Dashboard
Fiorano Webconsole provides a web-based monitoring tool for the Fiorano ESB Network and hence is commonly called the Dashboard. Apart from the monitoring feature, it also provides support for launching, stopping, and restarting an application using a web interface. The below section gives comprehensive insight into how to log on to the Dashboard and about the features available in each section of the Dashboard.
Login Page
Fiorano ESB Webconsole can be accessed by starting the Fiorano Enterprise Server (FES) and then opening http://localhost:1980/FioranoESB on a web browser. Alternatively, access it using the Fiorano Web Console link present on the Start Menu.
Replace 'localhost' with the IP address of the machine where the servers are running in case it is different from the local machine.
Log in by entering the credentials configured for the FES; the default credentials are:
- Username: admin
- Password: passwd
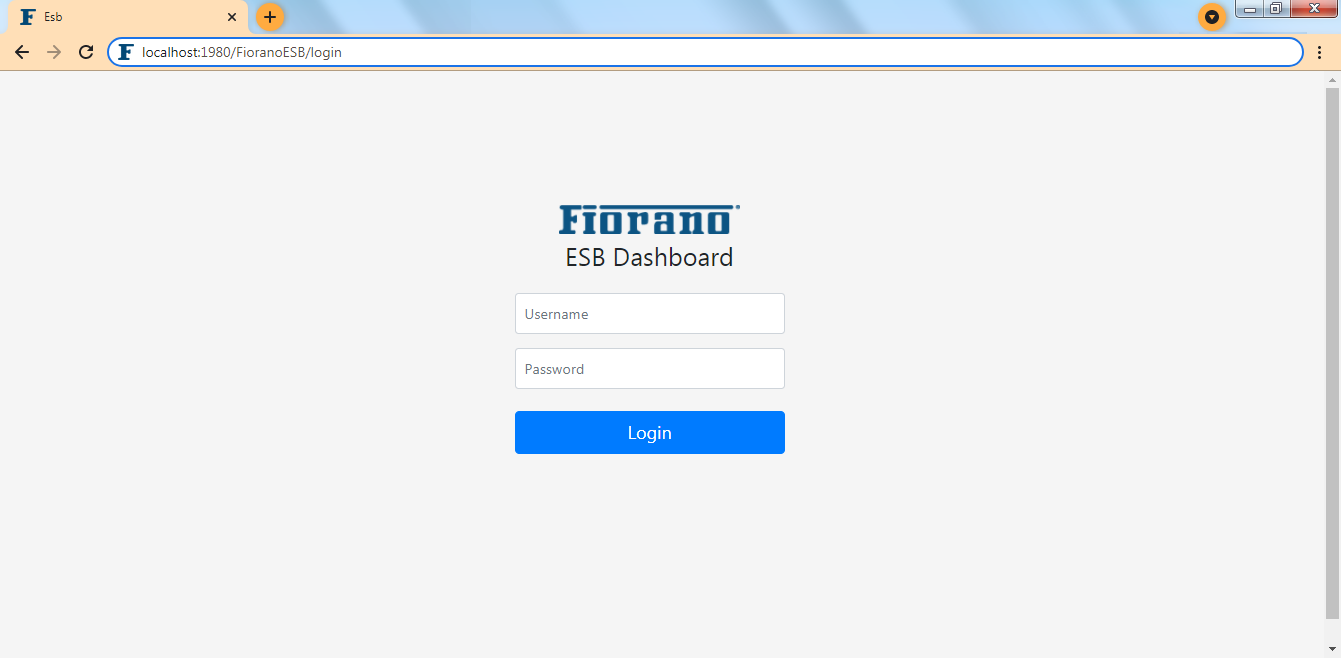
Figure 1: Fiorano Web Console Login Page
Each tab under the left navigation panel in the Fiorano Web Console (see the figure below), which is listed below, helps to accomplish various tasks.
Icon Reference
The following icons can be seen in the Dashboard. Refer to the table below to know what each icon implies.
| Icon Reference | |
|---|---|
 | Start |
 | Stop |
 | Restart |
 | Delete |
 | Download |
 | Details |
 | View Logs |
 | Download Logs |
 | Delete Logs |
 | Test a service |
Servers
The Servers tab shows the details of the available Fiorano Enterprise Servers, Peer Servers, and Server Groups.
Enterprise Servers
The top view of the Enterprise Servers page shows the server name, server profile, status, memory usage, and CPU Utilization.
Actions column
- This column provides capabilities to launch, stop, and restart a server.
- Clicking the Details link expands a bottom view to provide more details of the server such as Configuration, Destinations, Patches, Logs, and Thread Info as explained in the following sections.
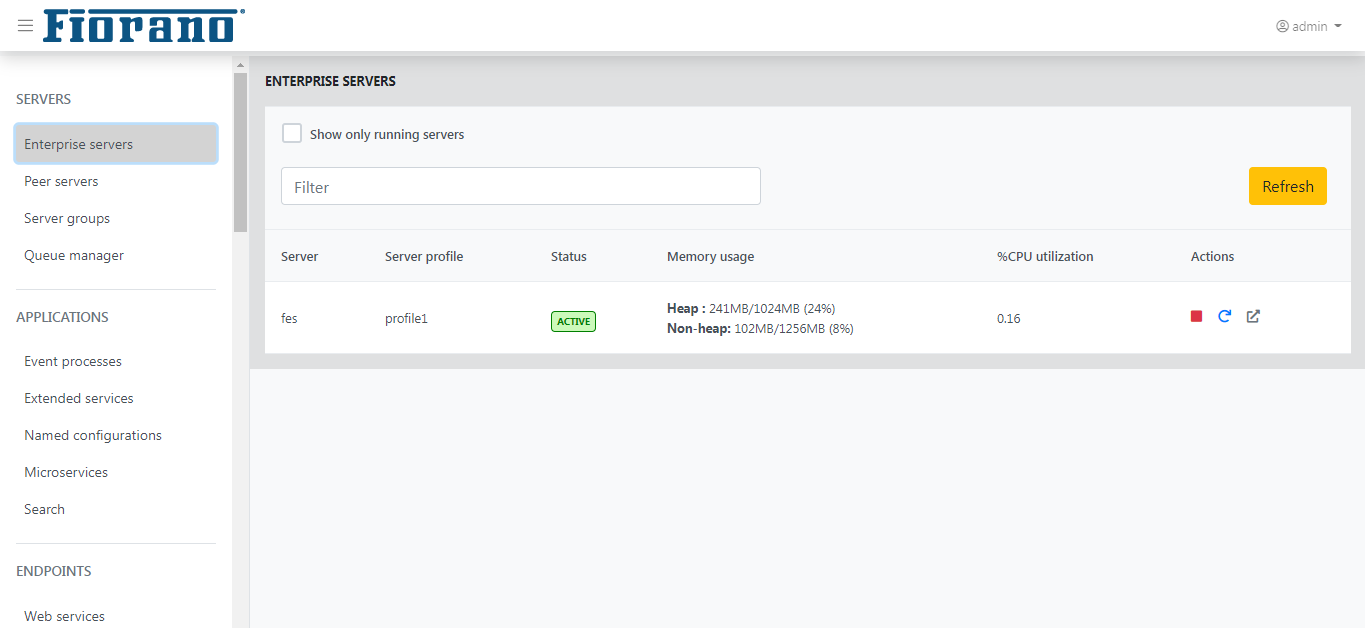
Figure 2: Enterprise Servers page showing FES details
Other options in the page
- The Show only running servers option filters and displays only those servers which are running.
- Click the Refresh button to display a newly added server (if it does not appear in the list).
- Use the Filter option to fetch a specific server by a keyword/name.
Configuration
Displays the basic details of the server and its configuration divided into two separate sections; click the respective headings to list the details.
Basic Details
It lists the details as follows: B2B Jetty port, BPM Jetty port, Dashboard Jetty SSL port, Dashboard Jetty port, HA enabled, Internal connections port, Max memory, Name, RmiConnectorServer listening port, Server PID, Server URL, Thread count, and Used memory.
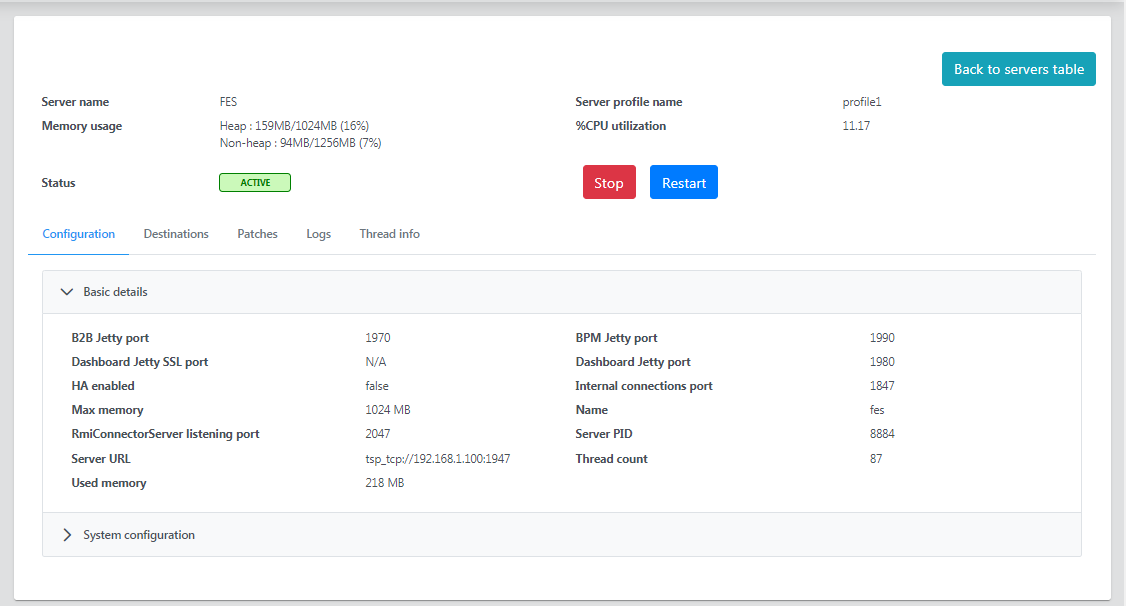
Figure 3: Basic details section under the Configuration tab
System Configuration
It lists the details as follows: Available CPU cores, IP, JRE, OS, RAM, Total disk space, Usable disk space, and Used disk space.
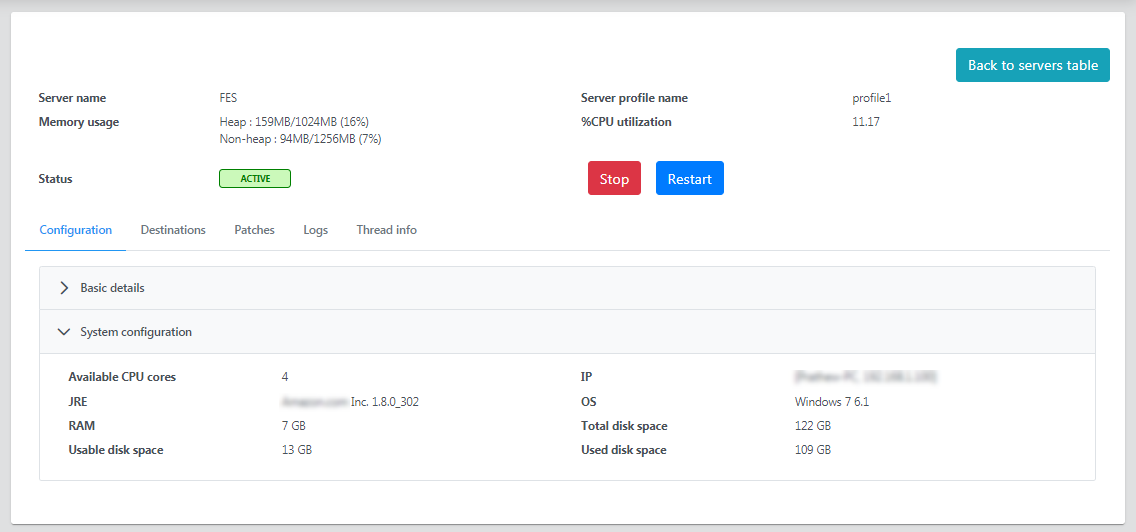
Figure 4: System configuration section under the Configuration tab
Destinations
Displays the details of Topics, Queues, and Connections divided into three separate sections; click the respective headings to list the details.
Topics
Displays the list of JMS topics present in the server with details such as Topic name, active subscribers, active publishers, and passive durable subscribers.
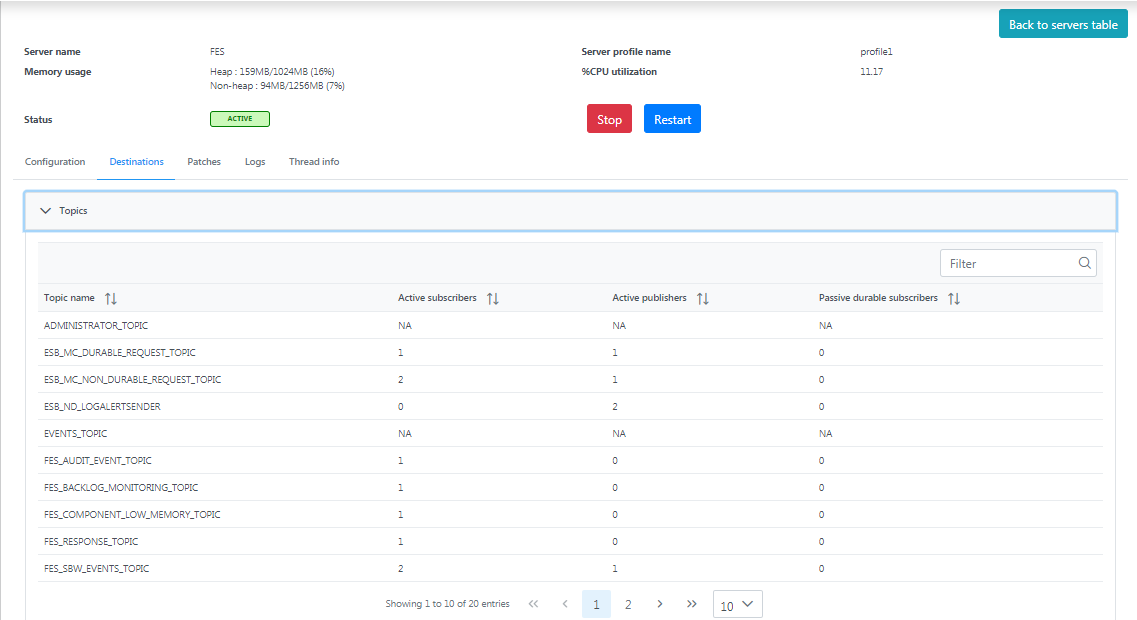
Figure 5: Topics section under the Destinations tab
Queues
Displays the list of queues present in the server with details such as Queue name, senders, receivers, pending messages, inbound messages, rate of inbound messages, outbound messages, and rate of outbound messages.
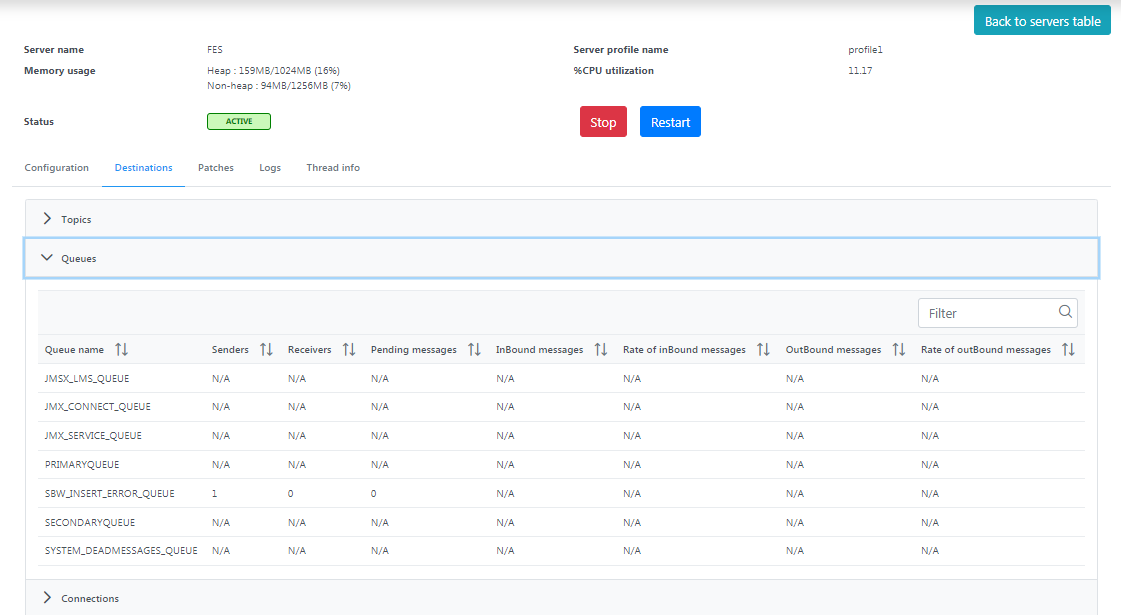
Figure 6: Queues section under the Destinations tab
To track messages in the Queues section, enable the EnableMessageMonitoring property under the QueueingSubSystem node in the Peer Server. Refer to the Enable Message Monitoring in the View Message Monitoring Logs section to see how to enable this from the Profile Manager perspective.
Connections
Displays the list of connections created by the server, along with the connection name and connection type.
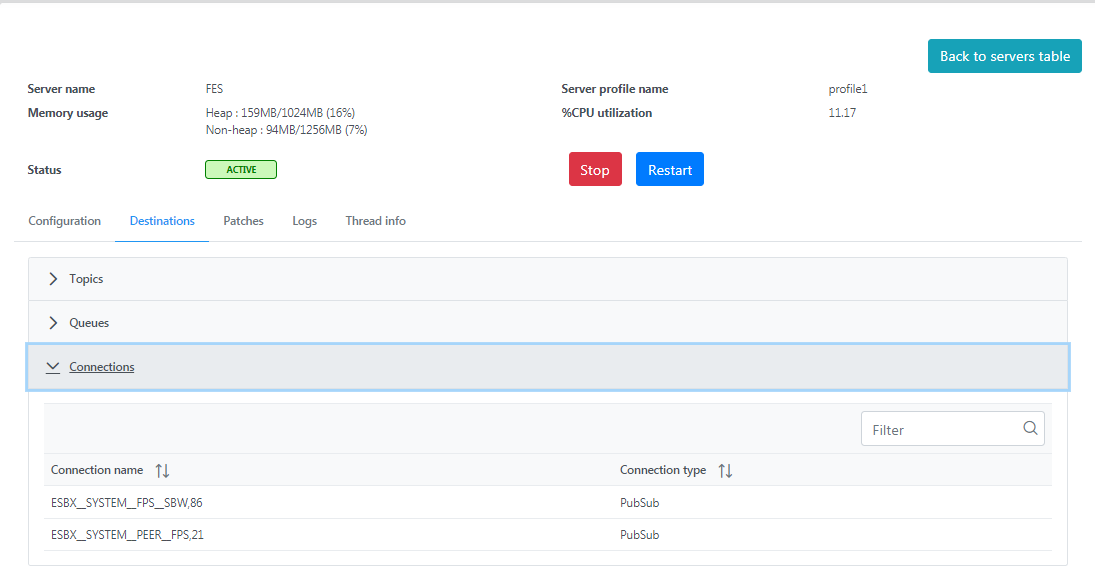
Figure 7: Connections section under the Destinations tab
Patches
Displays the details of the installed/uninstalled/failed patches to the server and microservices divided into two separate sections; click the respective headings to list the details.
Server
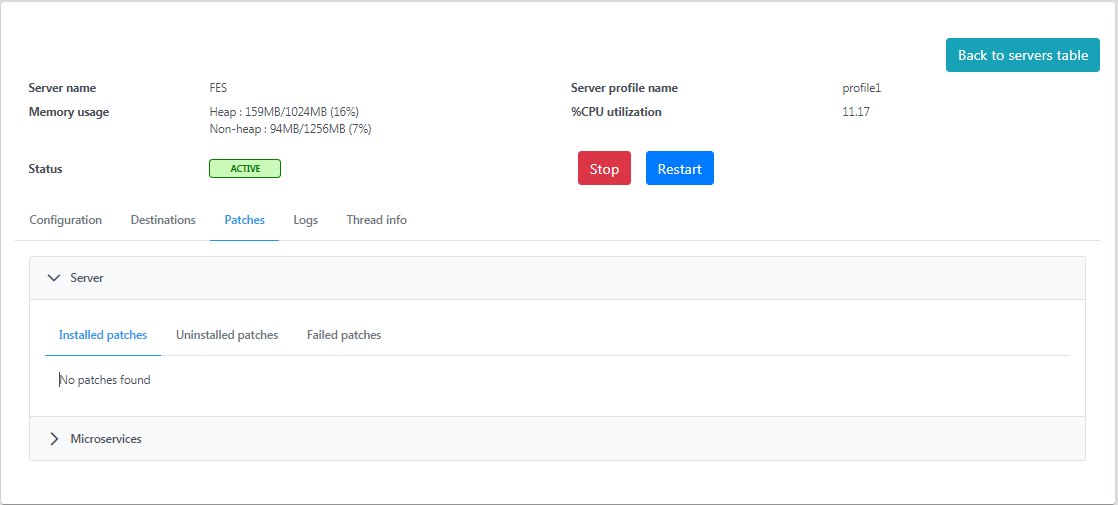
Figure 8: Server section under the Patches tab displaying details of installed/uninstalled/failed patches
Microservices
This section displays the patches installed for a microservice. After importing the patch from the eStudio Micro Service Repository, the microservice details are reflected here.
