Verify Json Web Token
Contents
This policy verifies the generated JSON Web token. If the token value has been tampered or the token is wrong, it will not allow the user to access the resource.
Configuration
The properties that have to be configured to use the policy are described below.
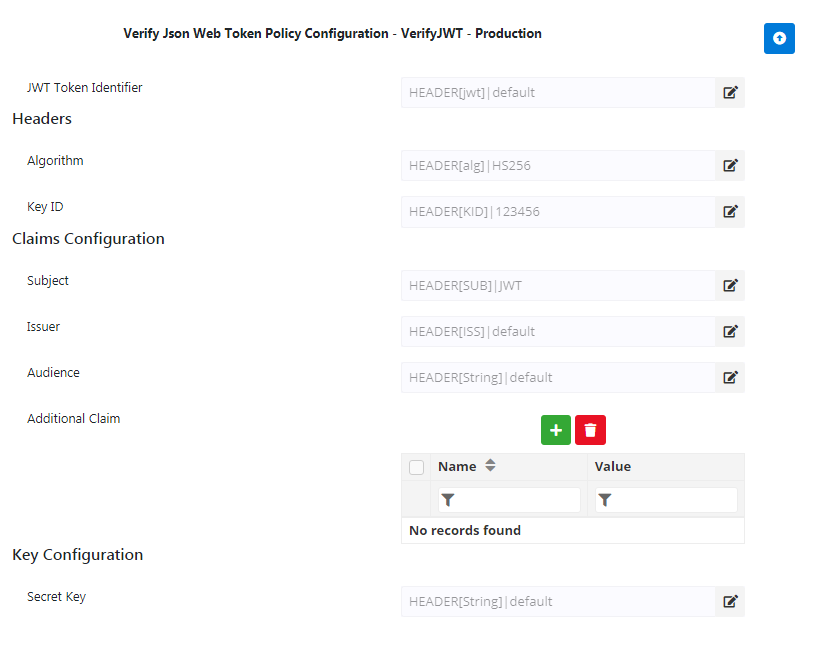
Figure 1: Verify Json Web Token policy configuration attributes
Property | Description |
| JWT Token Identifier | Configure the Message Part Identifier which contains the Content Type through which the JWT is passed. |
| Algorithm | Specifies the encryption algorithm (HS256 or RS256 or ES256) which was used for generating the token. |
| Key ID | The Key ID value corresponding to the algorithm chosen, which is provided in the JSON web keys. The JSON Public Keys can be provided in the following ways:
|
| Subject | Subject of the JWT issued as provided in the Json Web Token policy. Provide values for Subject, Issuer andAudience (described below) only if these values are provided in the Json Web Token policy |
| Issuer | The "iss" (issuer) claim identifies the entity that issues the JWT. Provide the same as provided in the Json Web Token policy. |
| Audience | Recipient value. The audience value is comprised of comma separated strings. This property is optional. |
| Additional Claim | To provide custom claims other than the above properties. |
| Secret Key | Where HS256 symmetric algorithm is chosen, Secret Key has to be provided. The minimum length of the string has to be 256 bit. |
Verifying a json web token
Request
Use the following URL in the browser/postman:
JWT Token Verify URL
http://192.168.2.231:2160/jsonVerifytoken/1.0?jwt-token=ewogICJ0eXBlIiA6ICJKV1QiLAogICJhbGciIDogIkhTMjU2IiwKICAia0lEIiA6ICIxMjM0NTYiCn0=.ewogICJzdWIiIDogIkpzb24tVG9rZW4tR2VuZXJhdGlvbiIsCiAgImlzcyIgOiAiRmlvcmFubyBzb2Z0d2FyZSBwcml2YXRlIGx0ZC4iLAogICJhdWQiIDogImF1ZGllbmNlIiwKICAiaWF0IiA6ICIyMDE4LTA5LTExIDIyOjM1OjEwIiwKICAiZXhwIiA6ICIyMDE4LTA5LTE1IDIyOjM1OjEwIiwKICAic2hvdyIgOiAiZmlvcmFubyIsCiAgImFkZGl0aW9uYWxDbGFpbSIgOiB7IH0KfQ==.n8YbWfgmw9v/4iYOnC7G2qFLhzUf3jVgQHUK8oWn7qg=Response
Attains access of the resources if the token is valid.
