Json Web Token policy
Json Web Token policy generates a signed JSON Web token with a provided set of claims and header.
Configuration
The properties that have to be configured to use the policy are described below.
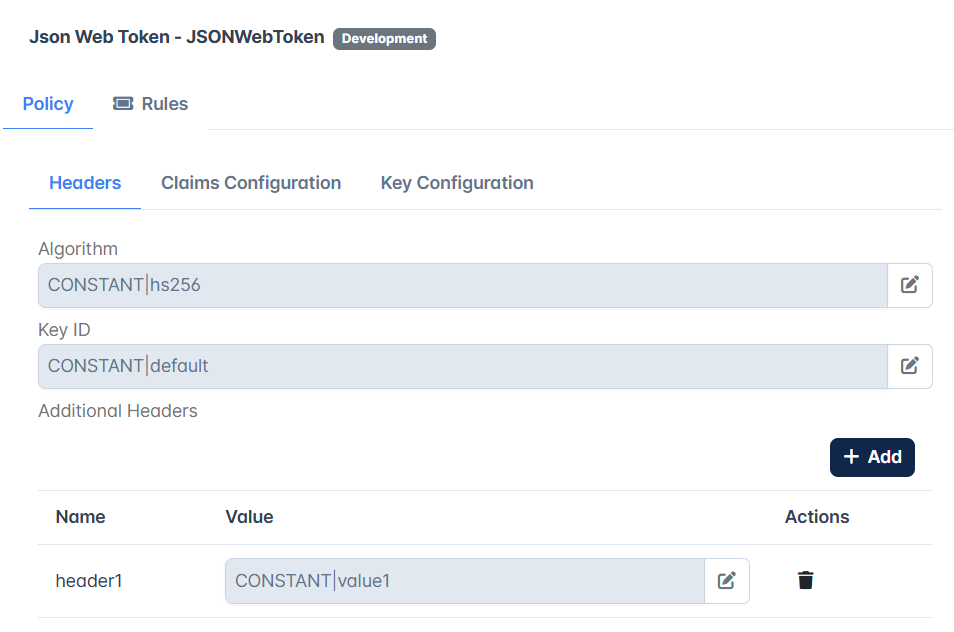
Figure 1: Json Web Token policy configuration attributes
Property | Description |
Headers | |
Algorithm | Specifies the encryption/signed algorithm to encrypt/sign. Supported algorithms are HS256, HS384, HS512, RS256, RS384, RS512, PS256, PS384, PS512, ES256, ES384, ES512 , NONE. Provide any of the above-mentioned algorithm values as input to be used to generate a token.
|
Key ID | The Key ID value corresponding to the algorithm (specified in the Algorithm property above) as provided in the Json web keys or the keys exposed in the Keys URL (described below). |
Additional Headers | This is to provide custom headers other than the above properties. Each header's value is source-configurable which means the value can be dynamically populated accordingly from the source chosen which can be Context variable/Header/Parameter/Constant. |
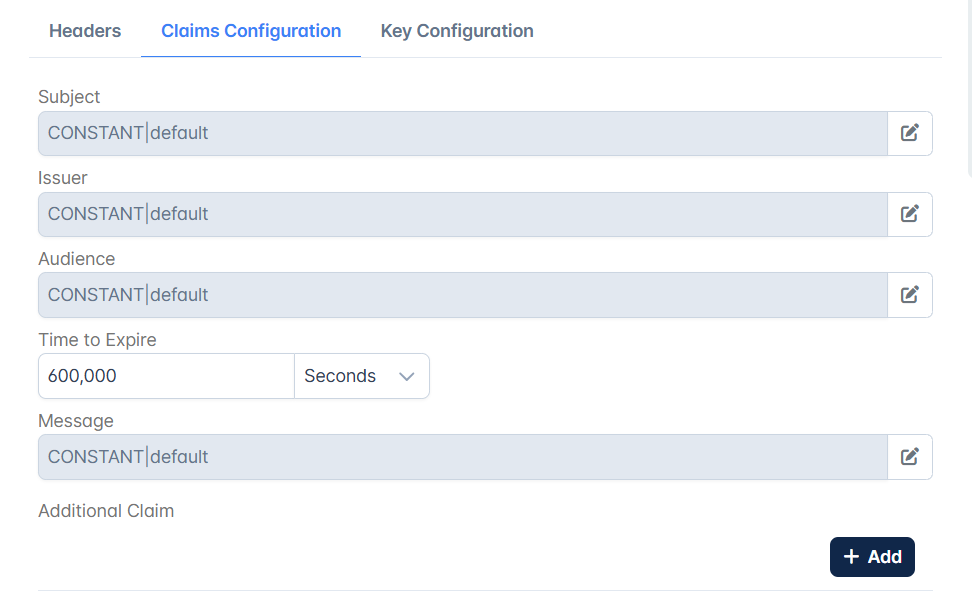
Claims Configuration
| |
Subject | The "sub" claim represents the subject of the JWT being issued. This property is optional. |
Issuer | The "iss" (issuer) claim identifies the entity that issues the JWT. This property is optional. |
Audience | The "aud" claim identifies the intended audience/recipients of the JWT. The audience value is comprised of comma separated string. This property is optional. |
Time to Expire | The expiry time of the token is that after which the token stands invalid. |
Message | The message that needs to be displayed. This property is optional. |