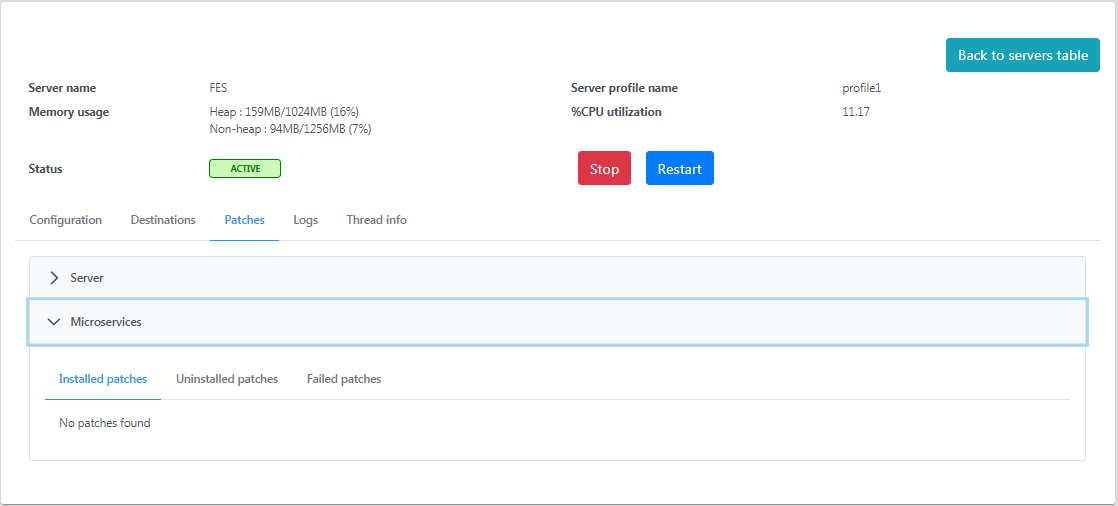
Figure 9: Microservices section under the Patches tab displaying details of installed/uninstalled/failed patches
Logs
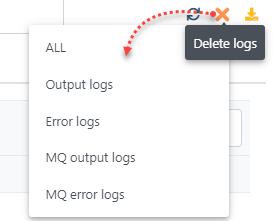
Displays the details of log messages such as output logs, error logs, MQ output logs, and MQ error logs with the date, type and detail of each log; click the respective headings to list the details.
| Icon Reference / Additional options | |
|---|---|
| Refresh logs to show the present logs |
 | Helps to delete the logs. Click the icon to choose to delete output logs, error logs, MQ output logs, and MQ error logs or all of these.
|
 | Downloads all the logs as a Zip file to the default downloads folder of the system. |
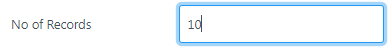 | Provide a number to define the number of rows of records to be displayed on the page. |
 | The Filter option helps to track a particular log by keyword. |
Output logs
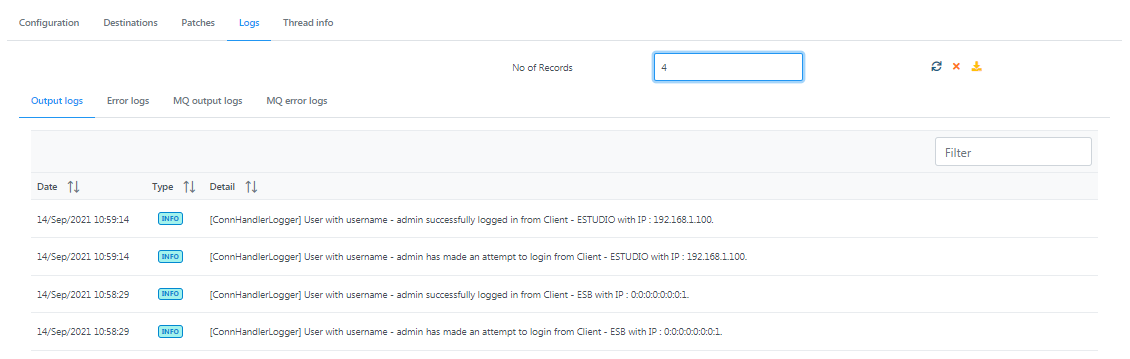
Figure 10: Output logs section under the Logs tab displaying date, type and details of logs
Error Logs
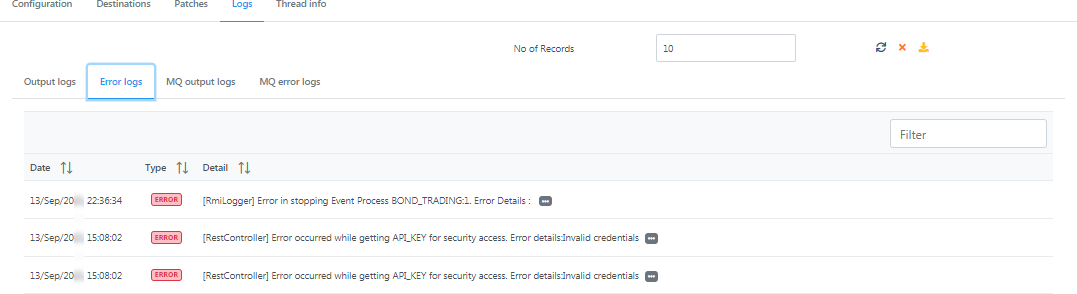
Figure 11: Error logs section under the Logs tab displaying date, type and details of logs
MQ Output logs
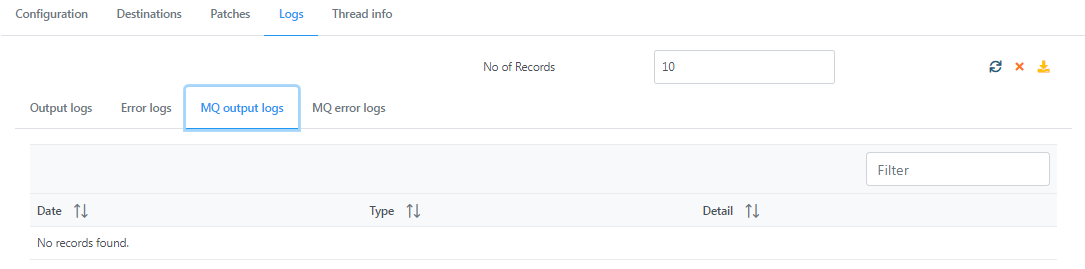
Figure 12: MQ output logs section under the Logs tab displaying date, type and details of logs
MQ error logs
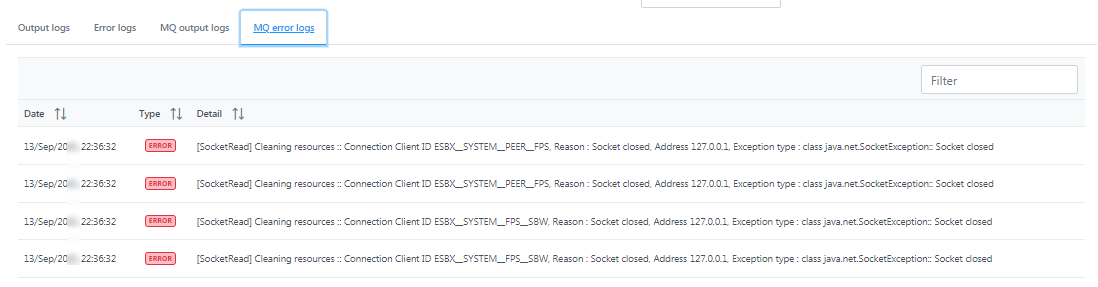
Figure 13: MQ error logs section under the Logs tab displaying date, type and details of logs
Thread info
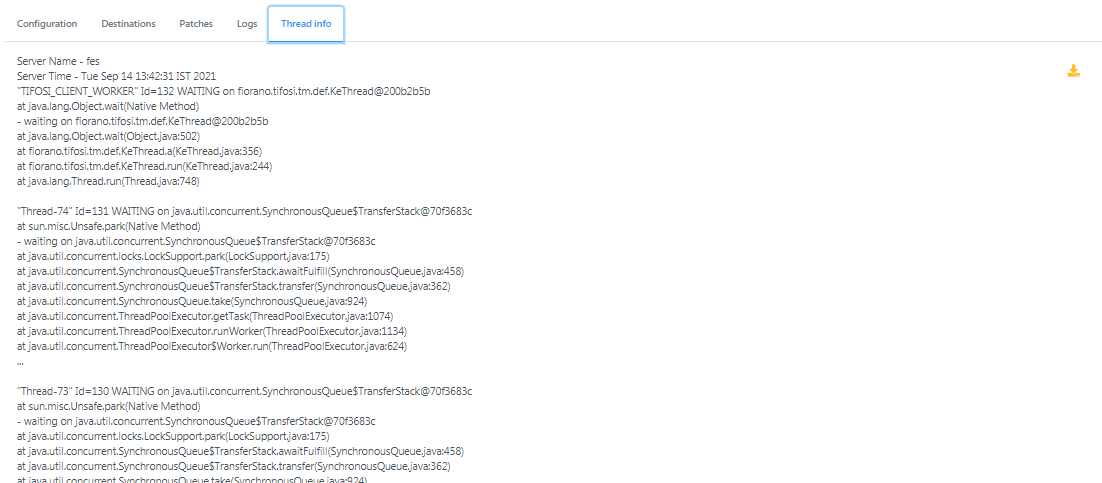
Figure 14: Thread info tab showing thread details of fes
Peer Servers
The top view of the Peer Servers page shows the server name, server profile, status, memory usage, and CPU Utilization.
- Refer to the Enterprise Servers section for descriptions, since all options present on this page are those present on the Enterprise Servers page.
- There are a couple of additional options on the Peer Servers page - Monitor tab in the Servers table (landing page) and Processes under Details which will be explained in the following sections.
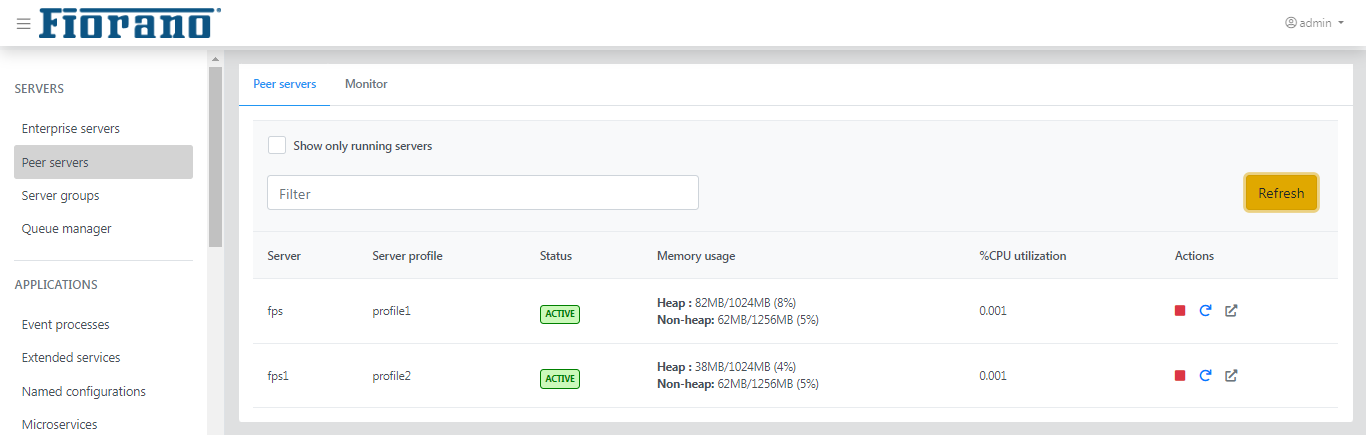
Figure 15: Peer server tab showing details of peer servers
Process
This section in the Details page shows the microservices running on the FPS as a result of the Event Processes that are running and the Extended Services working on the peer server; click the respective headings to list the details.
Running Components
Displays the list of microservices with details such as service instance name, service GUID, server version, application name, application version, launch type, memory usage, and process ID.
Click any header to sort in alphabetic order of the chosen column.
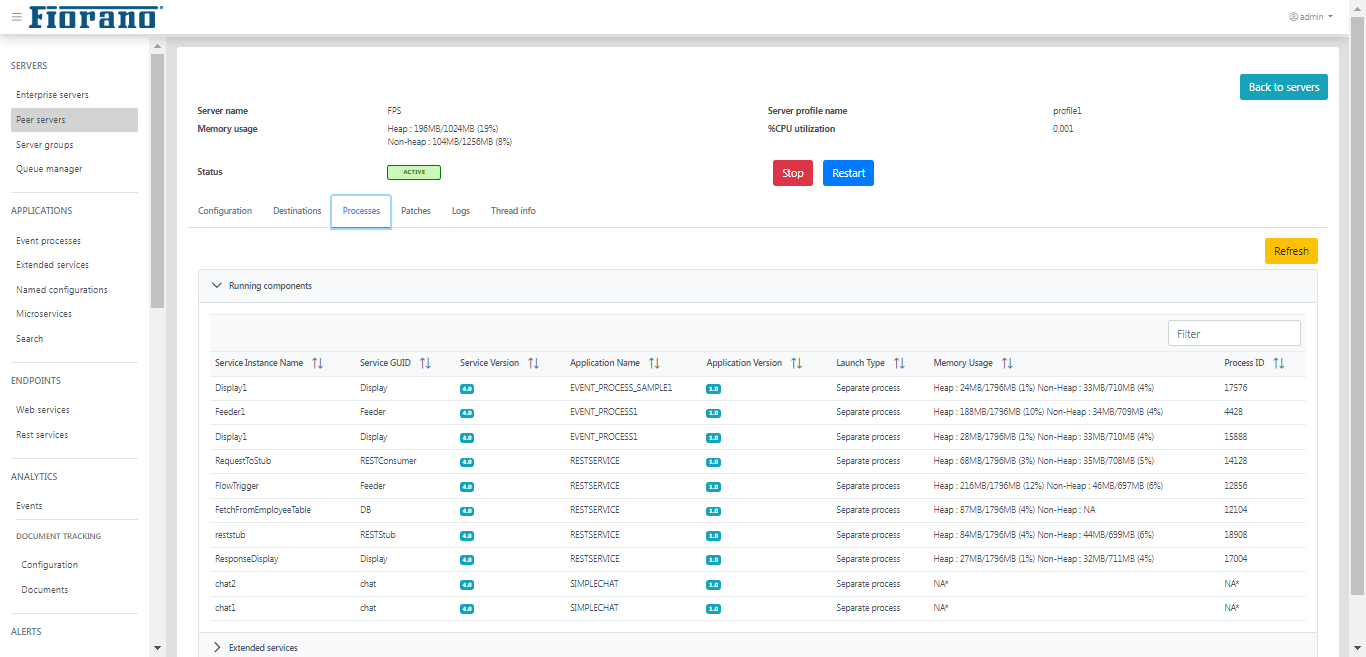
Figure 16: Running components section under the Processes tab displaying details of the microservices running on the peer server
Extended Services
Displays the list of Extended Services with details such as extended service GUID, version, status, start time, server group, route durable, and delete destination.
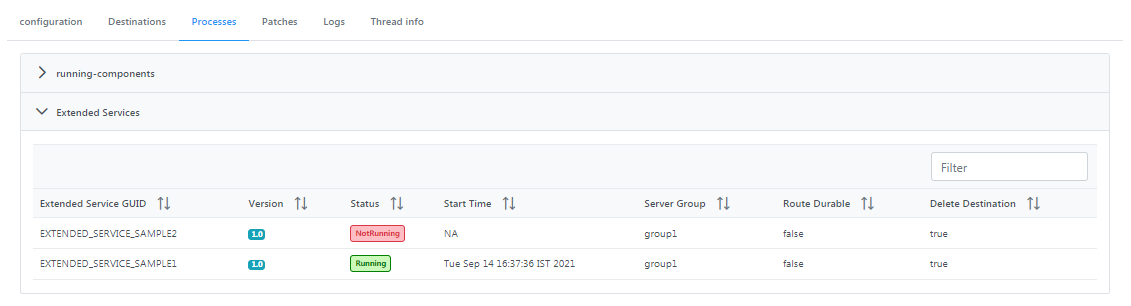
Figure 16: Extended Services section under the Processes tab displaying details of the extended service event processes running on the peer server
Monitor
Click the Monitor tab next to the Peer server tab for Server downtime/uptime monitoring. CPU utilization, downtime, and memory usage of a selected peer server will be graphically represented by various chart types such as line, bar, and radar graphs. Various options present on the page are:
- Peer name: Select the server to be analyzed.
- No of Records: Provide the number of records to be displayed in the chart.
- Date duration: Choose whether the analysis has to be done for the day, for the last 3 days, for the week, or for the month. The Custom date option can be used to analyze for a particular time period.
- Data Aggregation: Options change depending on the Date duration (above) By minute or by hour for the Date duration "Today", by hour or by day for Last 3 days, by day for Last Week, by month, by week and by day for Last month. Date aggregation type for the Custom date Date duration will be based on the period being chosen.
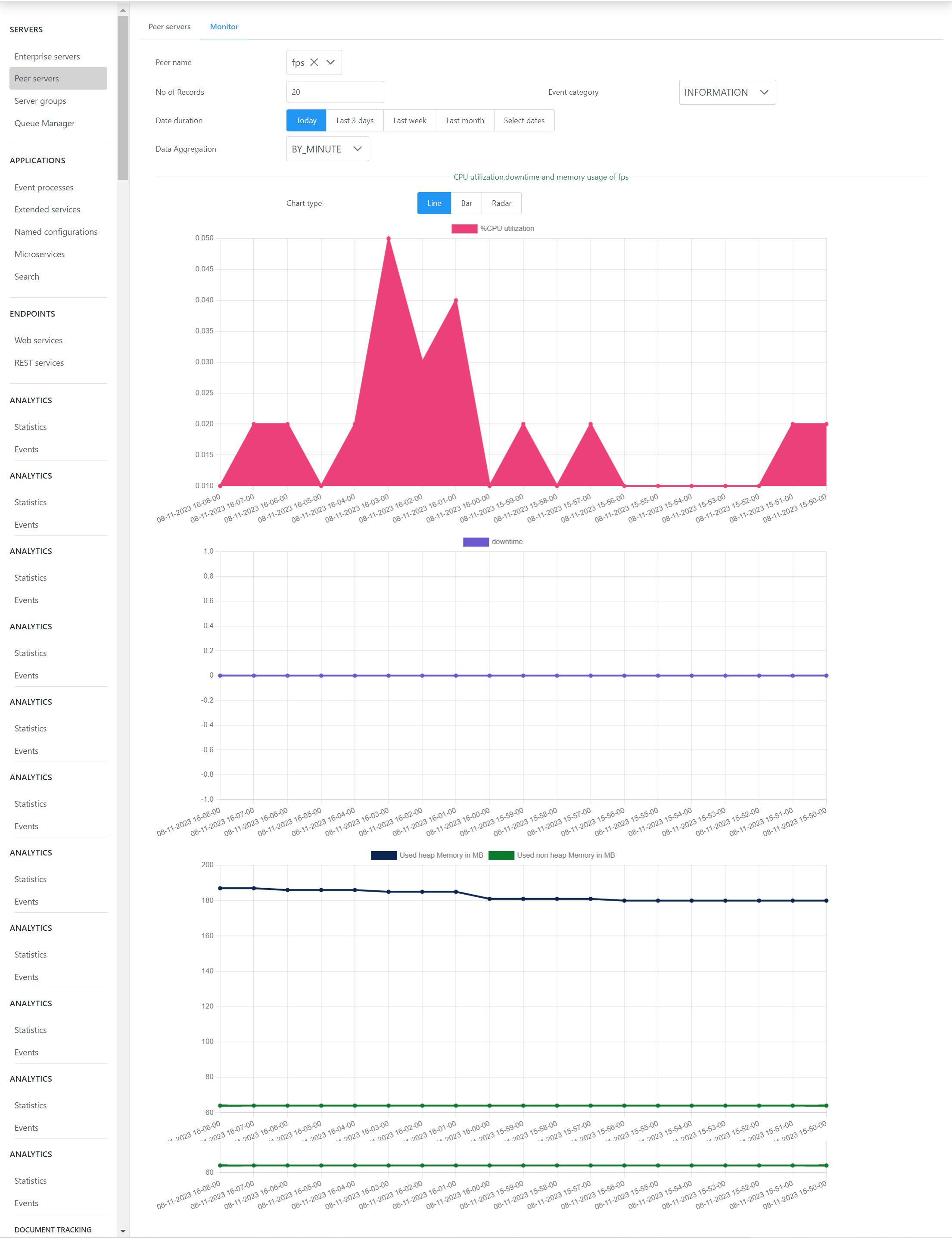
Figure 17: Monitor tab displaying a graphical representation of CPU utilization, downtime, and memory usage of a selected server
Server groups
A server group allows to keep multiple peer servers in a group which helps in load balancing.
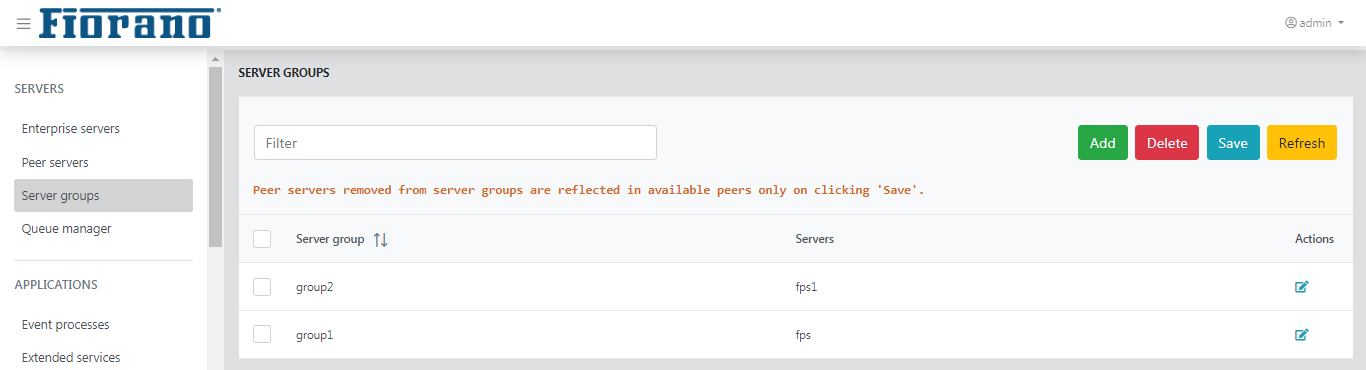
Figure 18: Server groups page with the details of default server groups
After making any change, ensure to click the Save button to apply the change made.
Adding a new server group
By default, the Server Group group1 will have the fps server and group2 will have fps1. To add a new Server Group, perform the following actions:
- Click the Add button, type the name of the new server group to be added and click the Add button that is on the right side of the name entered; the group gets added to the list.
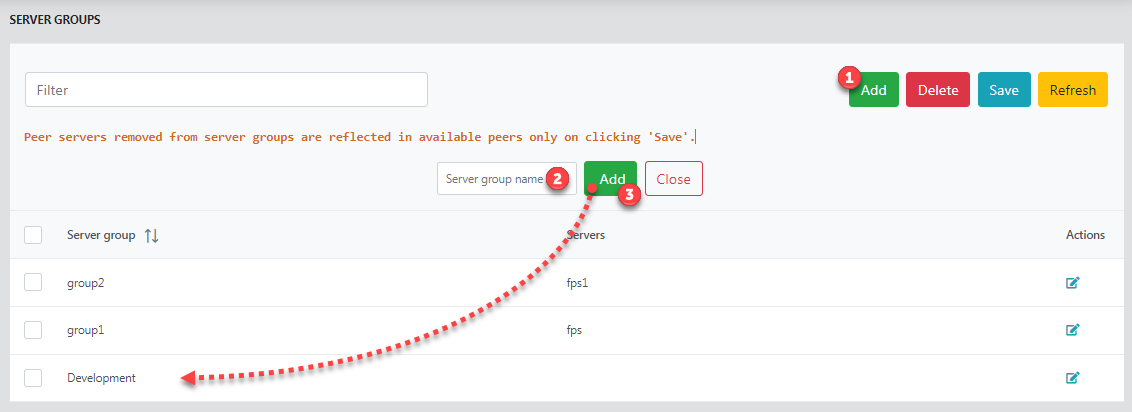
Figure 19: Adding a new server group In the newly added group, click the Edit button under the Action column to add servers.
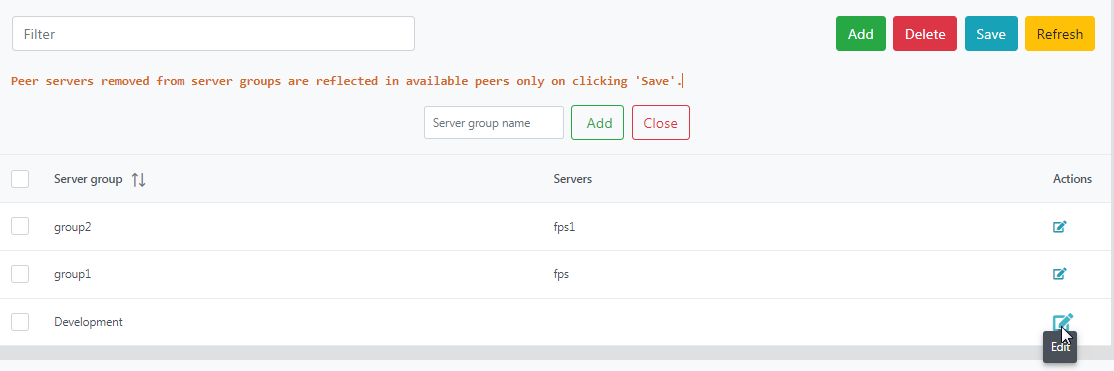
Figure 20: Edit servers option to add/remove serversSelect a server from the Available peers section and click the left arrow button to move the server to the Server in <Group Name> section.
For illustration purpose, fps and fps1 servers were moved (not mentioned in the steps) from group1 and group2 to be used for the new server group.
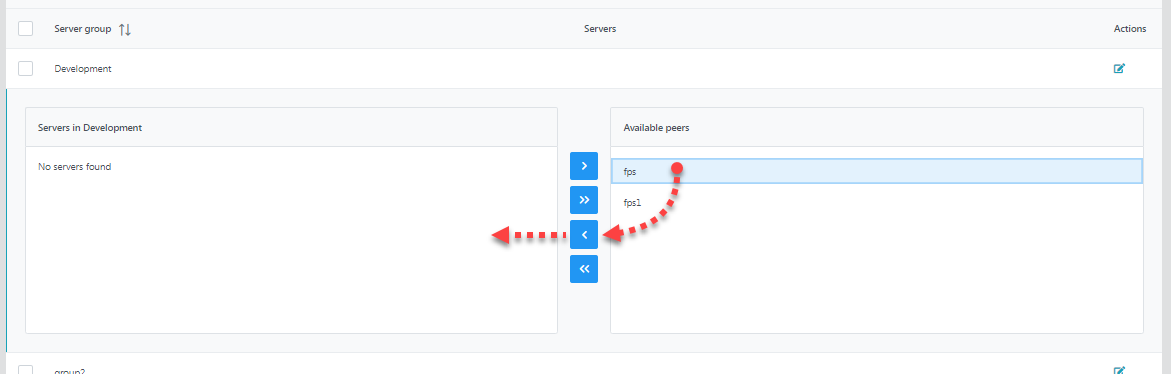
Figure 21: Adding servers to a new server groupMove as many servers as needed/available and click the Save button.
