Verify Json Web Signature Policy
This policy verifies the generated JWS. If the signature value has been tampered or the signature is different, it will not allow the user to access the resource.
Configuration
The properties that have to be configured to use the policy are described below.
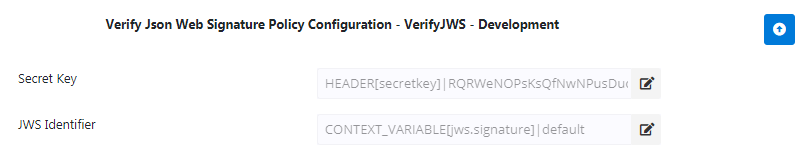
Figure 1: Verify Json Web Signature Policy configuration attributes
Property | Description |
| Secret Key | Where HS256 symmetric algorithm is chosen, Secret Key has to be provided. The minimum length of the string has to be 256 bit. |
Where asymmetric algorithms RS256 or ES256 is chosen, the public JSON Web Keys should be provided in any of the following ways:
| |
| JWS Identifier | Configure the Message Part Identifier which contains theContent Type through which the JWS is passed. |
Detached Content
In certain cases, it will be useful to protect the integrity of the content that is not itself contained in a JWS. Perform the following actions by detaching content as follows:
Create Assign Variable policy with the respective variable names and identifiers.
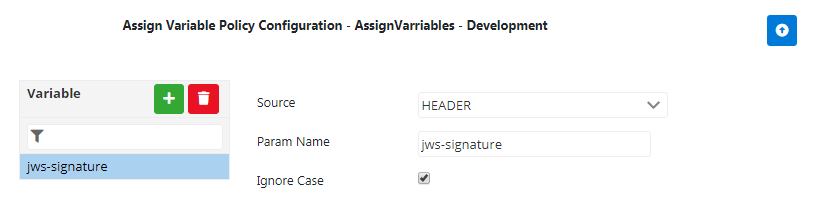
Figure 2: Verify Json Web Signature Policy configuration attributesThis sets the values in context variable with the specified names.
Go to $FioranoHome/APIManagement\samples\JavaCallOuts\DetachedJWSClaim and run the compiled script. This creates a Classes directory containing a jar with compiled classes.
The java class can be modified as per requirement.
- Configure Java Callout policy using the jar created above.
- Configure the Verify JWS policy as explained in this page.
Request
Use browser/postman to send the request as below:
curl -X POST \http://192.168.2.231:2160/verifycustomgignature/1.0/ \-H 'jws-signature:yJleHAiOiIxNTQ0MTgyNTY3MDQzIiwiYWxnIjoiSFMyNTYifQ==..u0MA9Bm95kkZU1McxzhHq/Qfm5fTaJRyFHMFzStzgWQ=' \-d '{"iss":"fiorano"}'The request contains JWS (Header and Signature) and claim as payload.
Response
Verifies the signature and allows to access the respective resources.