Additional Claim | This is to provide custom claims other than the above properties. Each claim's value is source-configurable which means the value can be dynamically populated accordingly from the source chosen which can be Context variable/Header/Parameter/Constant. |
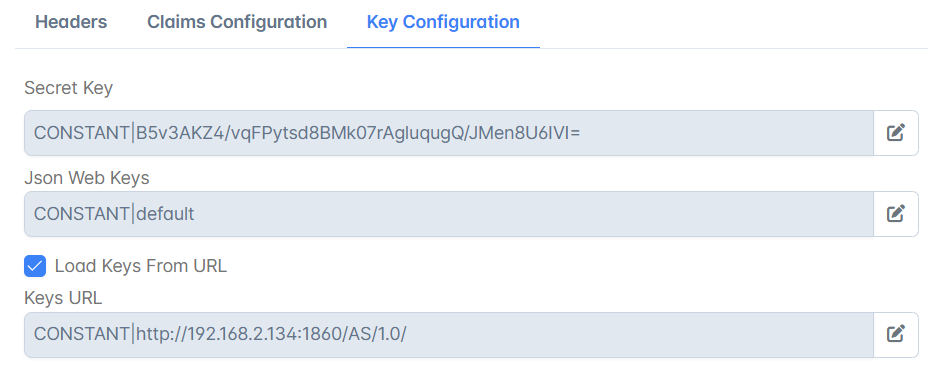
Key Configuration
| |
Secret Key | Provide when a symmetric algorithm like HS256 is specified. The minimum length of the string has to be 256,384,512 bits for HS256,HS384,HS512 respectively. |
Json Web Keys | Provide when an asymmetric algorithm like RS256 or ES256 is specified. For the JWK structure as in the sample above, refer to the link: https://tools.ietf.org/html/rfc7517 Alternatively, the Json Web Keys can be provided in the following ways:
|
Load Keys From URL | If Json Web Keys are exposed in a specific URL, then enable this property. |
Keys URL | Specify the URL in which Json Web Keys are exposed. If it's a secured URL (Eg: https://www.googleapis.com/oauth2/v3/certs), the certificate of the corresponding server has to be added to the Truststore located at installer\esb\server\profiles\certs\jssecacerts. Password of this Truststore is "passphrase". Sample Keytool command for importing certificate into truststore with an optional entry name(alias) as is given below.
CODE
With this command, "samplecert1.cer" certificate can be added to the truststore "jssecacerts" with an entry name "samplealias". |
Creating a JWT policy
Generate token using postman.
Request
CURL request to generate Json Web Token:
curl -X GET \ http://192.168.2.134:1860/jwt/1.0/Response
The generated JWT along with prefix "Bearer " is populated into context variables under the name "target.request.header.Authorization".
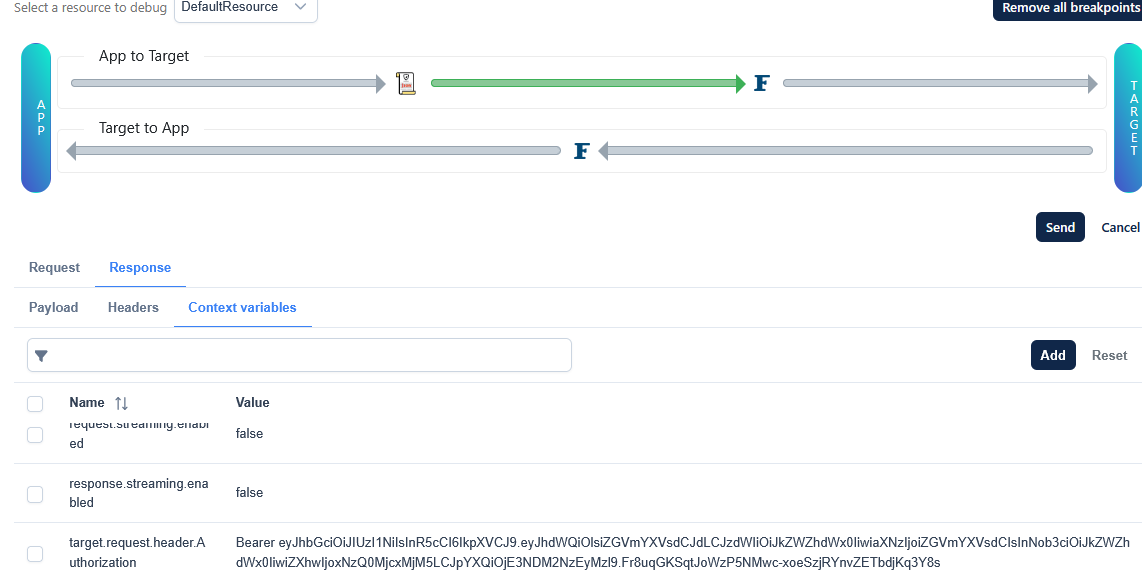
Figure 2: Json web token generated along with prefix "Bearer " populated into context variables