Use CTRL option to select more than one server at a time and use the button showing two arrows to move.
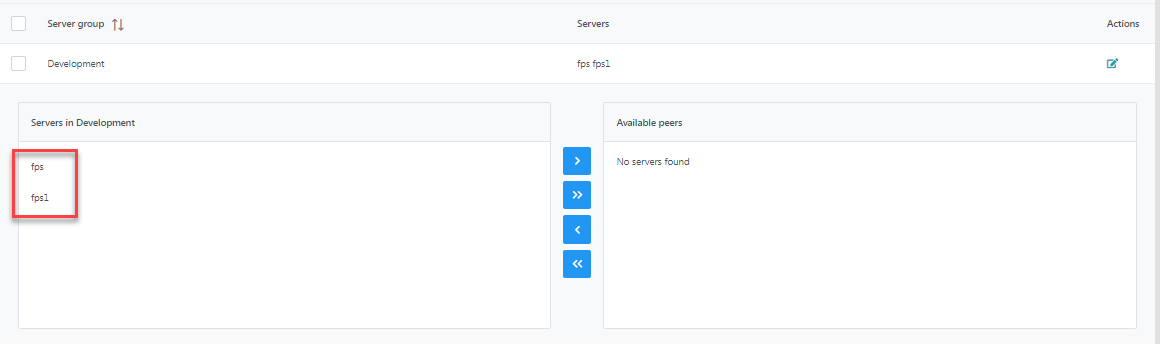
Figure 22: Servers added from the Available peers sectionClick the Refresh button to hide the editing windows. The new group with multiple servers will be displayed.
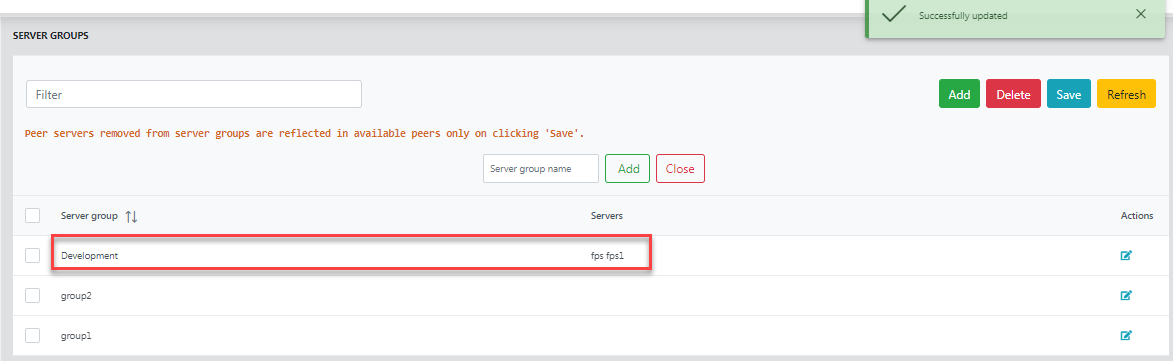
Figure 23: The new server group with the added serversThe same will be reflected in eStudio (after restarting the enterprise server) as well:
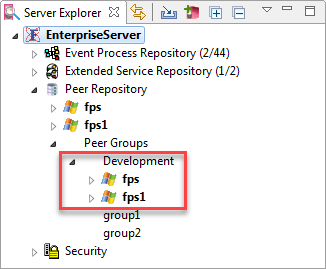
To delete a group, select the group and click the Delete button. If servers are attached to the group while it is being deleted, those servers will be free from the group after deleting and can be used by other groups.
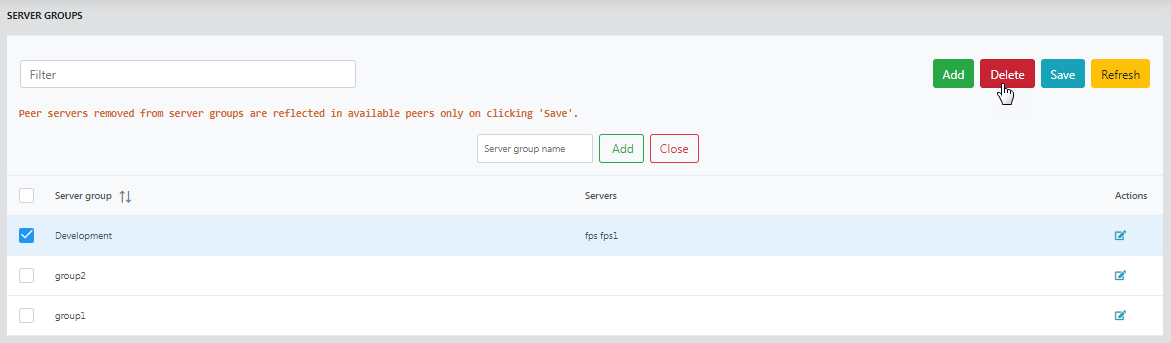
Figure 19: Deleting a server group
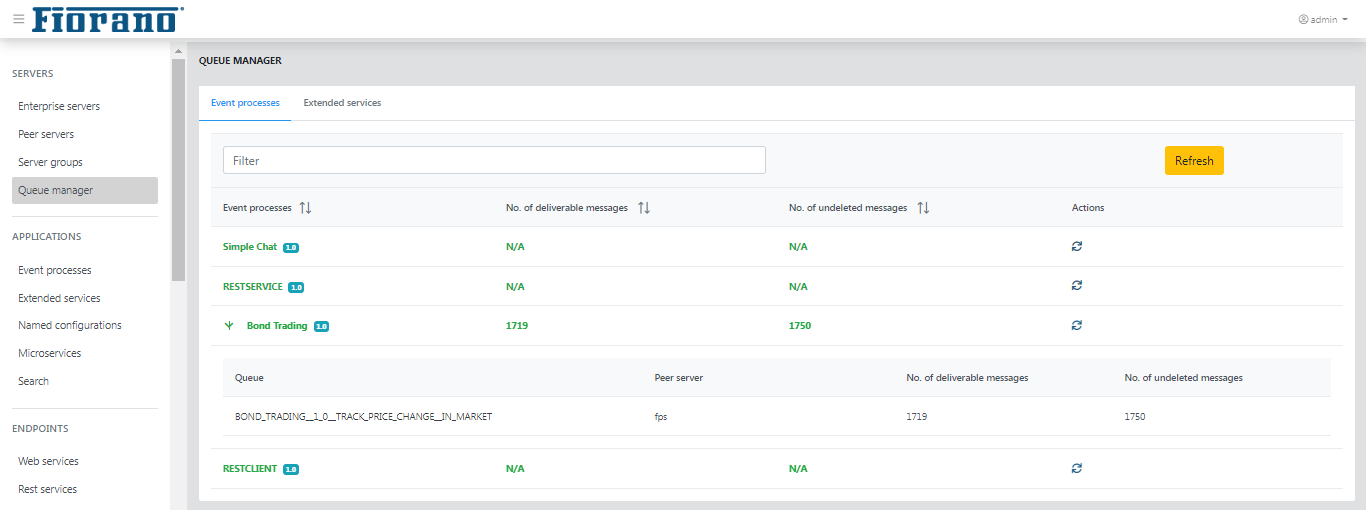
Queue Manager
Queue Manager provides a single view to see all the pending messages in Event Processes that are running. Click the Fetch messages count icon to see the number of delivered messages and number of undelivered messages.

Expand to view the queue details such as event process name and peer server.
Applications
This section shows the details of the event processes running on the Fiorano Peer Server, helps to import applications and also to monitor performance.
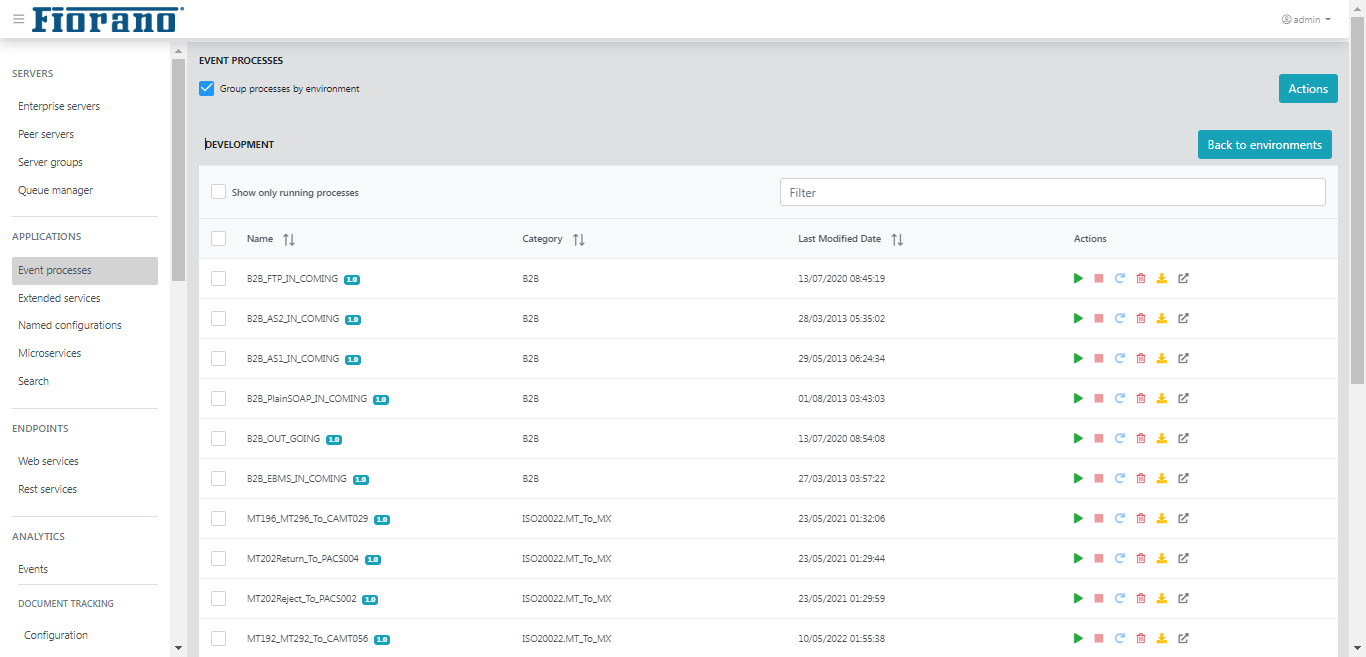
Event Processes
The page shows the list of event processes saved in the Fiorano Server.
Options in the Actions column provide capabilities to launch, stop, restart, delete, and download an event process. Likewise, the Action button does it for multiple event processes; that will be explained in the Actions option section below.
- Use the Filter option to trace a particular event process in the list.
- The number of items displayed in the list can be managed by changing the number in the bottom drop-down, 20 being the minimum and 100 the maximum number of records.
Group process by environment
Selecting this option lists the number of event processes present and running, which are segregated based on the environment.
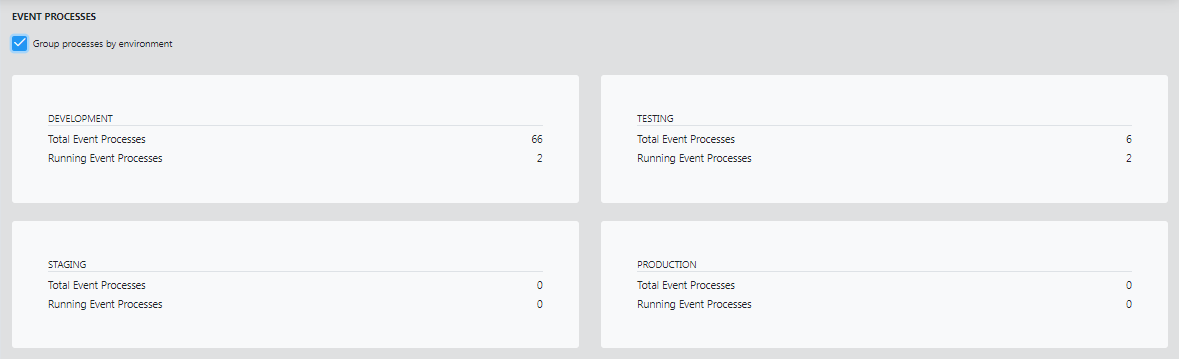
Click the particular environment to list the event processes in that environment.
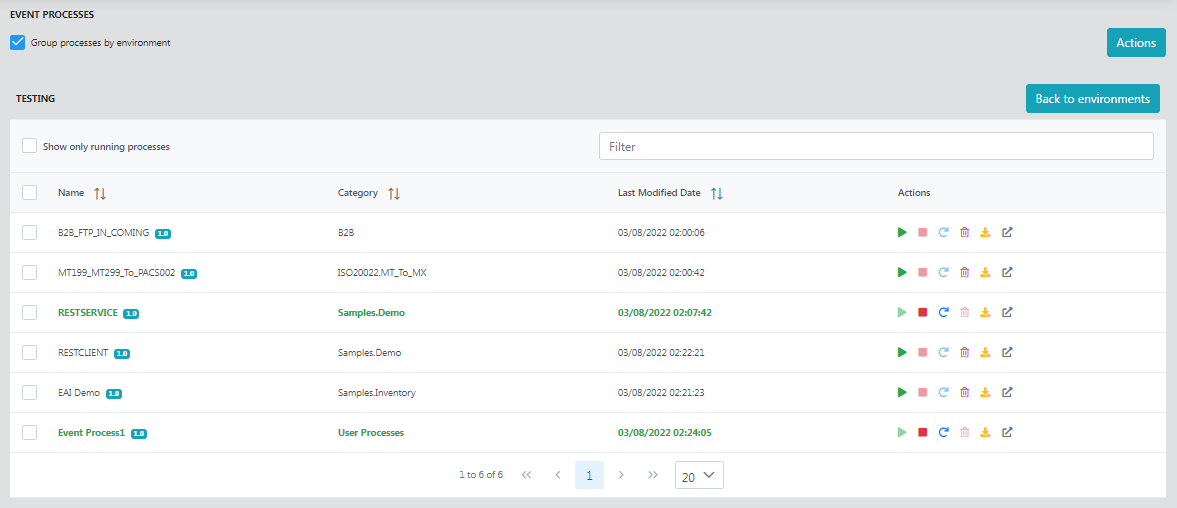
Show only running processes
Click this option to display only the list of processes that are running.
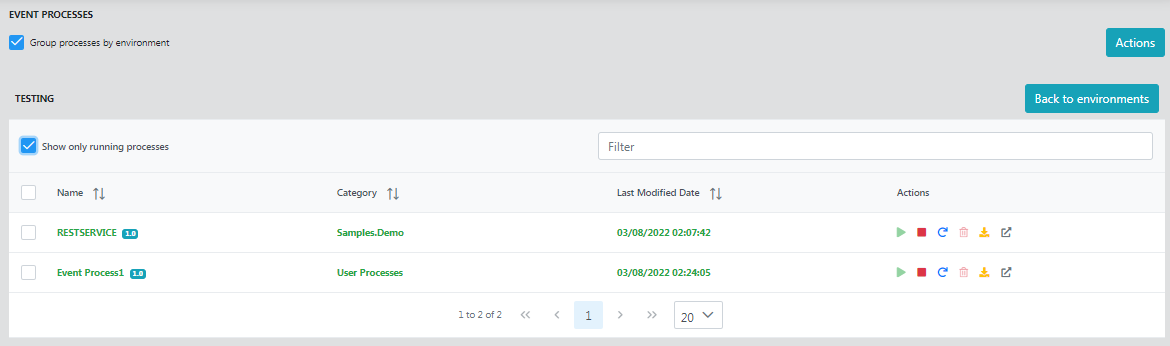
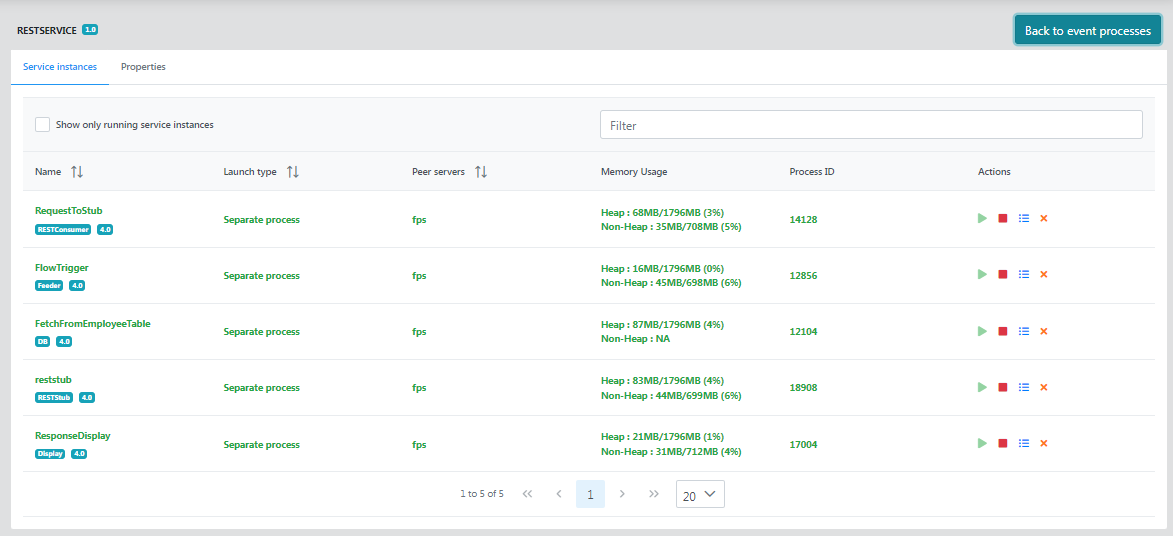
Click the Details link of an event process to list those Service Instances that are part of the event process.
Service Instances
The details page shows services instances that are part of the selected event process the name, launch type, and peer server name.
Options in the Actions column provide capabilities to stop a running service and start a stopped one. It also has options to view and delete output and error logs.
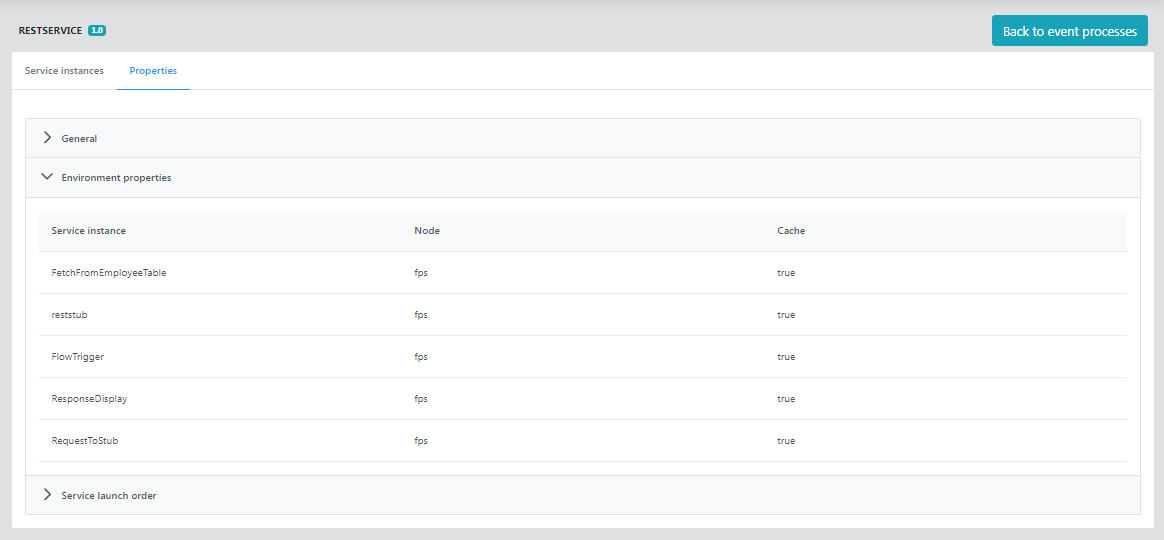
Properties
Displays Event Process properties as configured in eStudio such as General, Environment properties, and Service launch order.
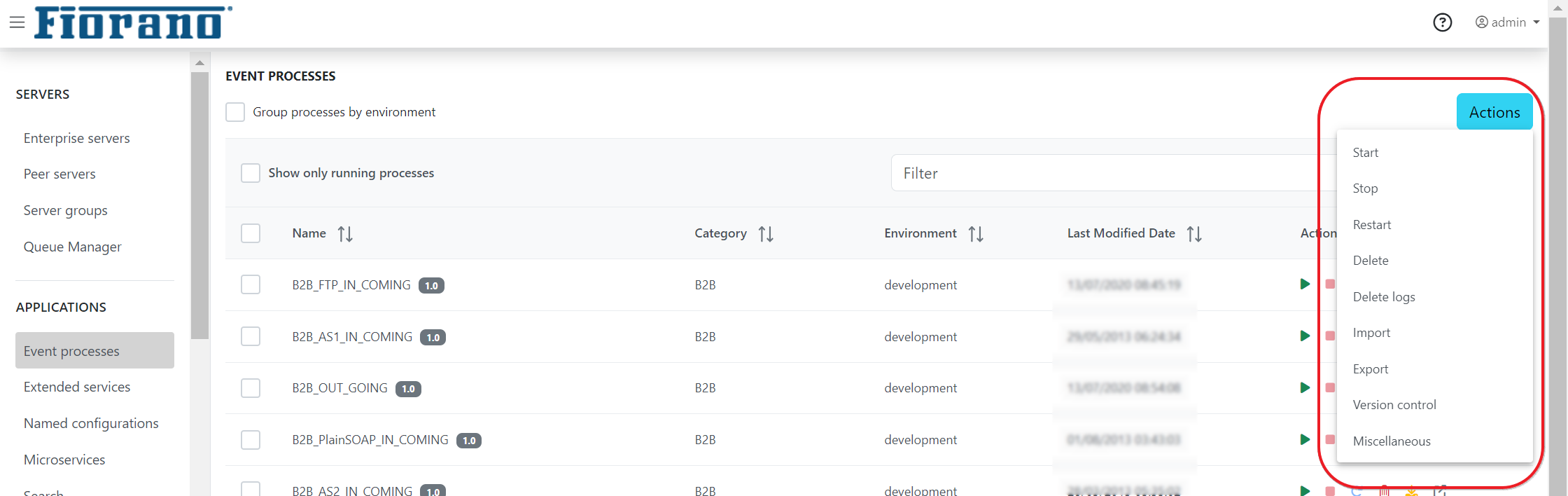
Actions option
As mentioned in the Event Processes section, there are options to launch, stop, restart, delete and download under the Actions column of each event process. Likewise, to perform these actions for multiple event processes, use the Actions button.
Actions button
- To download multiple EPs, use the Export option.
- The Delete logs option clears the logs.
Other Action elements
The options Import, Version Control, and Miscellaneous (Launch order and Scheduler) are explained in the following sections.
Importing an event process
Import option helps to import an event process or multiple event processes which are exported/downloaded or saved as a Zip file in a particular location.
