided for validation is present among the entries under this "Known Headers" element i.e the "Known Headers" must contain a superset of the items listed in JWT's "crit" header. Any header that is found in "crit" header that is not specified here among <KnownHeaders> causes the policy to fail. |
Ignore Critical Headers | If this property is enabled, the policy ignores "crit" parameter in the JWT header. |
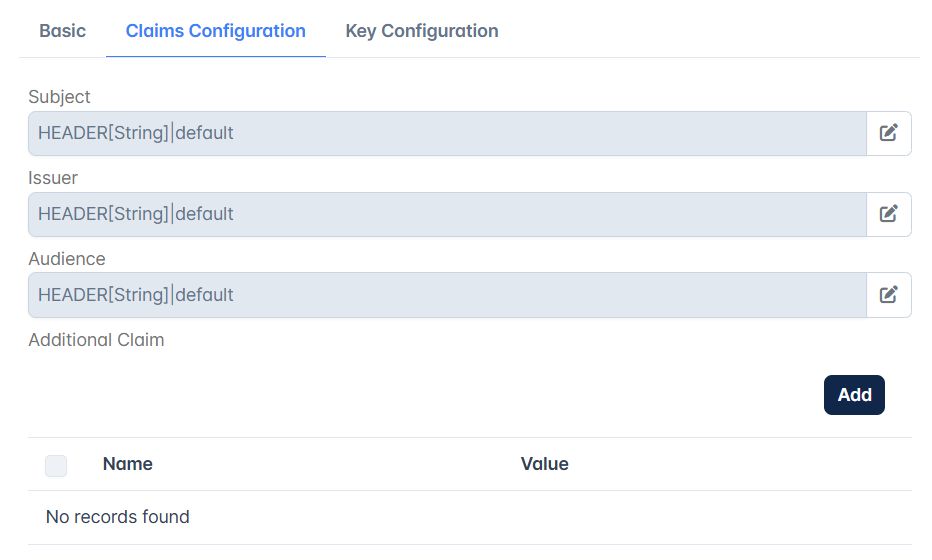
Claims Configuration
| |
Subject | This value should be same as that of the "sub" claim of the provided JWT for it to be valid. Provide values for Subject, Issuer, and Audience (described below) only if these values are provided in the Json Web Token policy |
Issuer | The "iss" (issuer) claim identifies the entity that issues the JWT. Provide the same value as that of "iss" claim contained in the provided JWT. |
Audience | The "aud" claim identifies the intended audience/recipients of the JWT. The audience value is comprised of comma comma-separated string. Make sure this value is present among those in the "aud" claim of JWT provided for successful validation. This property is optional. |
Additional Claim | Source-configurable custom claims can be specified here in order to verify their values against those present in the JWT provided for validation. Make sure every claim specified here is contained in the provided JWT, otherwise it is invalidated. |
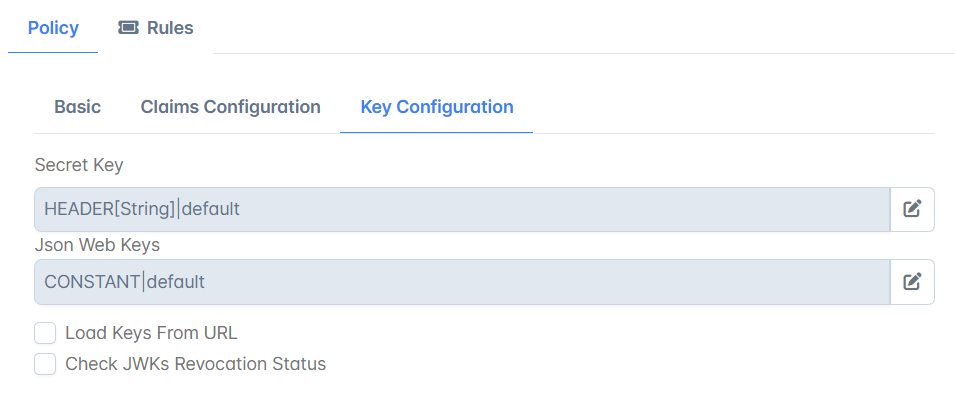
Key Configuration
| |
Secret Key | Provide when a symmetric algorithm like HS256 is specified. The minimum length of the string has to be 256,384,512 bits for HS256,HS384,HS512 respectively. |
Json Web Keys | Provide when an asymmetric algorithm like RS256 or ES256 is specified. For the JWK structure as in the sample above, refer to the link: https://tools.ietf.org/html/rfc7517. Alternatively, the Public JSON web Keys can be provided in the following ways:
|
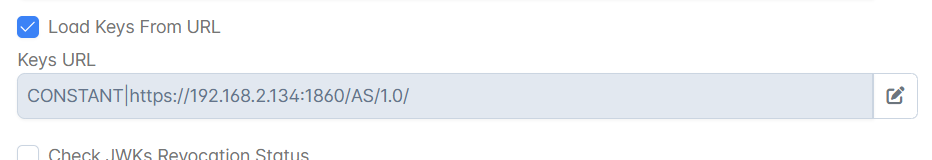
Load Keys From URL | Enable this property if Public Json Web Keys are exposed in a URL.
|
Keys URL | Specify the URL in which Public Json Web Keys are exposed. If it's a secured URL (Eg: https://www.googleapis.com/oauth2/v3/certs), the certificate of the corresponding server has to be added to the Truststore located at installer\esb\server\profiles\certs\jssecacerts. Password of this Truststore is "passphrase". Sample Keytool command for importing certificate into truststore with an optional entry name(alias) as is given below.
CODE
With this command, "samplecert1.cer" certificate can be added to the truststore "jssecacerts" with an entry name "samplealias". |
| Check JWKs Revocation Status | If this property is enabled, the public JSON Web Key being used for JWT verification shall be checked for its presence among the specified Revoked JWKs and verification would fail if the specific key is found to be revoked. |
| Revoked JWKs | Provide the revoked public JSON web Keys. |
| Load Revoked JWKs from URL | Enable this property if Revoked Public Json Web Keys are exposed in a URL. |
| Revoked JWKs URL | Specify the URL in which Revoked Public Json Web Keys are exposed. If it's a secured URL, refer to |
Verifying a Json Web Token
Request
Use the following URL in the browser/postman:
JWT Token Verify URL
http://192.168.2.231:2160/jsonVerifytoken/1.0?jwt-token=ewogICJ0eXBlIiA6ICJKV1QiLAogICJhbGciIDogIkhTMjU2IiwKICAia0lEIiA6ICIxMjM0NTYiCn0=.ewogICJzdWIiIDogIkpzb24tVG9rZW4tR2VuZXJhdGlvbiIsCiAgImlzcyIgOiAiRmlvcmFubyBzb2Z0d2FyZSBwcml2YXRlIGx0ZC4iLAogICJhdWQiIDogImF1ZGllbmNlIiwKICAiaWF0IiA6ICIyMDE4LTA5LTExIDIyOjM1OjEwIiwKICAiZXhwIiA6ICIyMDE4LTA5LTE1IDIyOjM1OjEwIiwKICAic2hvdyIgOiAiZmlvcmFubyIsCiAgImFkZGl0aW9uYWxDbGFpbSIgOiB7IH0KfQ==.n8YbWfgmw9v/4iYOnC7G2qFLhzUf3jVgQHUK8oWn7qg=Response
Attains access to the resources if the token is valid.