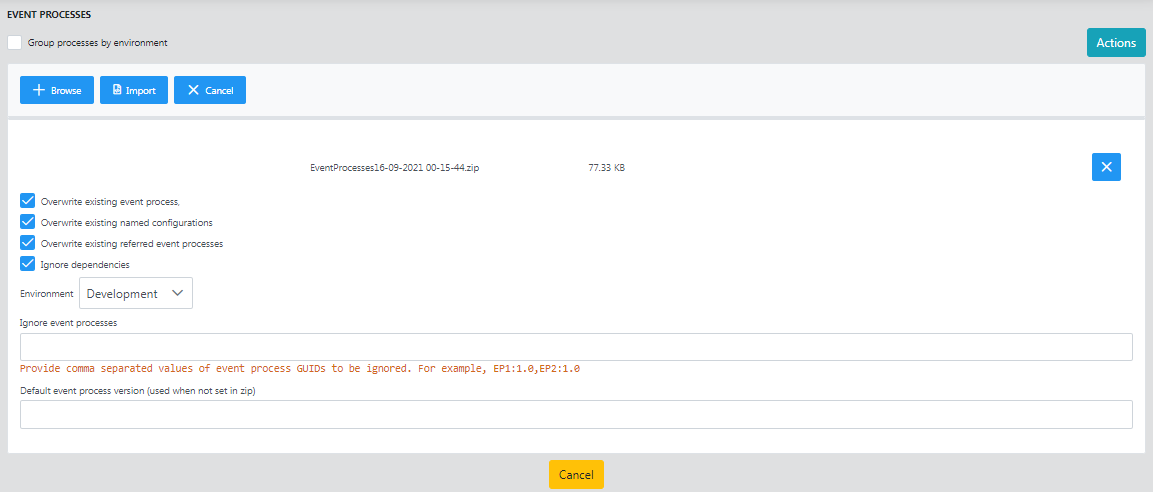
To import, click the Browse button to select the Zip file, provide the following details, and click Import.
| Property | Description |
| Overwrite existing event process |
|
| Overwrite existing named configurations |
|
| Overwrite existing referred event processes |
|
| Ignore Dependencies |
|
| Environment | Choose the environment to which the event process needs to be imported; options being Development, Testing, Staging, and Production. |
| Ignore event processes | In a ZIP file with multiple EPs, specify the comma-separated names of the EPs that need not be imported along with the other EPs in the file. Example From the zip file which contains multiple EP's — EP1, EP2, EP3, and EP4, to import only EP1 and EP3, specify the EP names to be excluded while importing, that is, EP2 and EP4. Format for comma-separated EPs
CODE
|
| Default application Version (used when not set in zip) | Specify a version number if a version number was not set in the zip file. |
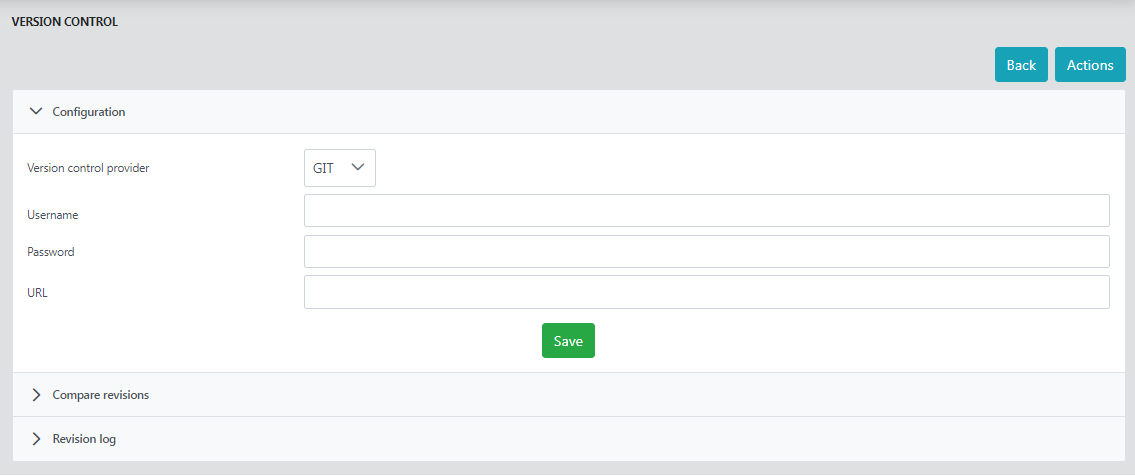
Version Control
This feature enables version control Integration for Event Processes. It helps in configuring GIT, comparing revisions and viewing revision logs in the GIT version control repository.
The Actions button provides options to Clone, Checkout, Update and Commit.
Configuration
Username and Password are the version control username and password. The URL string is the remote URL location to perform push, pull or checkout of the commits from eStudio or API management dashboard.
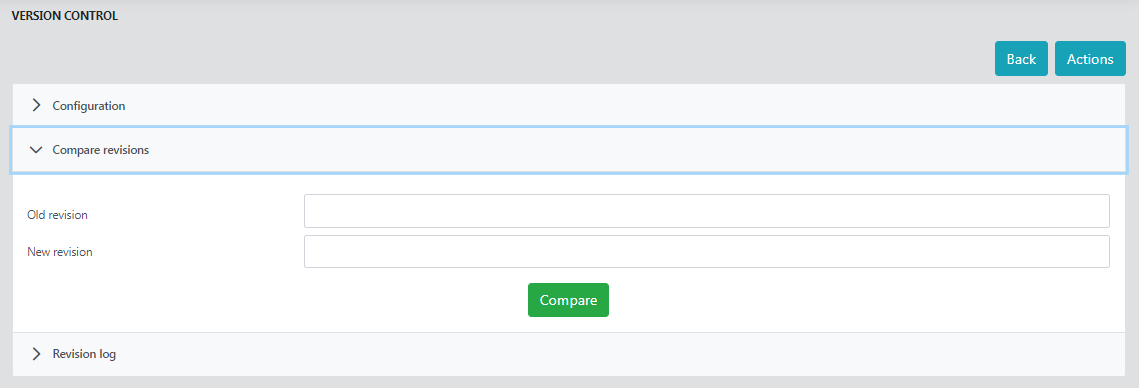
Compare revisions
Compares the files modified/added/deleted between any two commits in the applications directory.
To compare, provide the old and the new revision numbers and click Compare.
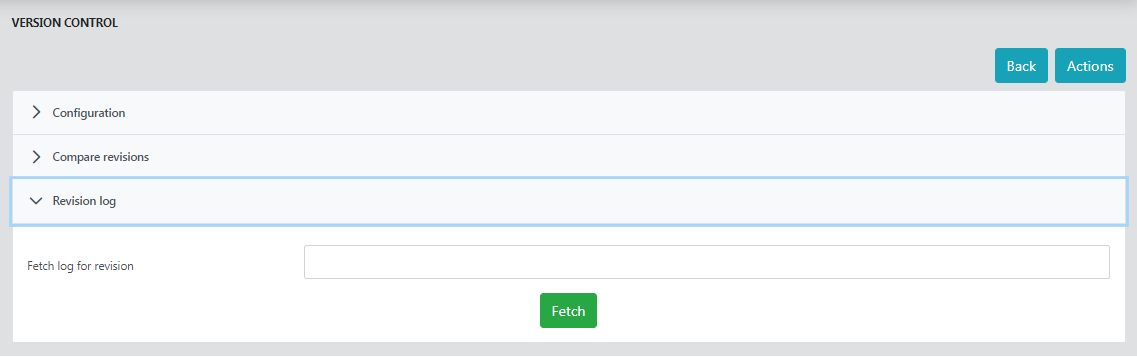
Revision log
To list all the files pushed from the applications directory to remote repository during a particular commit, use the Revision log option.
Provide the revision number which gets printed on the server console after every successful push and click Fetch.
Miscellaneous
Launch order
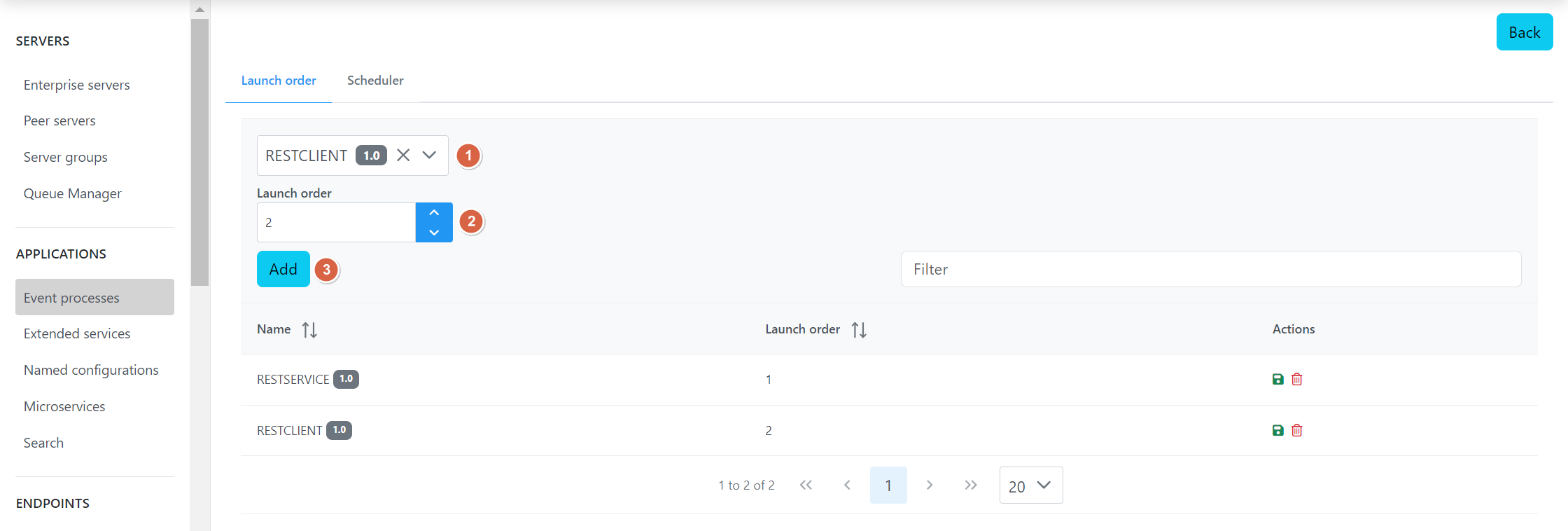
Launch order can be set for applications by providing against each application that represents the order of execution. When the Enterprise Server starts or restarts, each application launches in the order specified.
The Launch order settings apply to those applications that are already running.
Adding Applications to Configure Launch Order
To add applications to assign launch order, select the application, and specify the number based on the order that is required.
After the enterprise server restart, check the order of execution at EnterpriseServer > Peer Repository > fps > View Logs after the server restart.
Duplication of launch order is possible - two or three applications can have the same sequencial number.
Example
If two applications in a group of applications need to have a start time and end time respectively (assume it as 1 and 3) and the rest of the applications that need to work together can have any launch order, those applications can have the same number (retain 2 for the other applications).
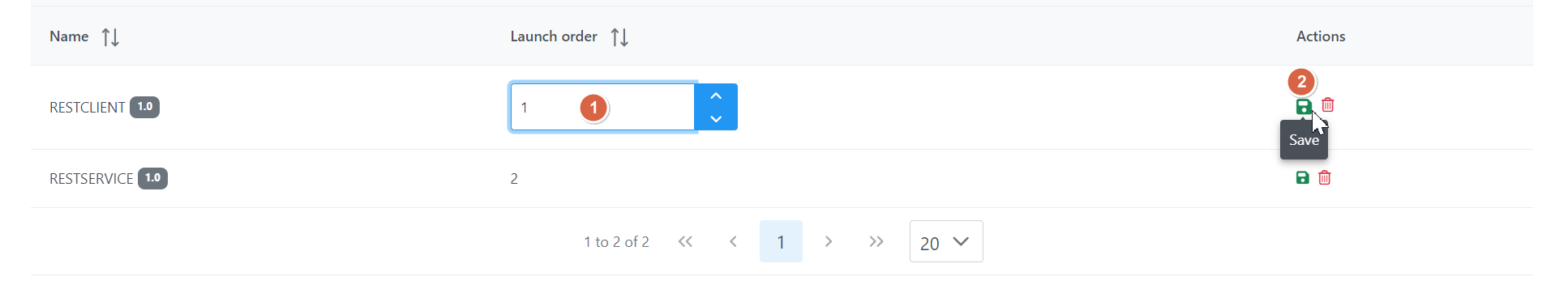
Editing the Launch Order
To edit the launch order that’s already configured, click on the needed cell under the Launch order column and click the Save icon under the Actions column.
Scheduler
This helps to schedule an application to start or/and end at a specific time.
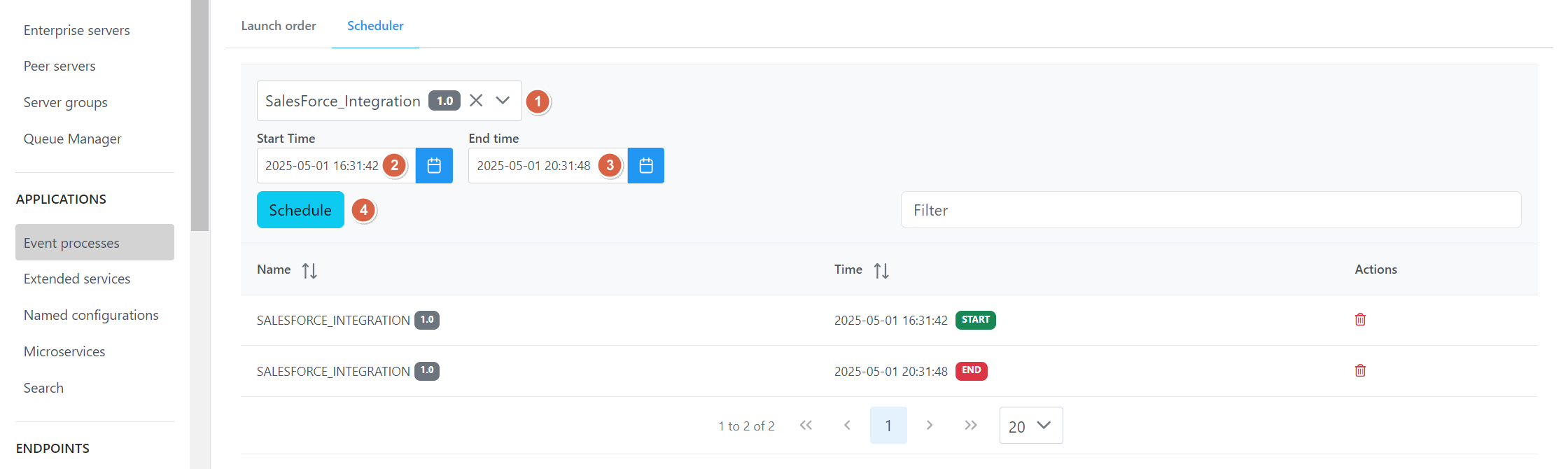
The record saved in the scheduler gets deleted automatically once the end time mentioned is elapsed.
Extended Services
Displays the details of extended services such as name, category, environment, server groups, and last modified date.
The Action column provides the capability to start, stop, restart, delete, and download the service. The Details page gives information about the services present in the event process.
As the options in the Actions button are the same as in the Event processes section, refer to the .
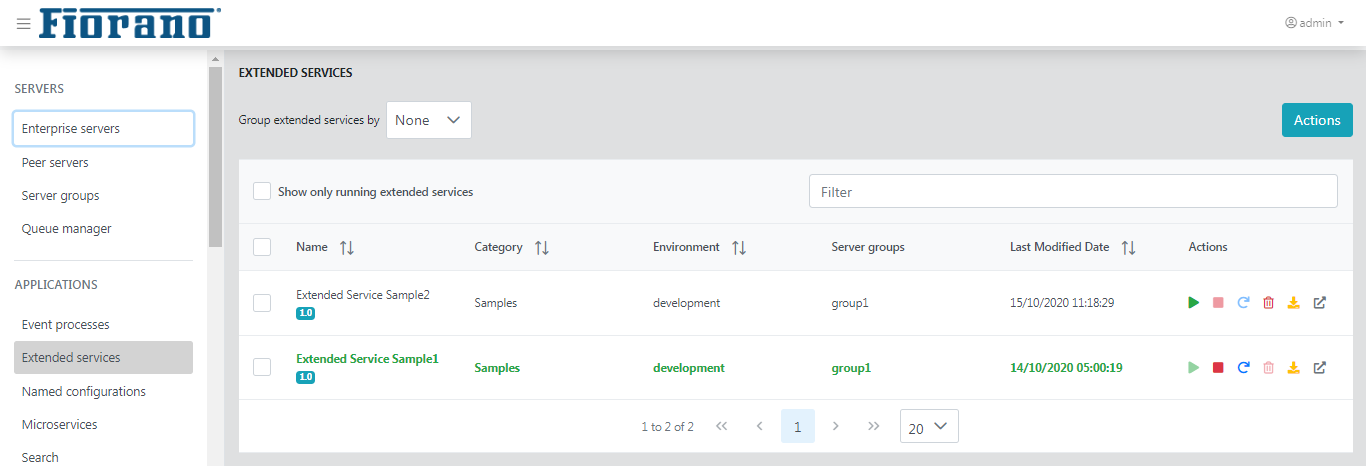
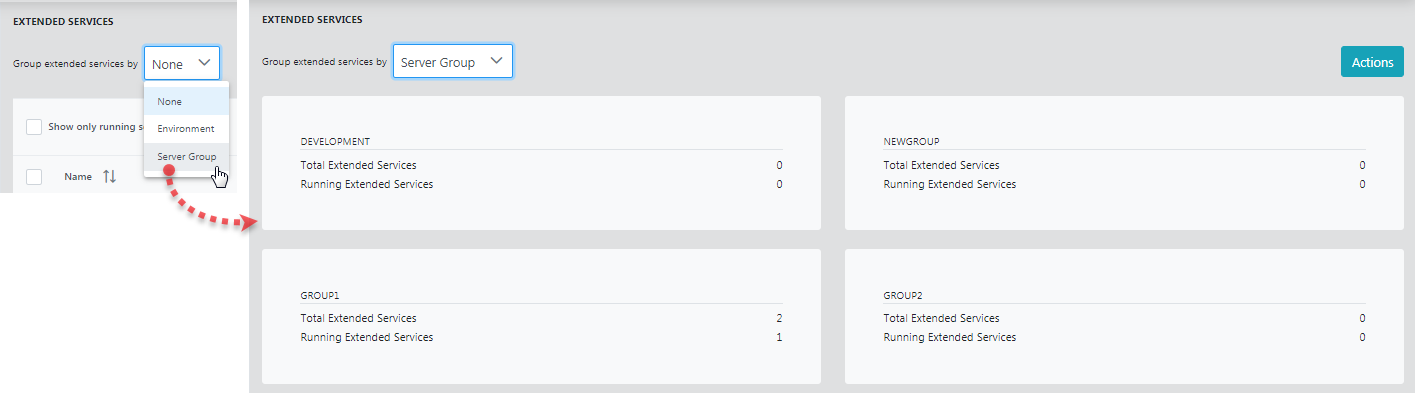
Group by Environment and Server Group
Selecting this option lists the number of event processes present and running, which are segregated based on the environment or server group.
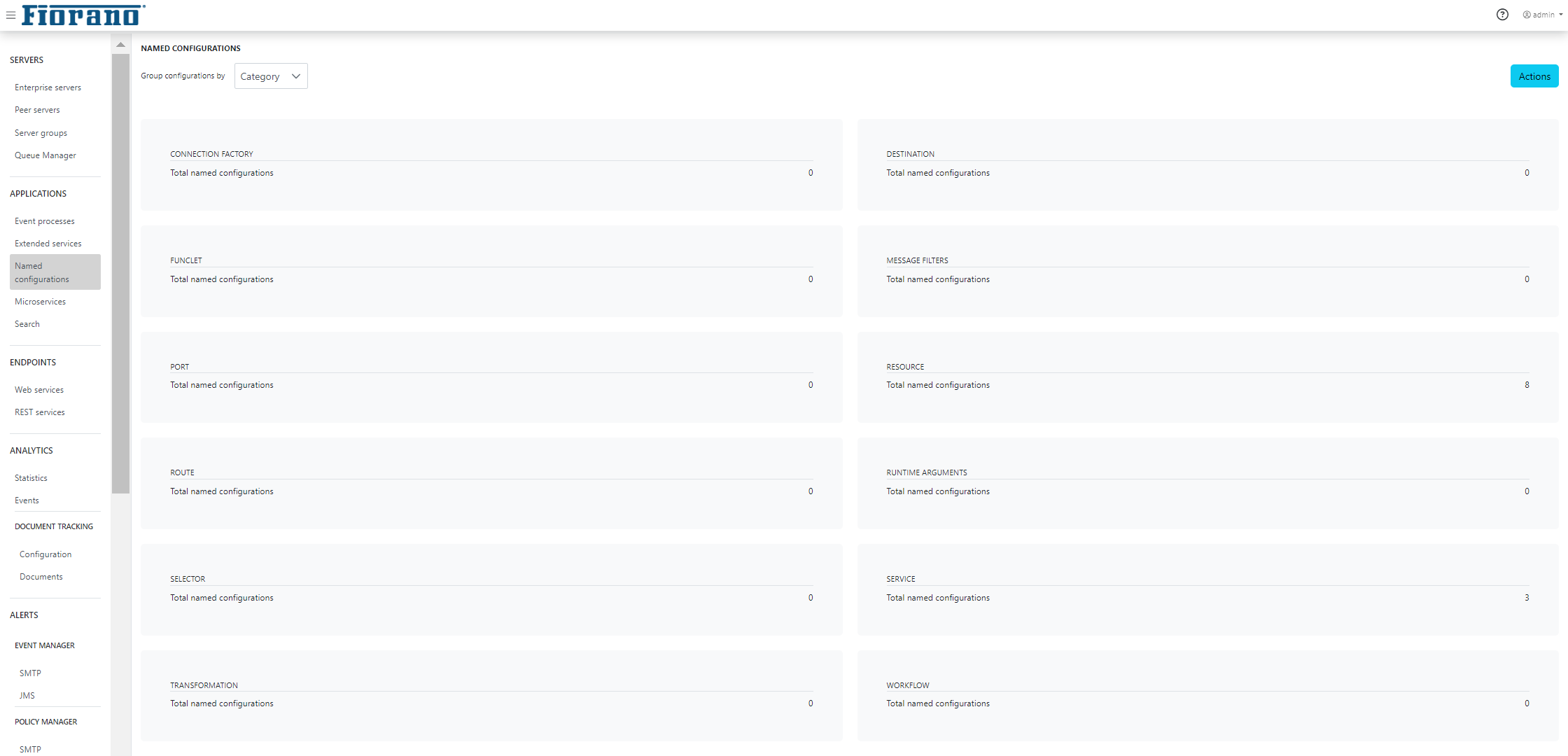
Named configurations
Named Configuration is filetered by Category by default.
It can be filtered by the environment too.
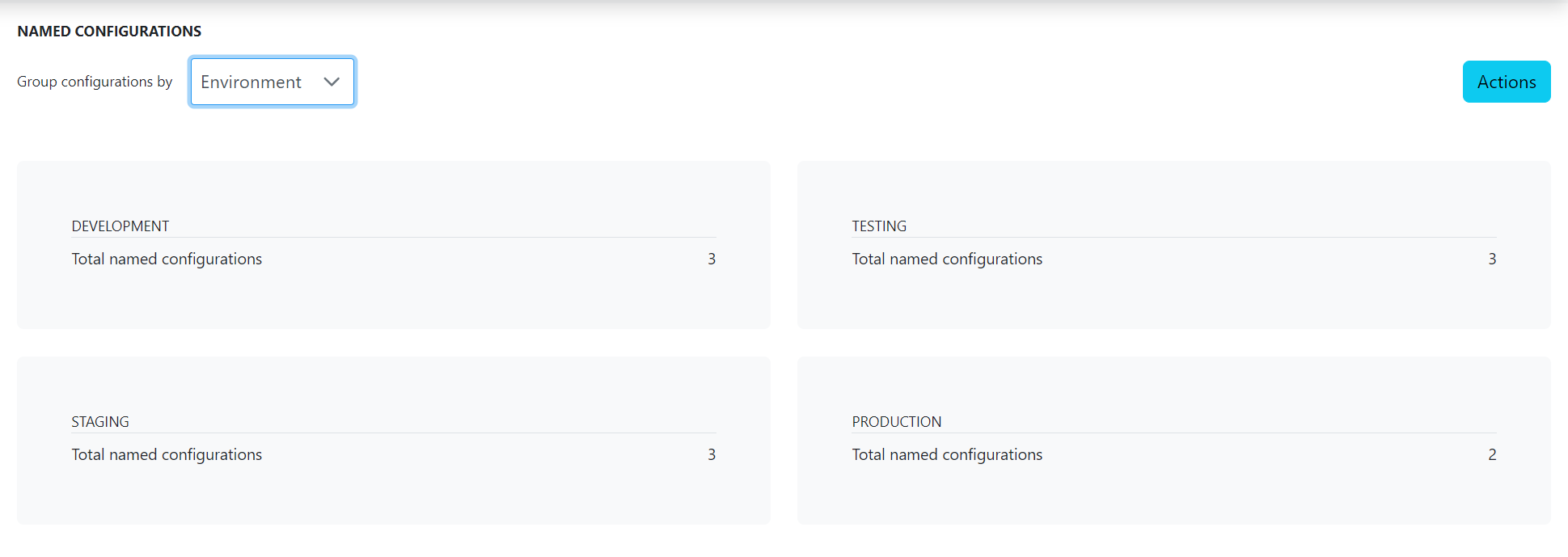
Click the category/environment to see the named configuration details of the respective category/environment.
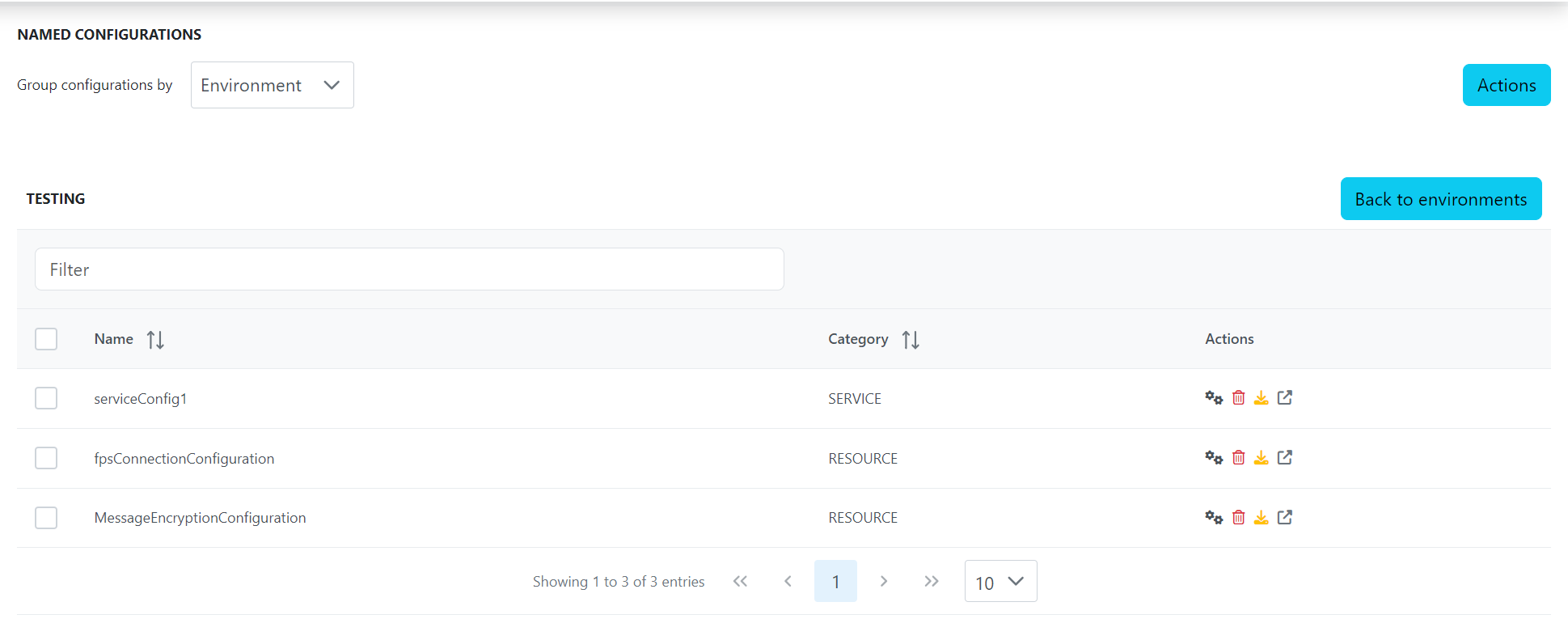
Click the "Fetch usages" icon to see the usage of the respective named configuration element.
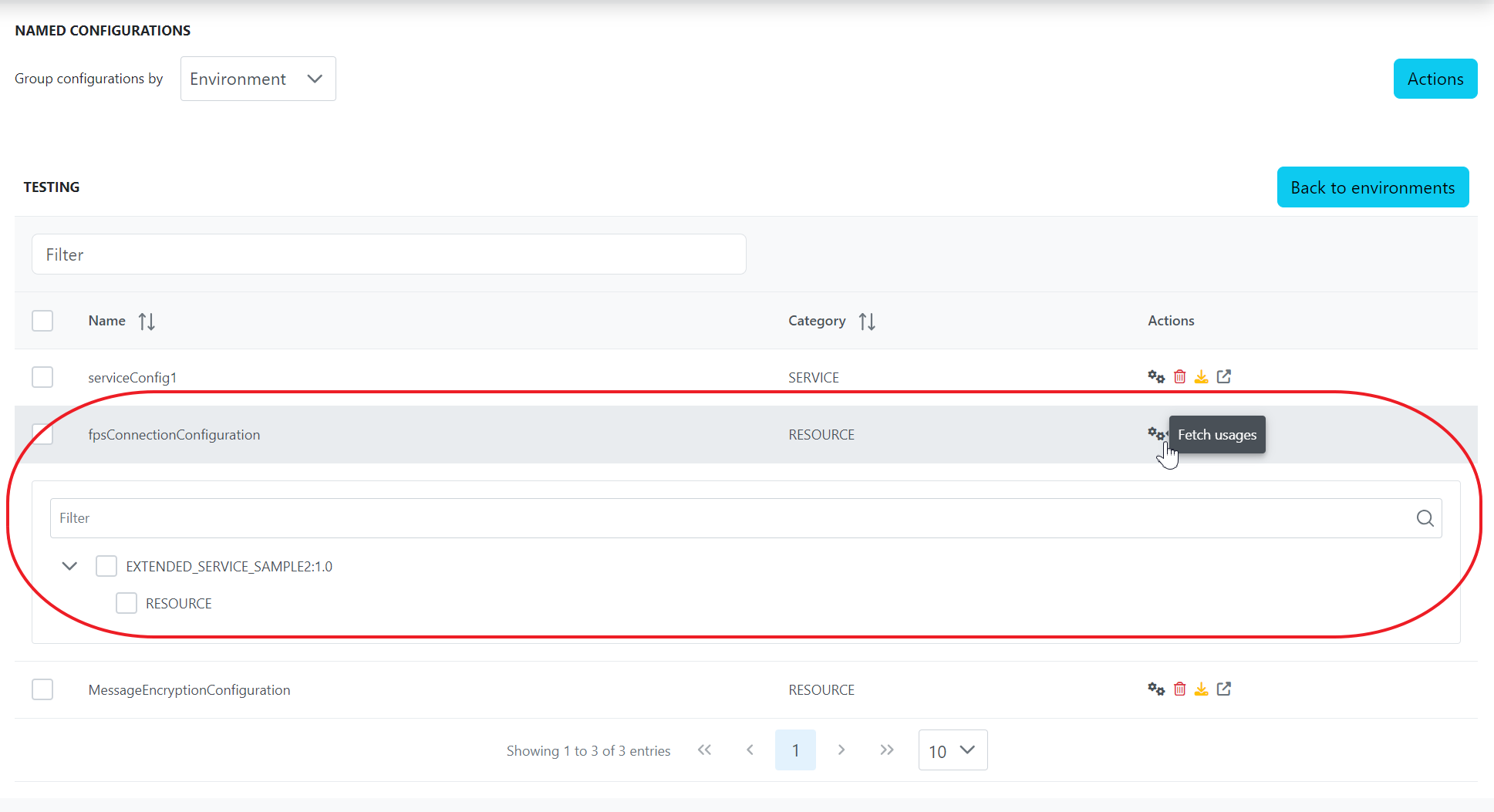
Click the Details icon to see the configuration.
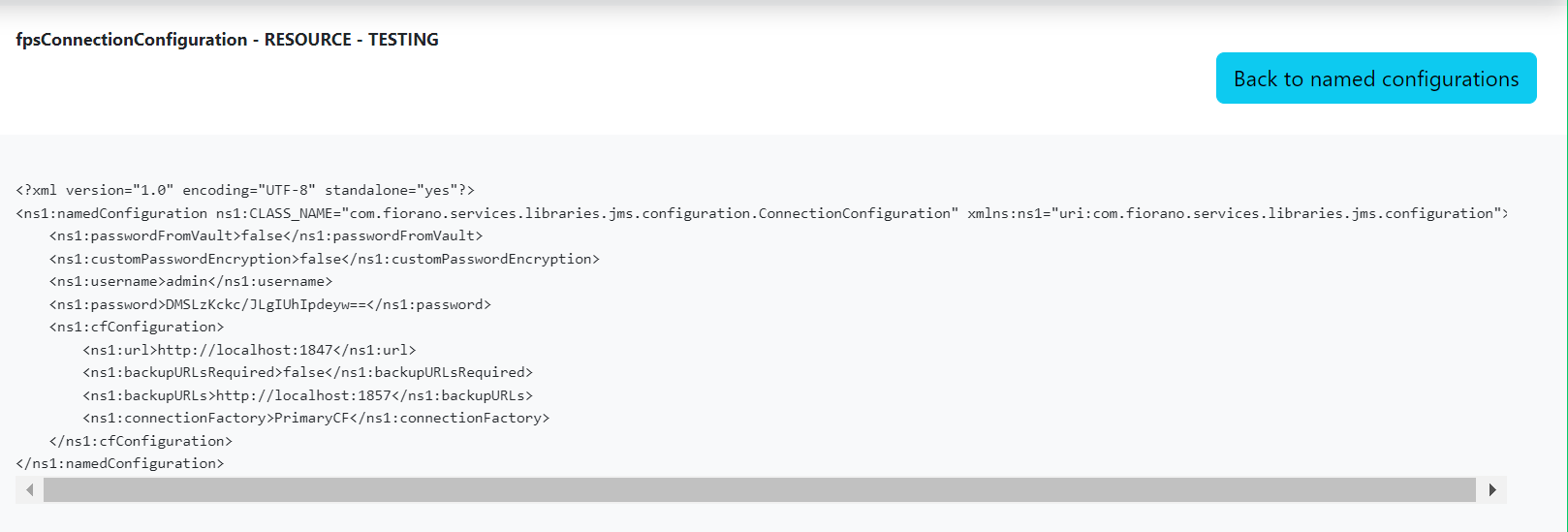
The Actions button provides options to refresh, export, import, delete, version control, and copy.
Refer to the previous sections for details on import and version control options.
Copying to a different environment
A Named Configuration set for one environment can be copied to other environments.
- Click the Actions button and click the Copy configuration option to navigate to the page where copying can be executed.
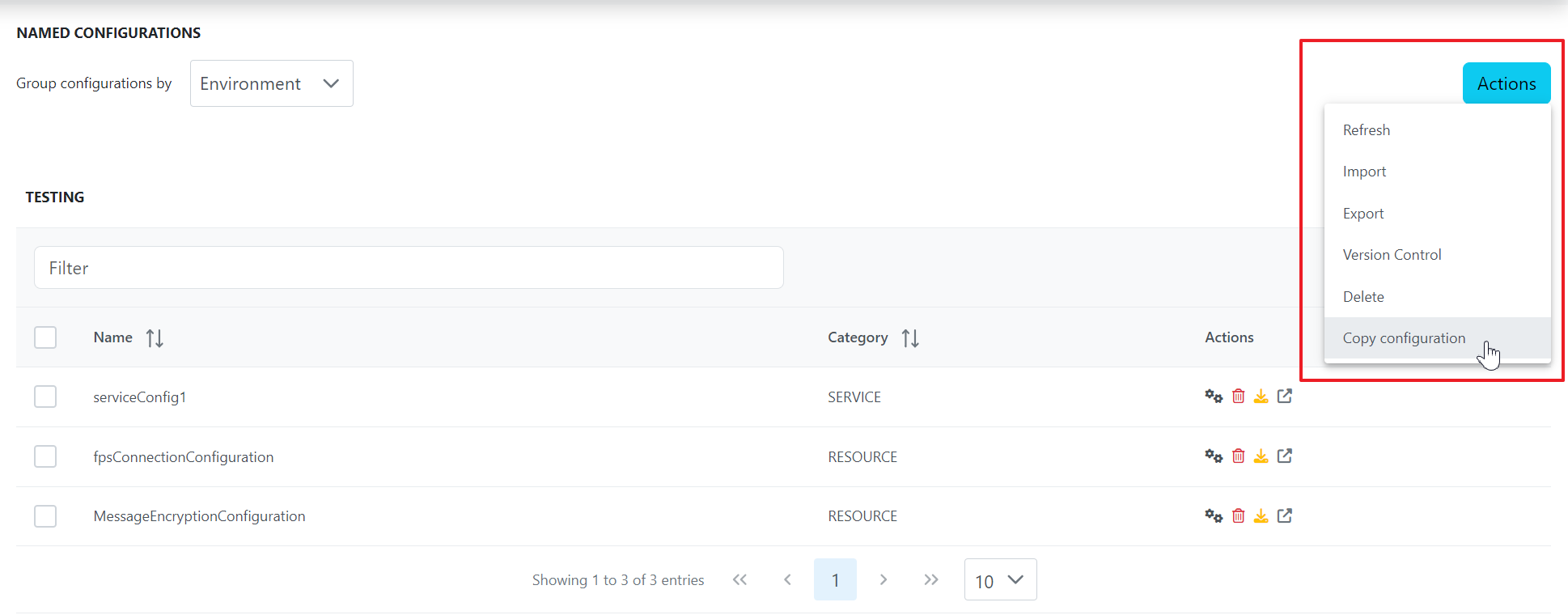
- Select the respective named configuration in the Source environment and click the Copy button to copy the named configuration settings to another environment selected.
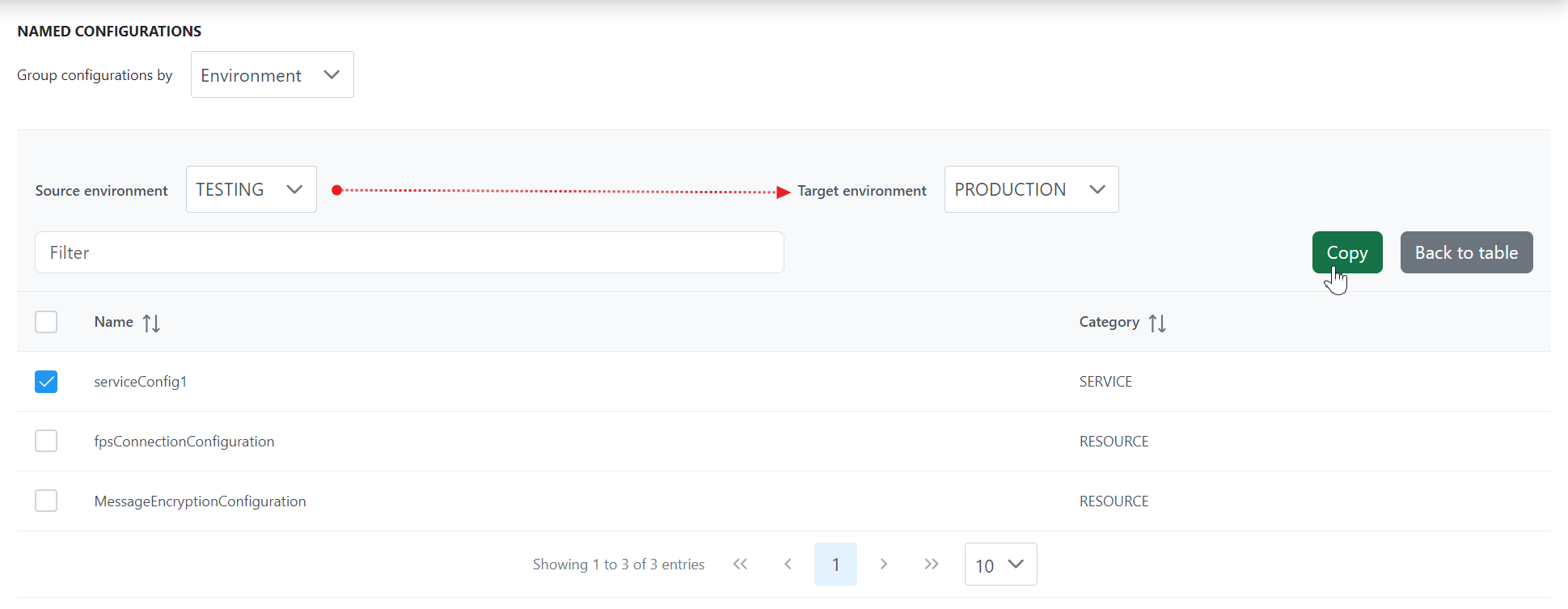
Change the Source environment to the environment to which the configuration element was copied to check whether it's been copied.
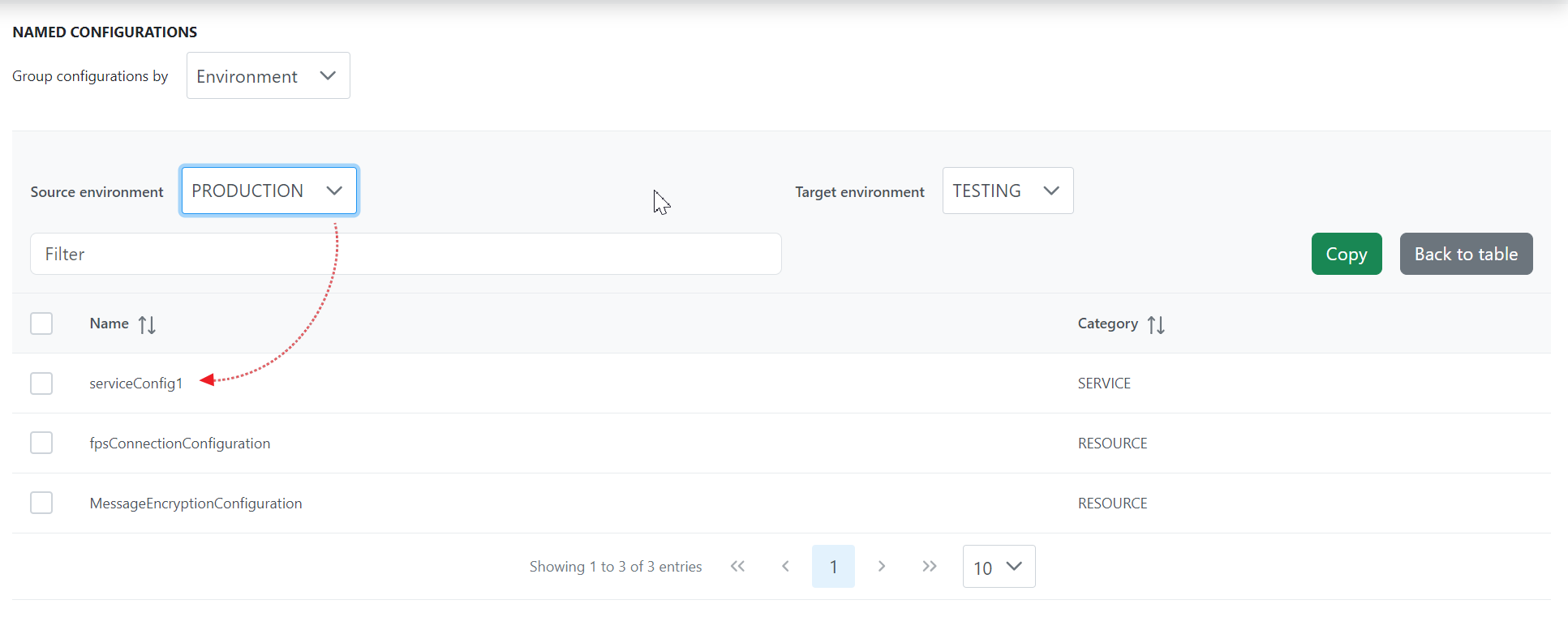
The number of elements in the Production environment has turned to 3 in place of 2 as displayed in the image that refers to filtering based on Environment in one of the previous images.
Microservices
Actions button provides options to refresh, export, import, and delete microservices.
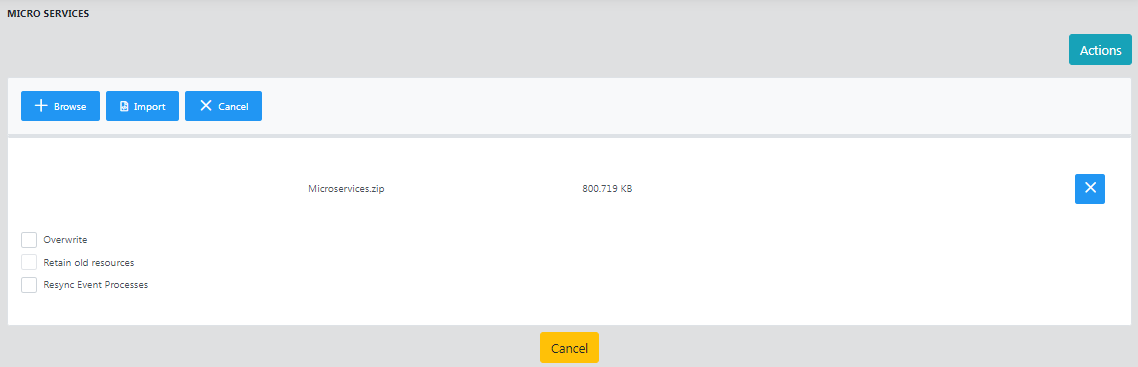
Import
Import option under the Actions button helps to import a microservice or multiple microservices which are exported/downloaded or saved as a Zip file in a particular location. Options available for importing microservices are:
- Overwrite: Replaces the microservice(s) with the one that exists in the repository with all properties and resources of the importing microservice.
Retain old resources: Overwrites the microservice retaining the resources (jars, property files etc.) present in the old microservice in the repository.
This option works only when the Overwrite option is enabled.
Resync Event Processes: If the importing microservice is part of an event process that is running, this option helps to re-synchronize and apply the modifications to the running event process.
If this option is enabled, there is no need to click Synchronize Application option in eStudio.
Filter Option
- Use filter search box to fetch a particular microservice that needs to be managed.
- One or more microservices can be selected to download (export) or delete.
Details option to customize microservices
Click the Details icon present at the end of each service instance under the microservices to go to the Service Descriptor options where a microservice can be customized in various ways.
After making a change, ensure to click the Save button to apply the changes.
Refer to the Services eStudio section to understand the usage of each option in these sections.
Overview
The information used to identify the service is shown under the Overview section. The user can change the name and descriptions of the microservice in this section.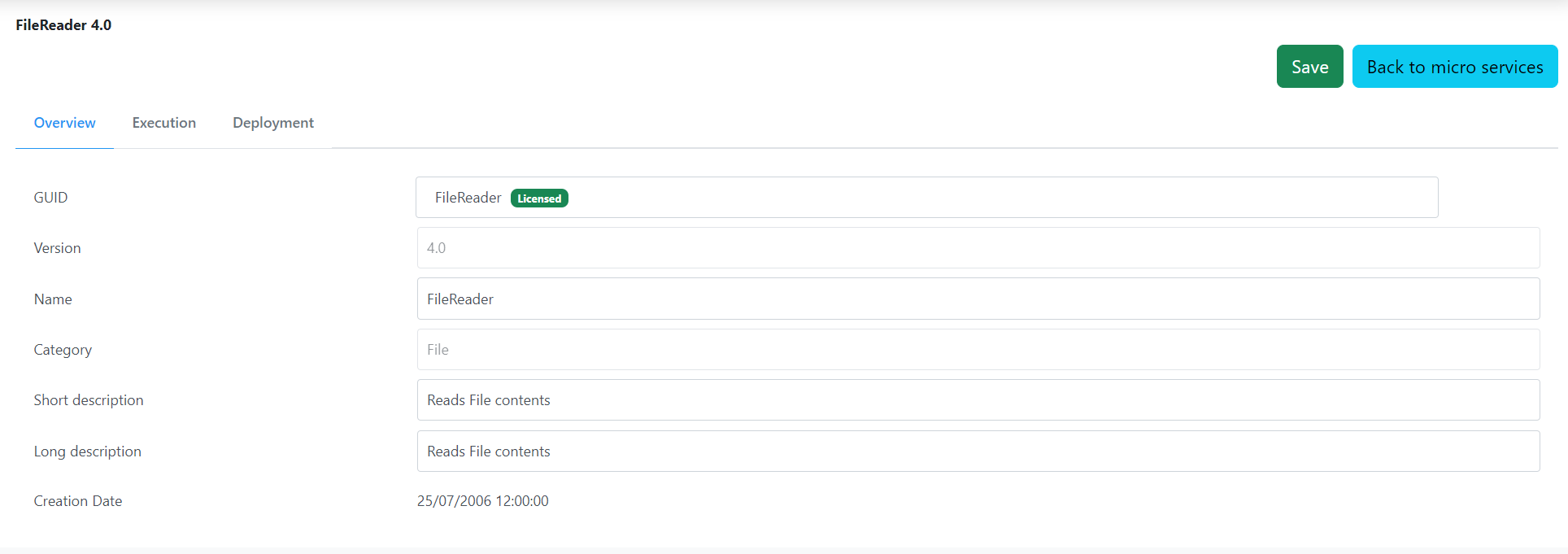
Execution
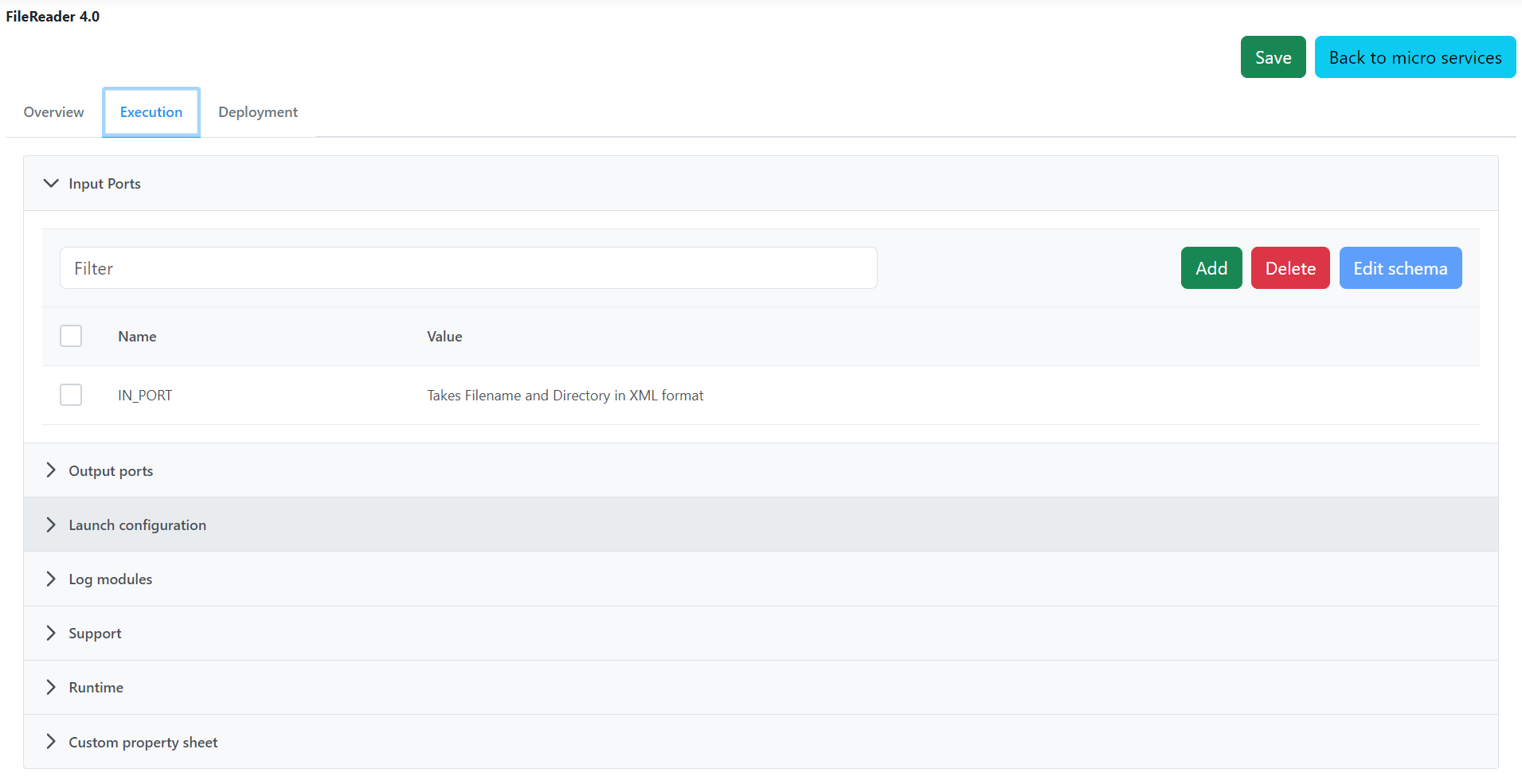
Deployment
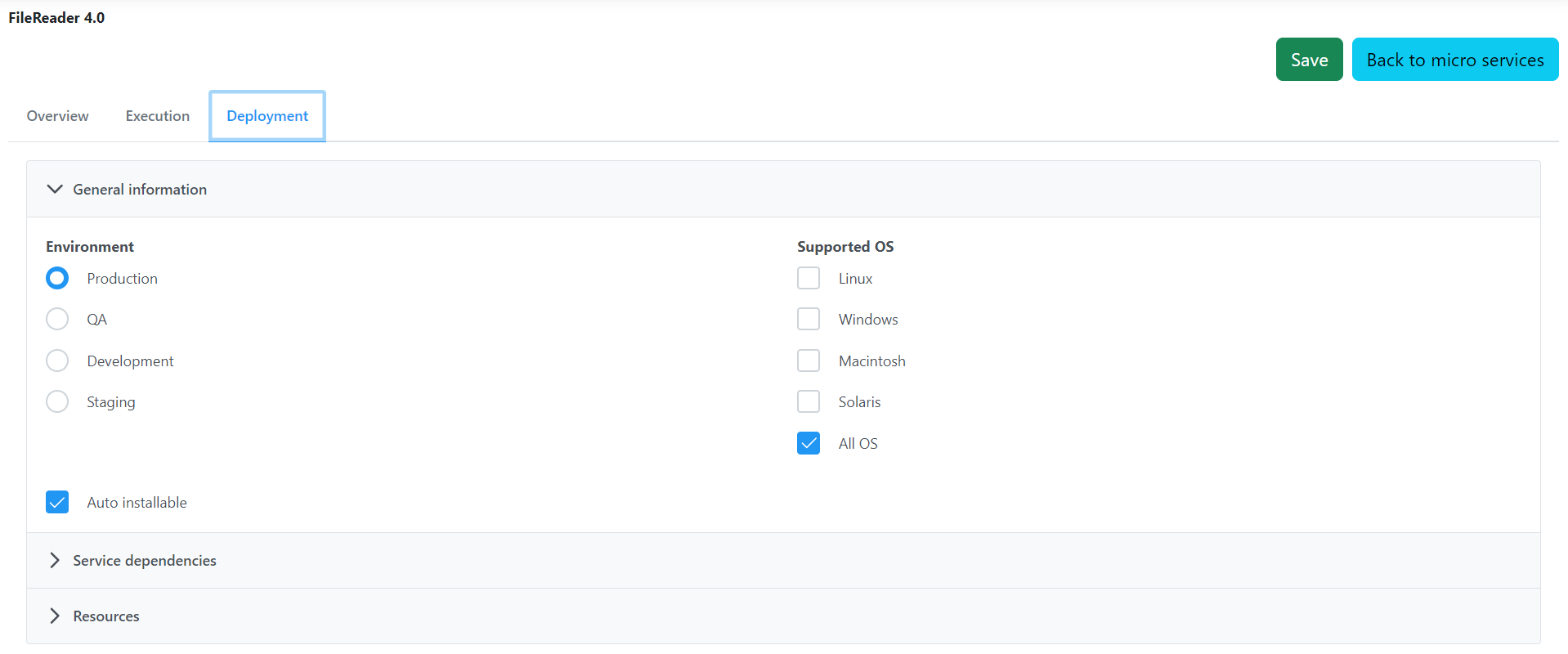
Adding a resource
To add an additional resource, perform the following actions:
Click the Add button to open the panel to add a resource.
Click the Browse button and choose the file from the respective location.
To save and add the resource to the list of resources, click the Import button.
After adding a resource and after removing a resource by clicking the Remove button, clicking the Save button is not required to apply the change made.
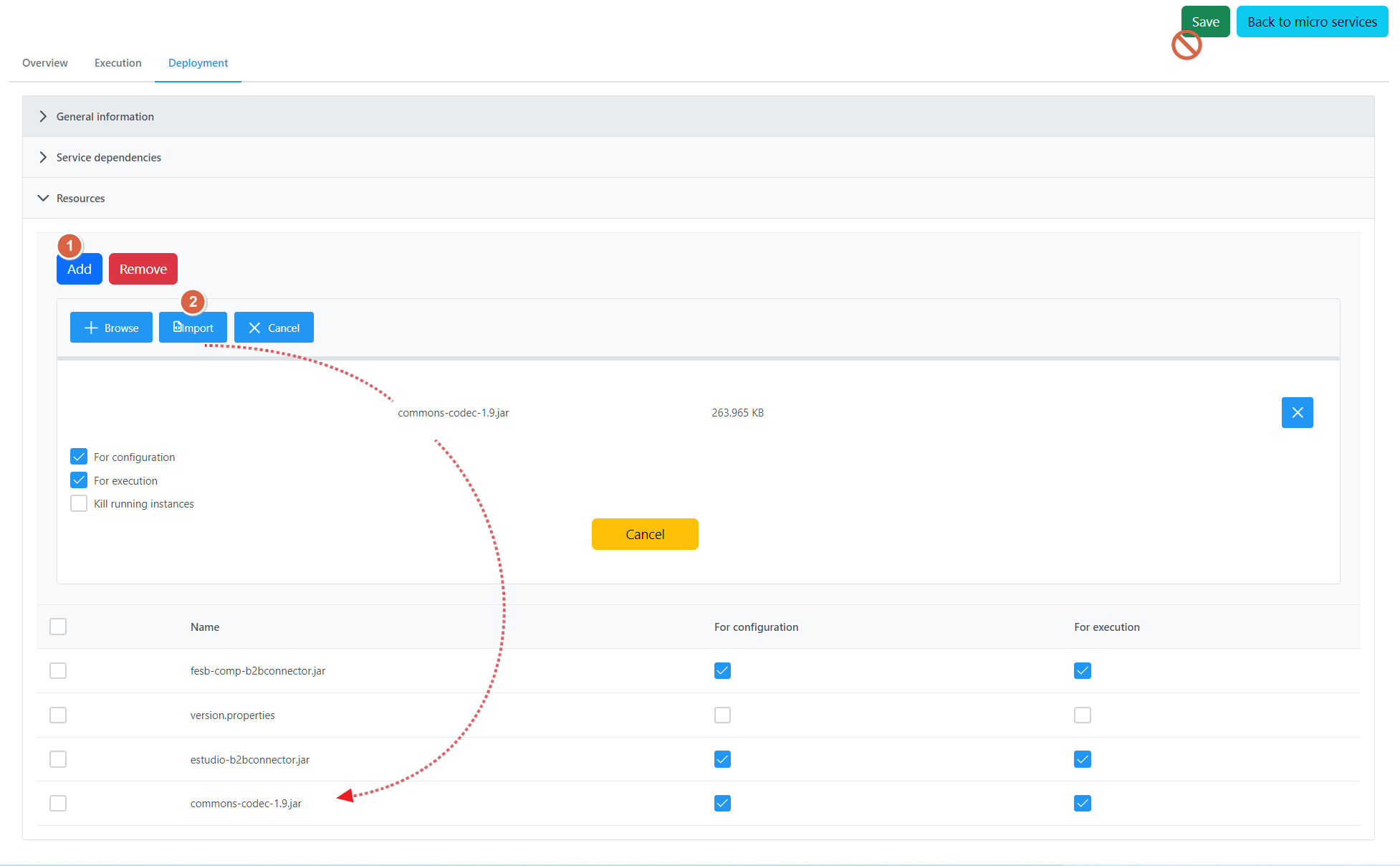
Click the Close button to hide the panel to add resources.
Search
This section provides the capability to search for resources that are configured to be used by event processes, which can be performed on three different levels:
- Applications View
- Microservices View
- Resources View
Figure 57: Searching configured resources based on application view
In all three options, use the drop-down to select the application/microservice/resource in resources that need to be searched for.
In the filter bar,
- multiple applications can be selected.
- application can be filtered using keyword
Click the Clear button to clear the searched data and perform a new search at any point.
Applications
The Applications page shows details such as applications (name), category, microservice GUID, and microservice instance.
Click a row to display the resource names and values in different environments.
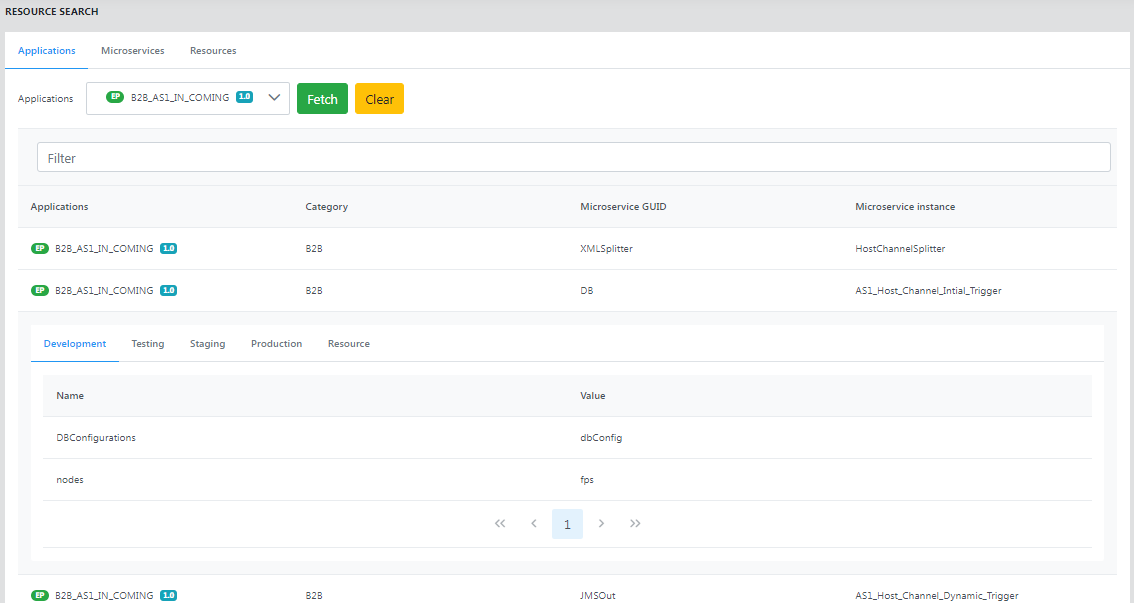
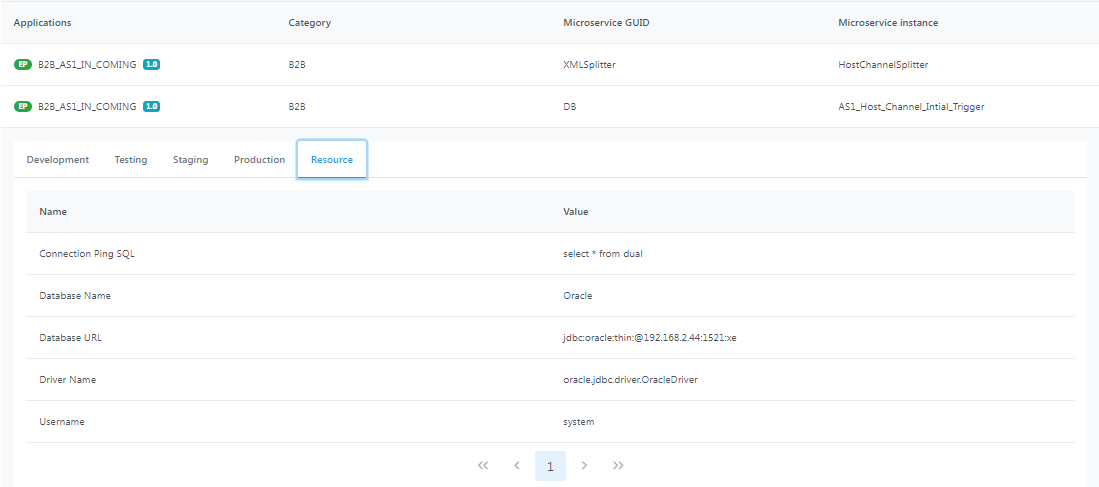
Click the Resource tab under the specific application to see more details about the resources in it and the corresponding values.
Microservices
The Microservices page shows details such as Applications, Category, Microservice GUID, and Microservice instance.
Click a row to display the resource names and values in different environments.
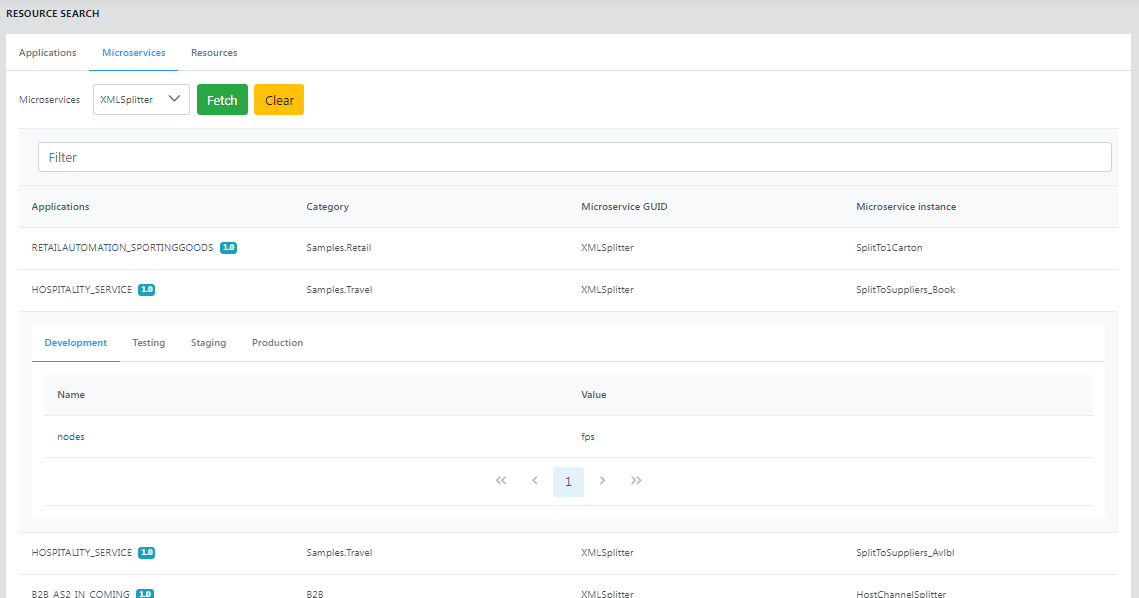
Figure 58: Searching configured resources based on the Microservices view
Resources
The Resources page shows details of the resources such as Value, Environment, Applications, Category, Microservice GUID, and Microservice instance.
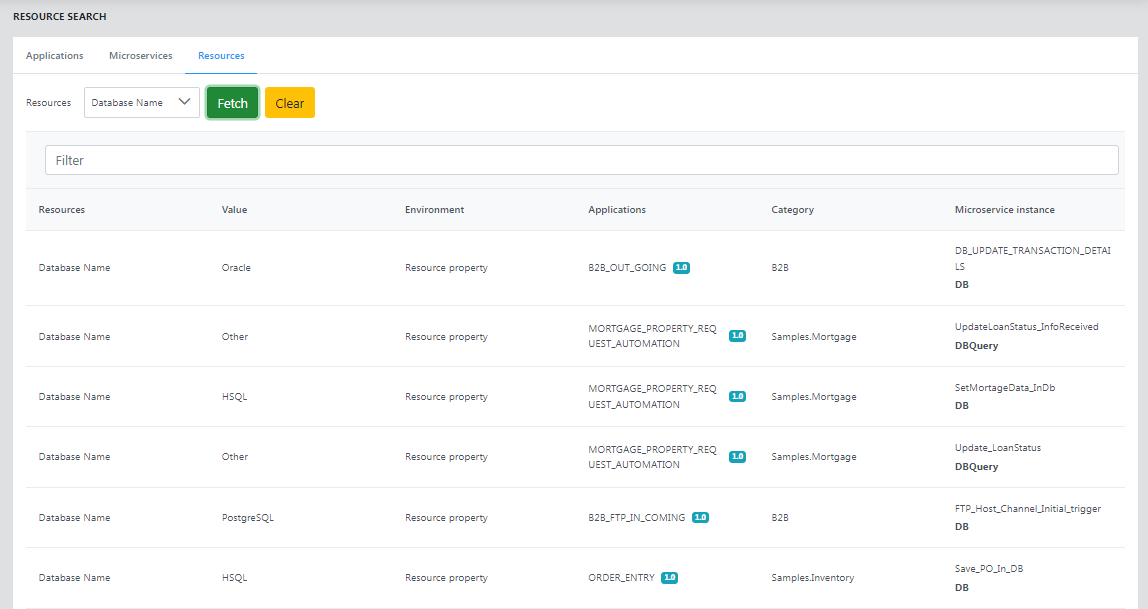
Figure 59: Searching configured resources based on resource view
Endpoints
This section provides details of the event processes deployed as Web Services and RESTful services. You can view the status of web service either online or offline and has the option of enabling or disabling this option. You can also test RESTful deployed from the dashboard.
Web Services
The Rest service event processes will be displayed with details such as service name, endpoint URI, WSDL URL, event process name, Stub name, Node, and Actions.
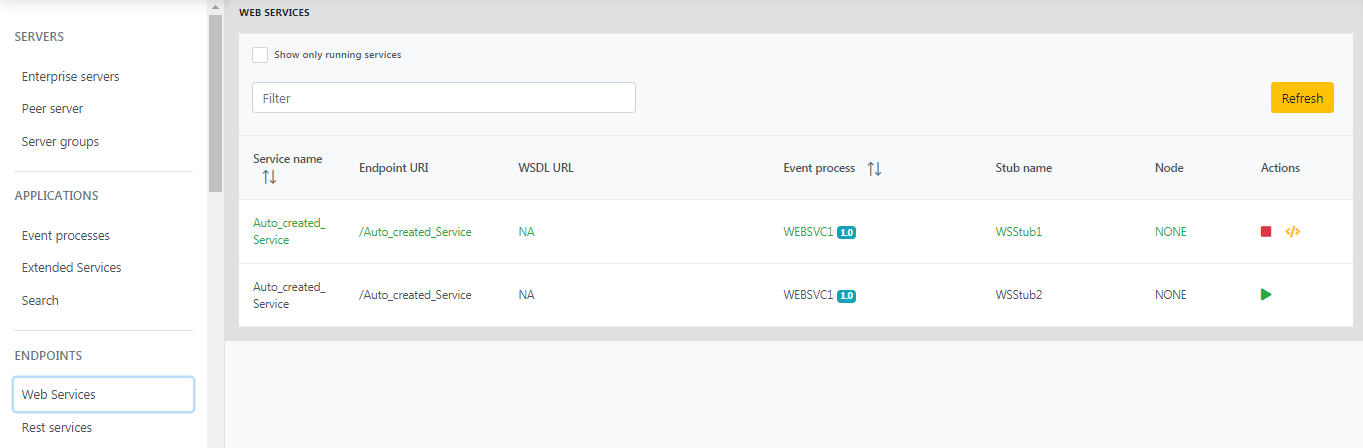
Actions column
The Actions column has the option to start a service. A started service can be stopped using the same icon that switches between start and stop.
Test
Refer to the next section (Rest Services) to learn about the other option under the Actions column - the Test icon to test the service.
Rest services
The Rest service event processes will be displayed with details such as service name, endpoint URI, WADL URL, event process name, Stub name, Node, and Actions.
The Actions column has the option to start a service. A started service can be stopped using the same icon that switches between start and stop.
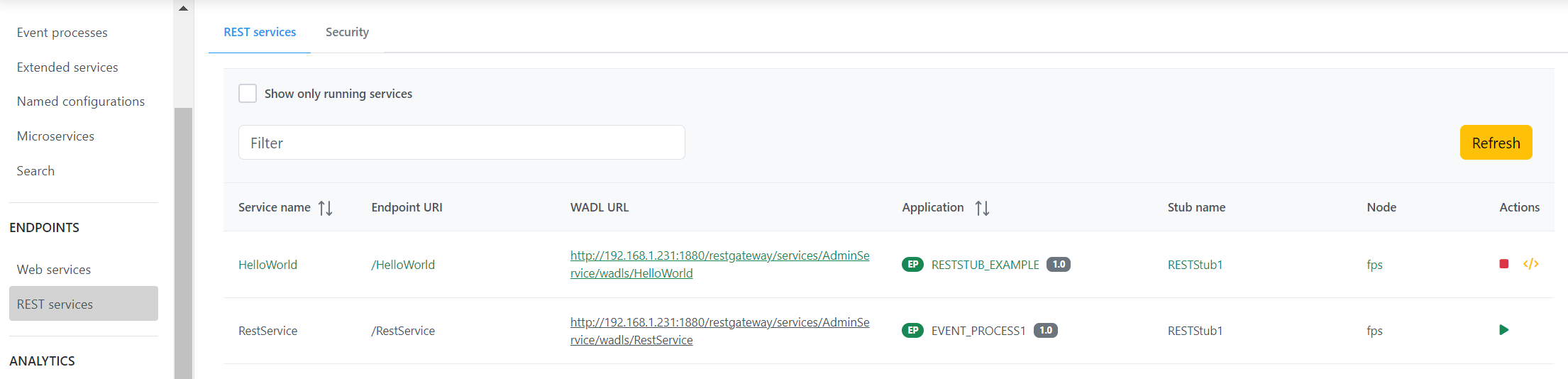
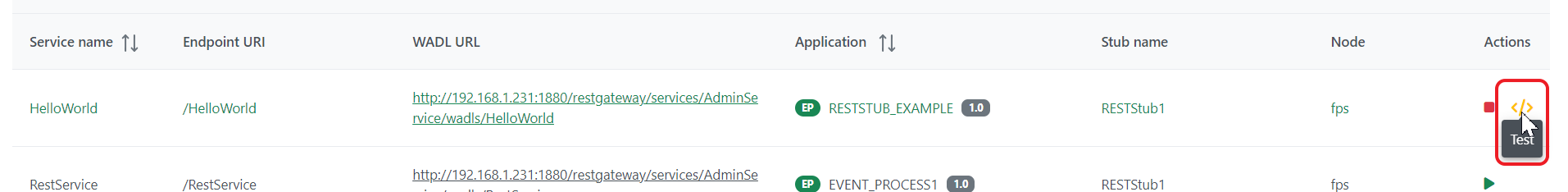
Testing the service
After running a service, perform the following actions to test the service:
- Click the Test icon next to the Stop icon.
Click the Generate resources button
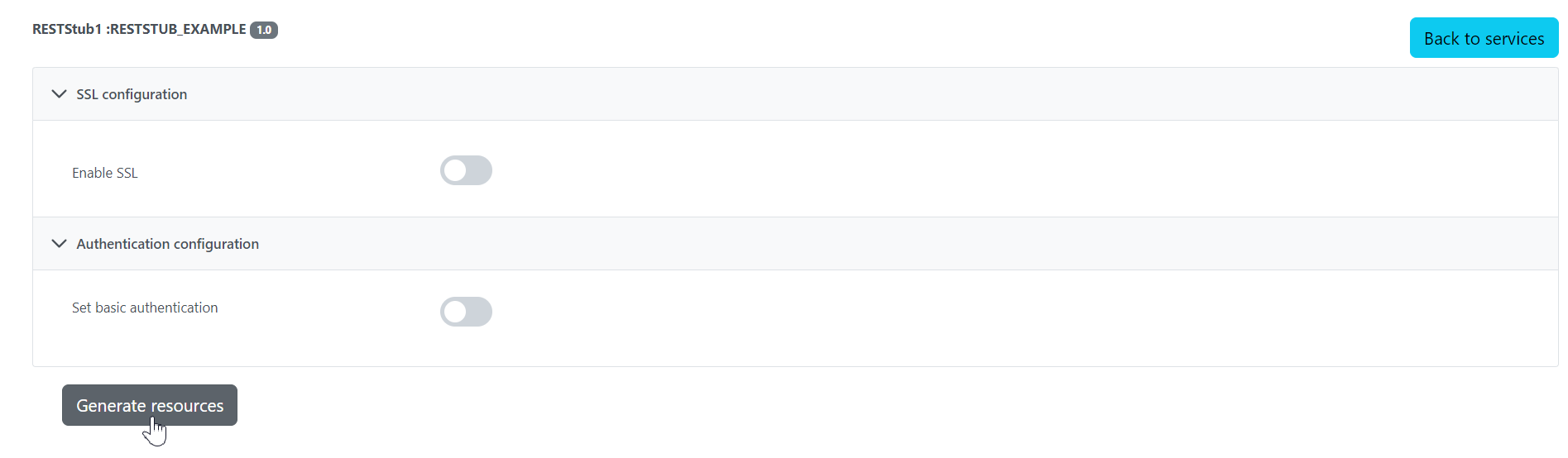
SSL configuration and basic authentication can be set at this point.
Select the resource from the Resource drop-down and method from the Method drop-down, and click the Test button.
A default sample appears, which may be edited as per the requirement. After editing, to reset the values to default, click the Default sample button.
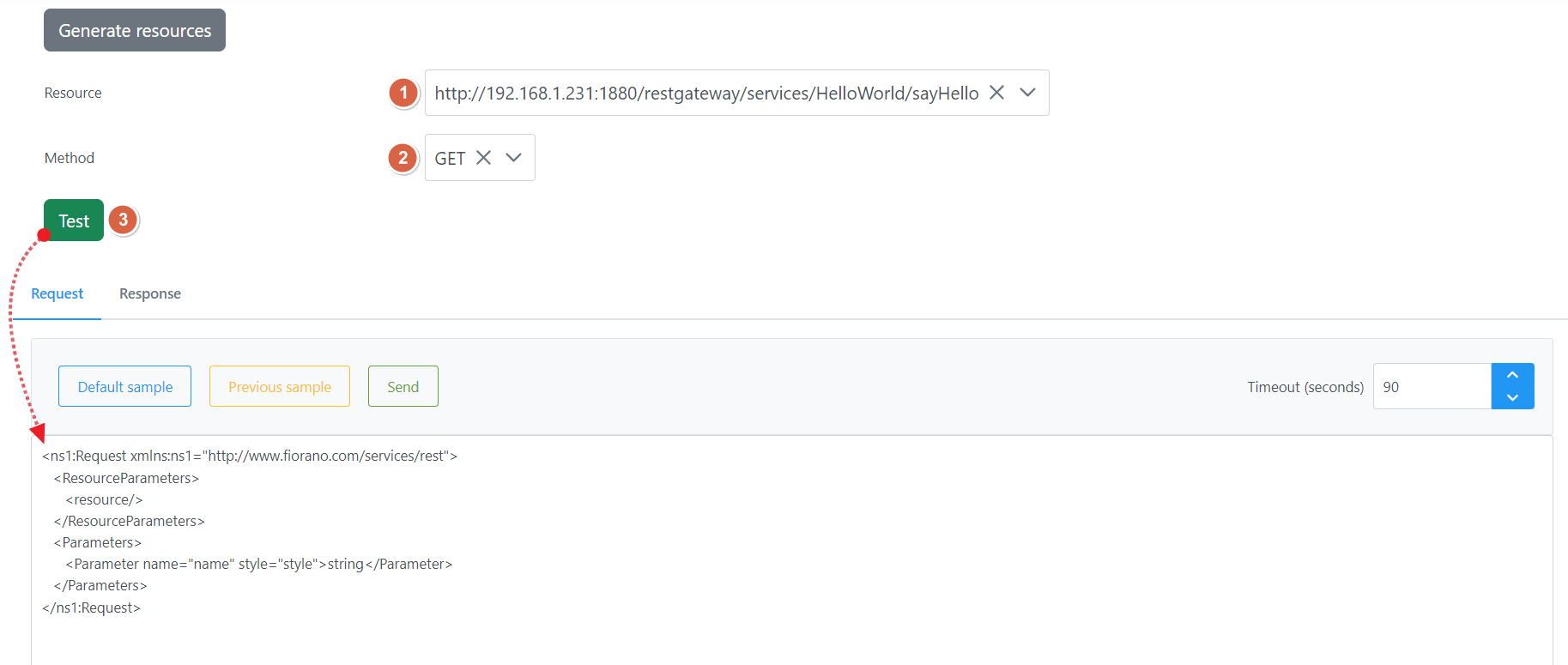
Click the Send button to execute the test.
THe response status number "200" indicates that the request has been successfully sent for the GET method.
Security
Click the Add button to add a user with security attributes defined.
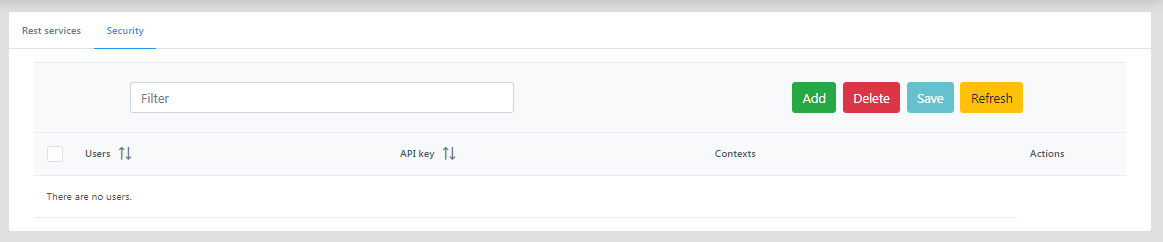
Provide the username, context name, and API key, and click the Add user button.
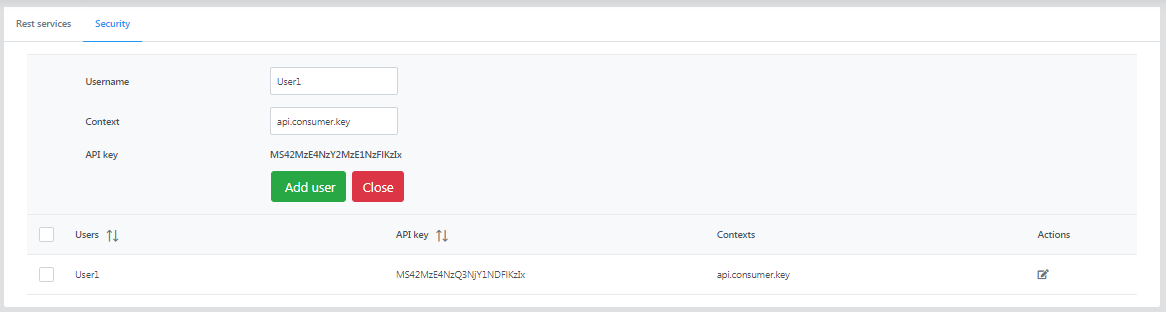
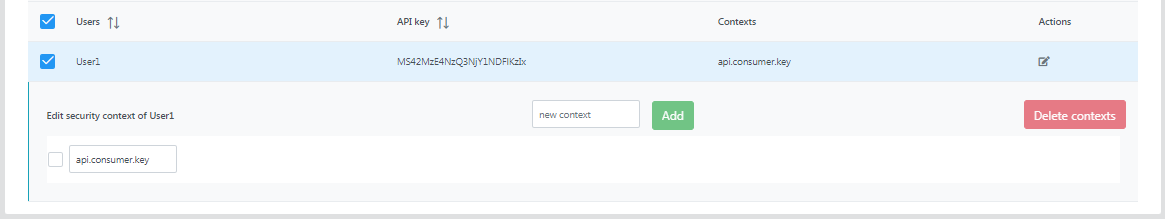
Click the edit button under the Actions column to add a new context to the user.
Analytics
Statistics
A graphical presentation of message traffic through ports of a specific application.
Specify the role (Properties > General > Workflow) of the port in the event process to enable statistics and hence display the graph.
Example
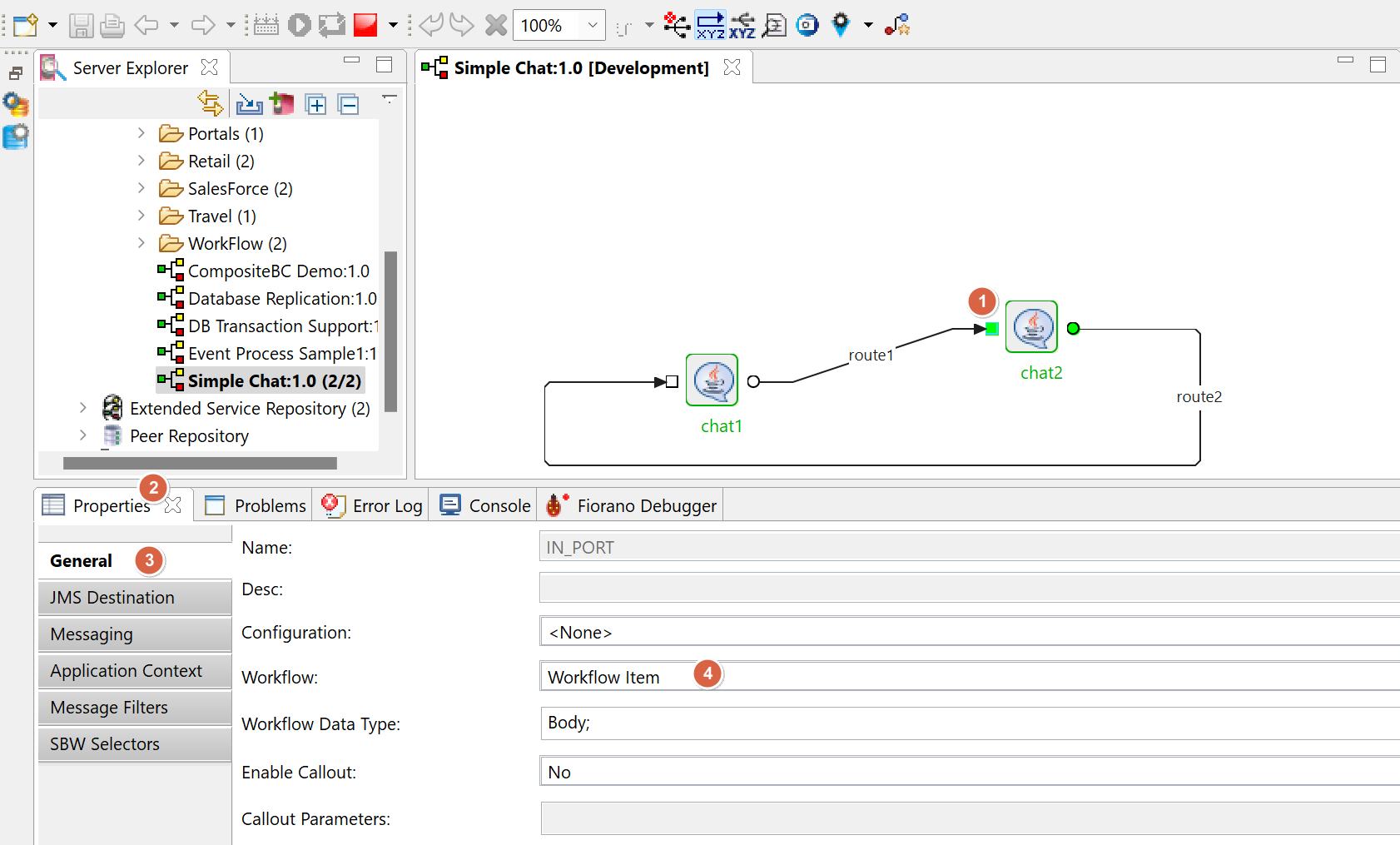
The graphs in the images below are a result of the configuration as shown in the image above.
It also gives the rate of message flow per minute and the error percentage of message flow.
Choose the event process and the time frame (hour/day/week/month) to see the Traffic Pattern graph along with the above-mentioned values.
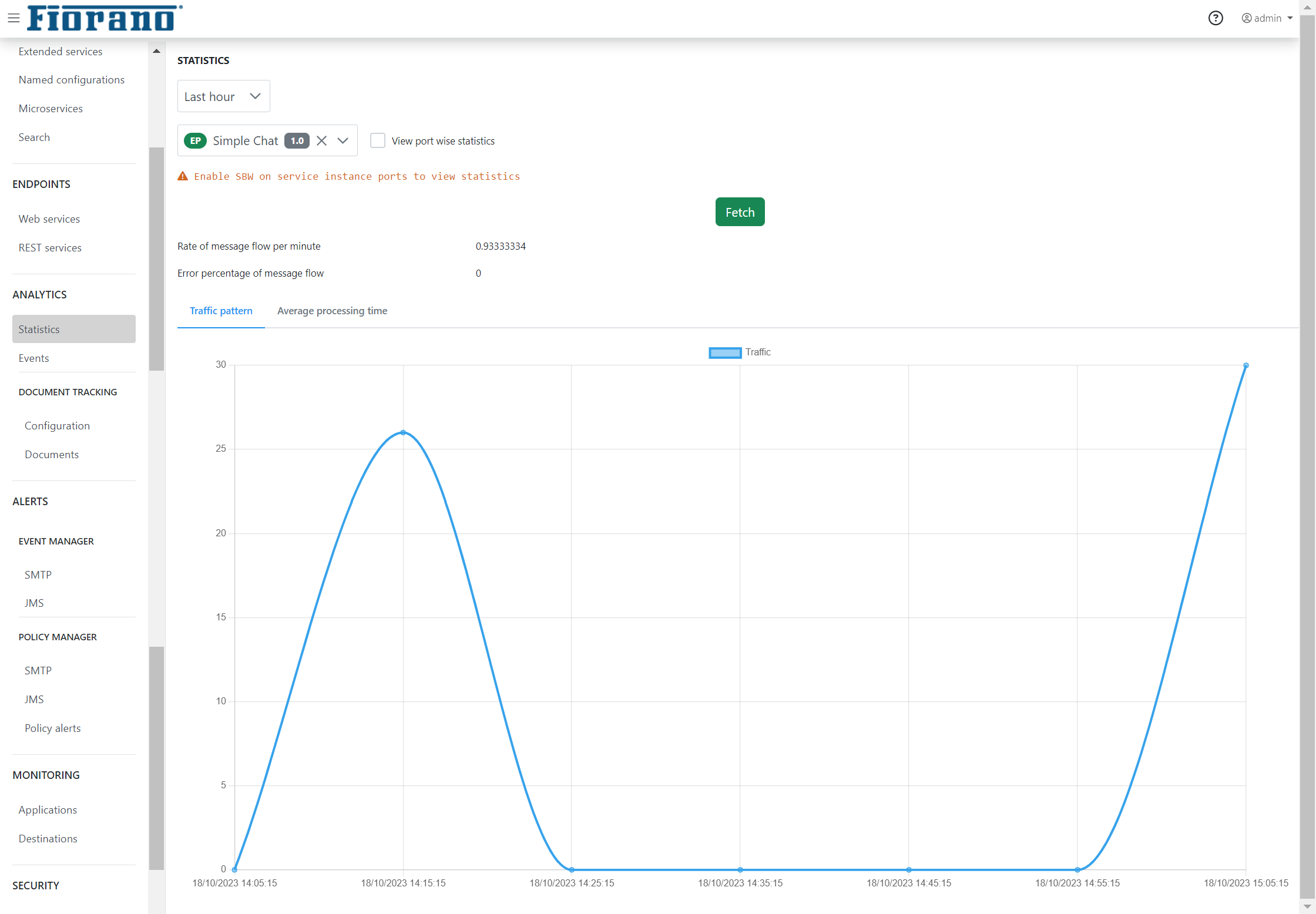
View port wise statistics
Enable the View port wise statistics option to record the port-wise data to display the graph.
Choose the respective service instance and the port, and click the Fetch button to display the port-wise statistics graph.
The Average processing time tab displays a graph representing the same as the name suggests.
Events
Provides the details of the events generated by the Fiorano Enterprise Server (FES), the Fiorano Peer Server (FPS), Applications, Services, Security, and the SBW exceptions that occur while running various event processes.
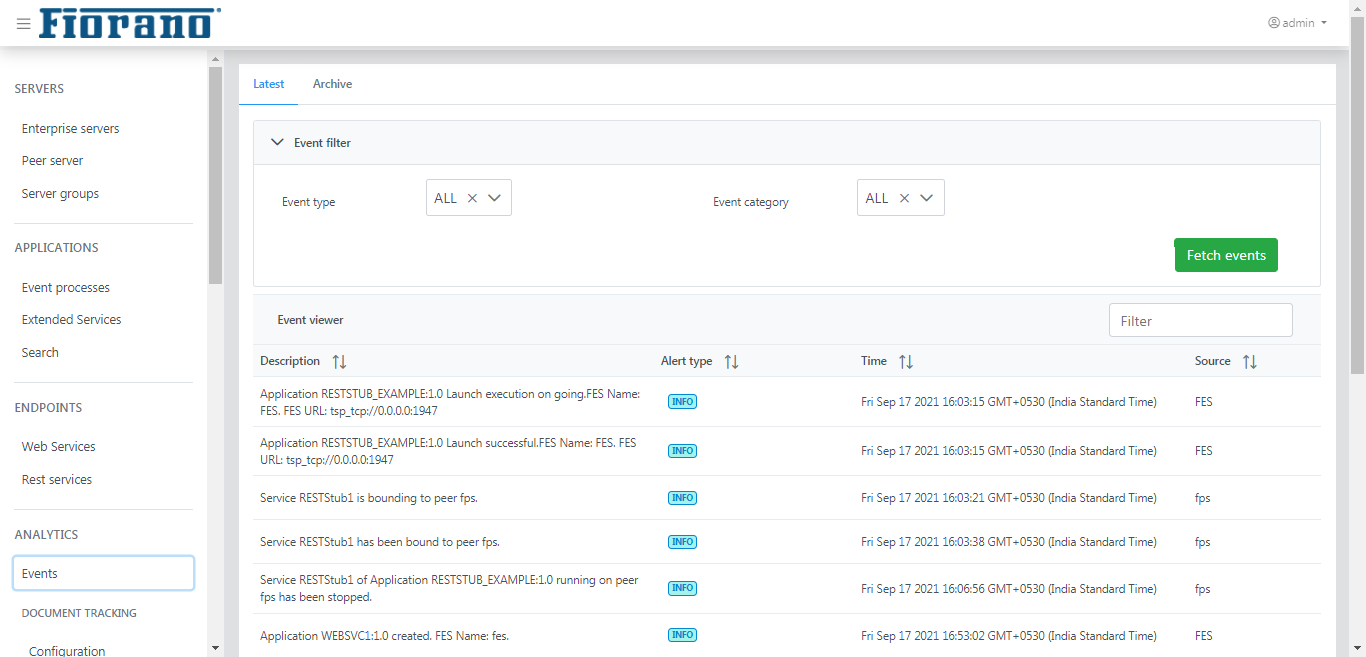
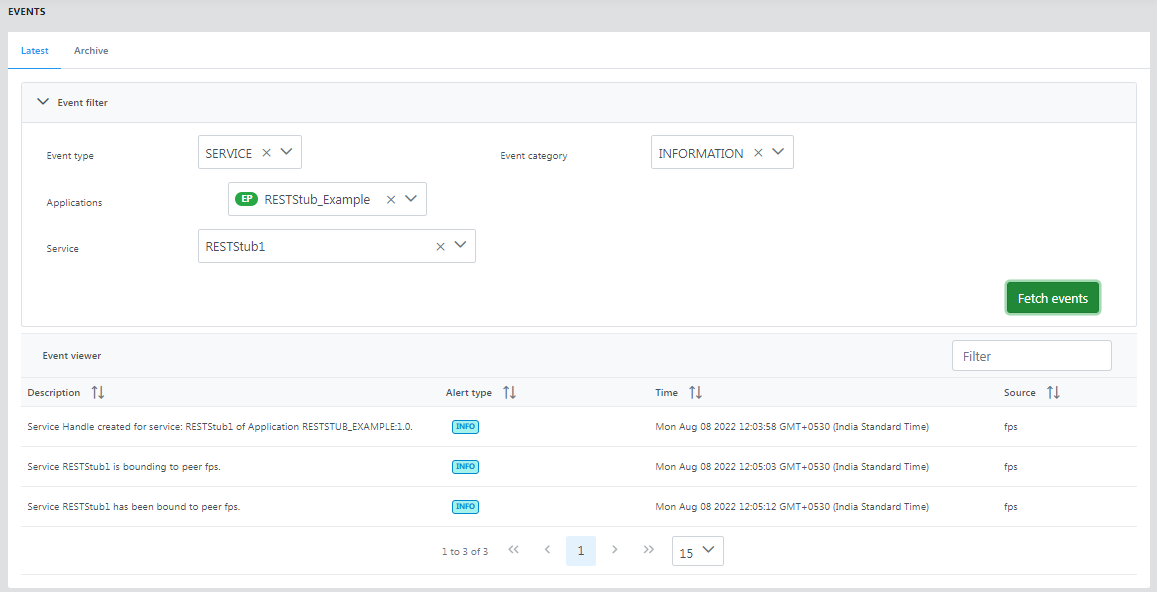
Figure 13: Events tab showing the latest events
The Event tab has two sections which are explained below.
Latest
This gives the list of the latest events generated by the enterprise server and peer servers.
To filter specific events, use the Event type and Event category from the options listed below and click the Fetch events button.
The sub-category mentioned under certain event types is the drop-down option that appears when that particular event type is selected.
| Event type | Event Category |
|---|---|
|
|
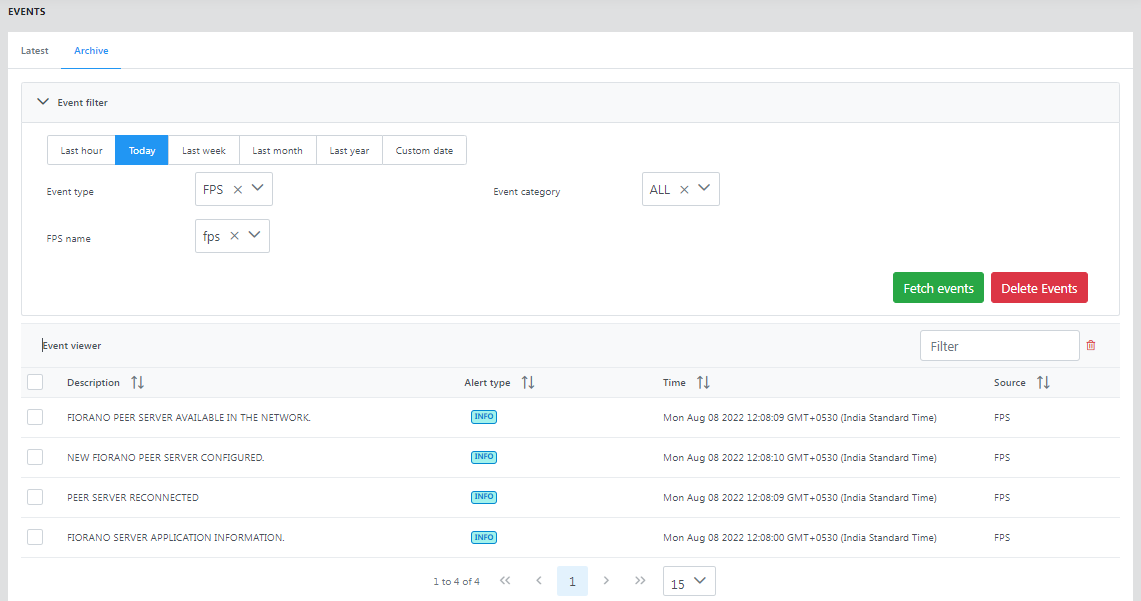
Archive
In this section, those events which are archived over a period of time in the database can be filtered using various date ranges.
The event type and category are as explained in the Latest section above. The date range that can be selected is based on the hour, day, week, month year, and customer date where specific start and end dates can be provided in the DD/MM/YYYY HH:MM format.
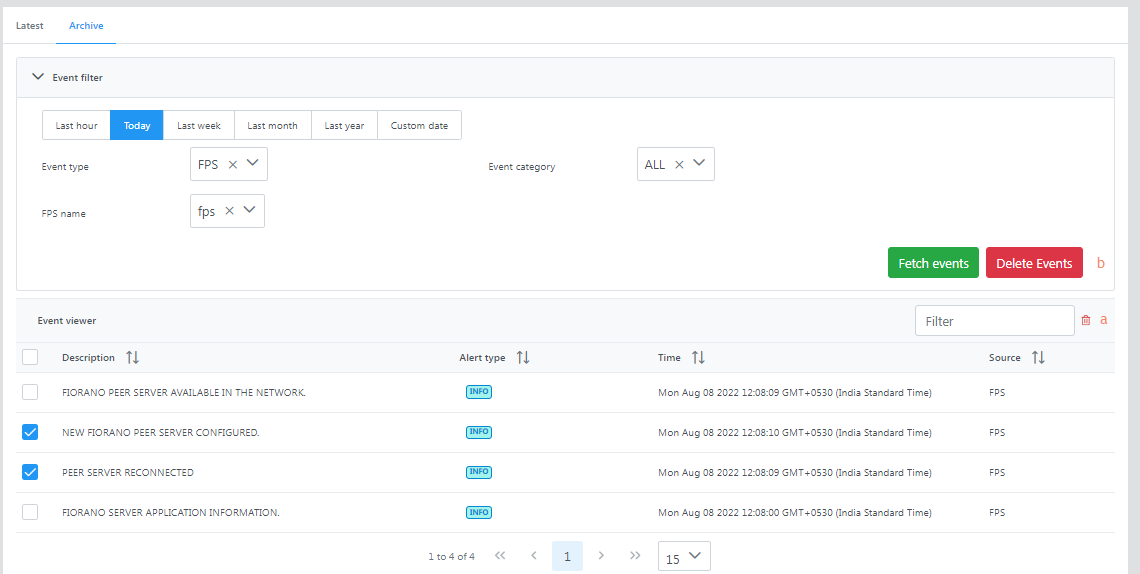
Deleting archived events
To delete events, perform the following action accordingly:
- Single or multiple events: Select the relevant event(s) and click the Delete icon.
- All events: Click the Delete Events button.
Document Tracking
The document tracking feature is configured as part of FES to track SBW events into the database running within Enterprise Server.
Document Tracking is enabled from eStudio. Refer to the Enabling Document Tracking section to know how to enable Document Tracking in a Workflow of an Event Process and hence track them in the Dashboard.
Configuration
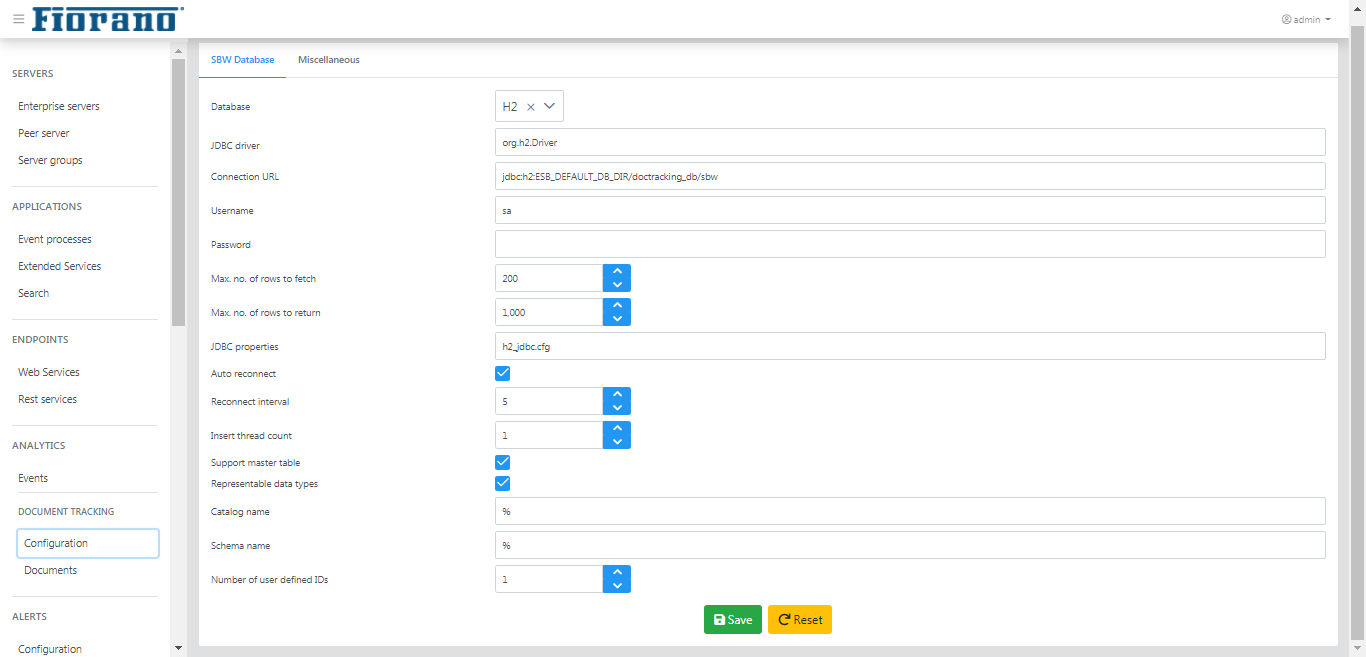
By default, the tracked documents are set to be stored in the H2 database that runs inside the Enterprise Server. The section below allows configuring an external database for Document Tracking.
SBW Database
Provide property values of the database and click Save to assign the database.
Refer to the SBW Database Property descriptions section for the database property descriptions.
The Reset button helps to reset the values entered before saving those.
Miscellaneous
This section displays the event processes and extended services for which documents can be tracked and it allows to set global settings for event processes to enable/disable tracking globally in FES and purge document can be set for multiple documents.
Global document tracking in FES
Click to expand this option to configure tracking details as below.
Enable document tracking for event processes and extended services globally in FES
Enable this option to enable document tracking for event processes and extended services globally in FES.
Refer to the Purging SBW Documents of Multiple Applications section for the rest of the properties that help delete document tracking data.
Event processes
This section not only shows the event processes for which documents can be tracked as well as purging can be enabled, but can configure to reset counter and to purge old documents of a selected event process too. The indication under the columns Track documents and Enable purge change based on the change in settings.
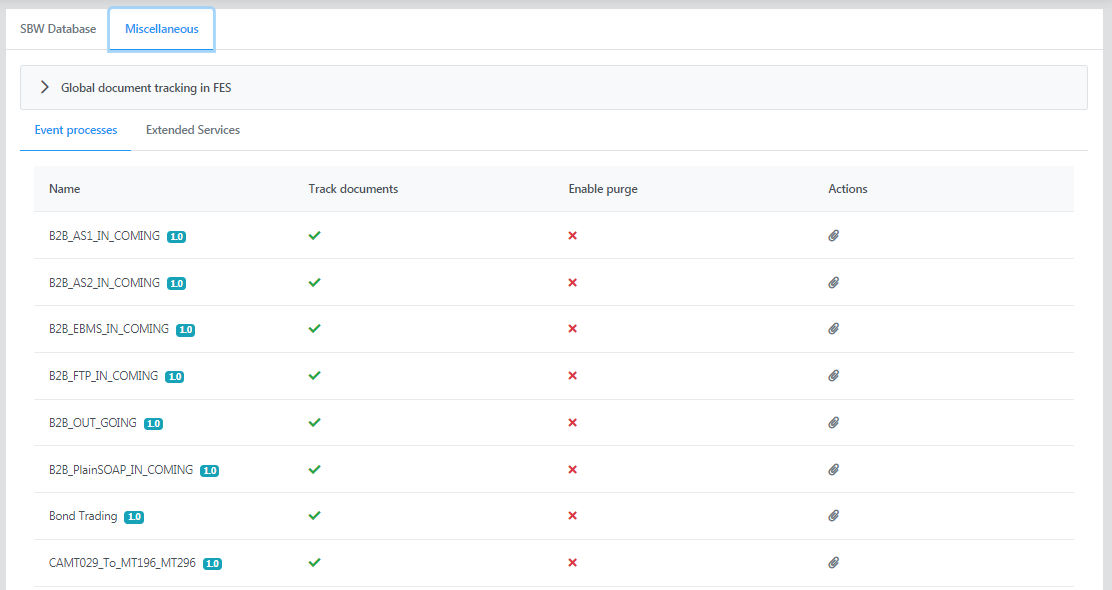
Click the attachments icon under the Actions column to
- Reset Counters
- Purge old documents
Reset Counters
The counters can be reset for the following types of counters; all or any one of these:
- In Transit
- Completed
- Exception Documents
Select the options and click the Reset button.
To revert the counters, click the Undo reset button.
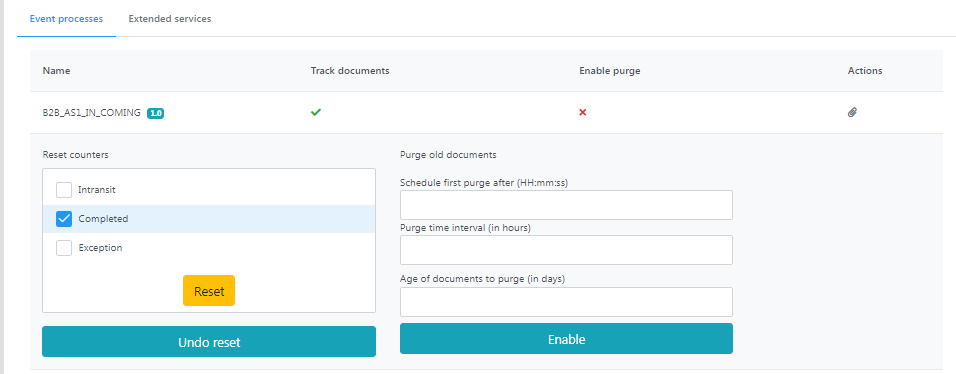
Example
Select the Completed option and click the Reset button for a message with counters as below:
- Intransit - 3
- Completed - 12
- Error - 2
The counter will be updated as below:
- Intransit - 3
- Completed - 0
- Error - 2
Click the Undo reset button to revert the values that were previously changed by clicking the Reset button.
Purging SBW documents
This option helps to purge SBW document records from the database. Purging can be done based on
- a scheduled time for a particular application
- a scheduled time for multiple applications
- instant deletion of an application or multiple applications
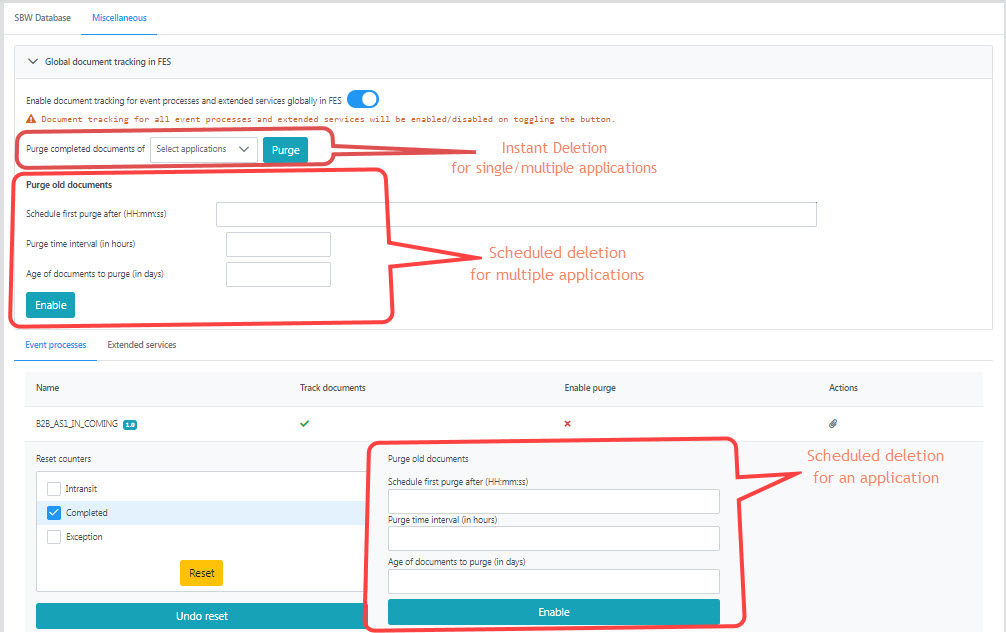
Purging SBW documents of an application
Document tracking records take up a substantial amount of disk space on the enterprise server over time. A scheduled deletion by discarding old entries can be performed to manage disk space in the Document Tracking Database.
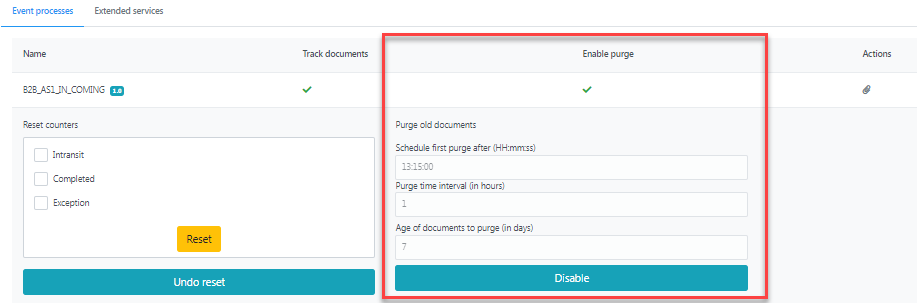
The Purge old documents option allows scheduling a task for purging old SBW document records of the selected event process from the database in the following manner:
Schedule first purge after: Time, in 24 hrs format, at which the task would execute.
- Purge time interval (in Hrs): Interval at which task of deleting docs would execute.
Age of documents to purge (in days): Documents older than this value will be deleted.
Click the Enable button after providing these values.
Click the Disable button to stop purging documents as configured.
After enabling the Purge old documents option, the cross mark under the Enable purge column turns into a tick mark which indicates that the purge is enabled.
Purging SBW documents of multiple applications
Purging can be set for multiple documents as well by performing the following actions.
- Expand the Global document tracking in FES option on top of the page.
- Select the applications for which purging needs to be enabled from the Purge completed documents of drop-down.
- Under the Purge old documents section, provide values as explained in the section above, and click the Enable button below it.
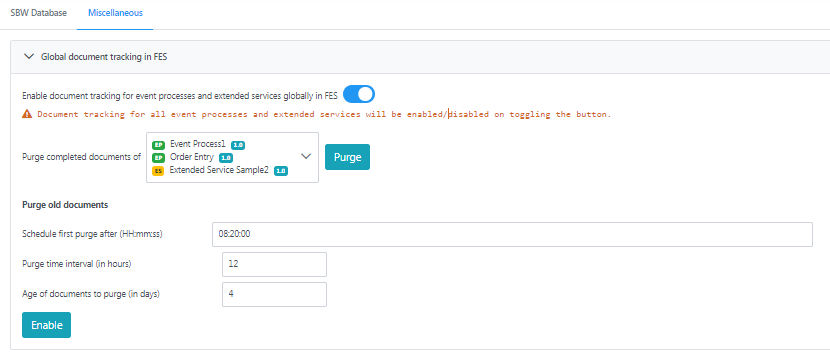
Click the Disable button (which gets enabled after clicking the Enable button) to stop purging documents as configured.
Purging SBW document records instantly
Tracked document records of applications stored in the database till the moment can be instantly deleted. To perform this, after selecting the applications as mentioned in the above section, click the Purge button against the Purge completed documents of drop-down.
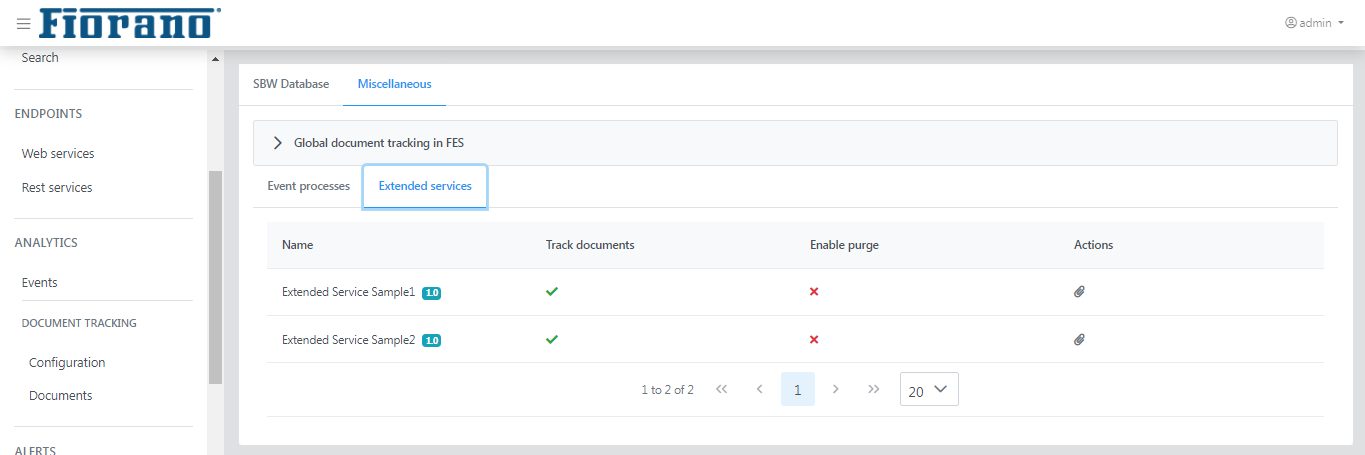
Extended services
This section shows the event processes for which documents can be tracked. It has all the functions available in the Event processes section; please refer to the Event processes section.
Documents
In this section, the tracked documents or the event processes for which SBW workflow is set can be fetched, details of each document can be viewed and deleted, and more importantly, the message and its properties can be edited and reinjected for those messages that face exception or reach the exception port.
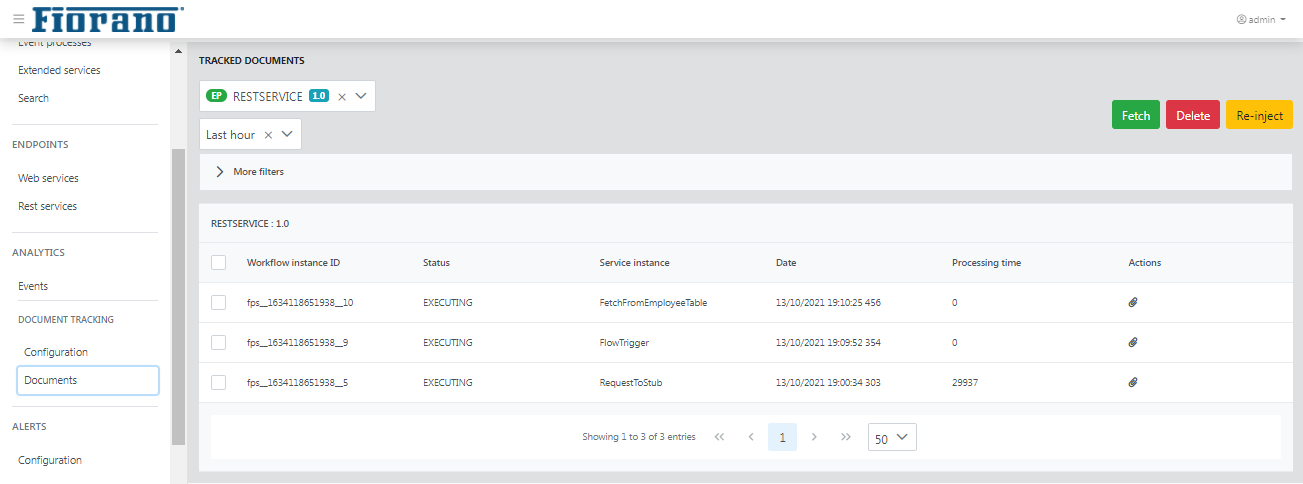
Searching SBW Documents
Select the application that needs to be tracked from the drop-down and click the Fetch button to display the details of the tracked documents such as Workflow instance ID, Status (executing/executed), Service instance, Date, and Processing time.
Filtering Options
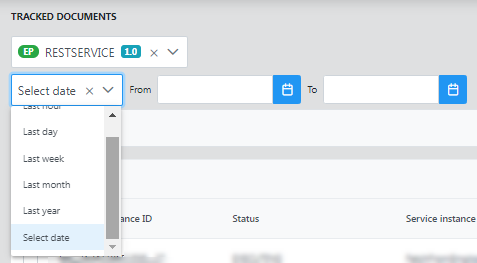
Date
Though by default, the data is filtered for the previous hour, documents can be searched based on the date they were generated as well by specifying a particular period of time as required.
Click the Select date drop-down and select from the options Last hour, Last day, Last week, Last month, and Last year for the latest hourly, daily, weekly, monthly, and yearly data respectively.
Select the Date Range option to opt for specific start and end dates to filter records.
More filters
An application can be further tracked down by specifying more details. Expand the More filters option to do so and provide any of the details such as Service instance, Port, User document ID, Workflow instance ID, Document ID, Fiorano Peer Server, Status, and Message and click the Fetch button.
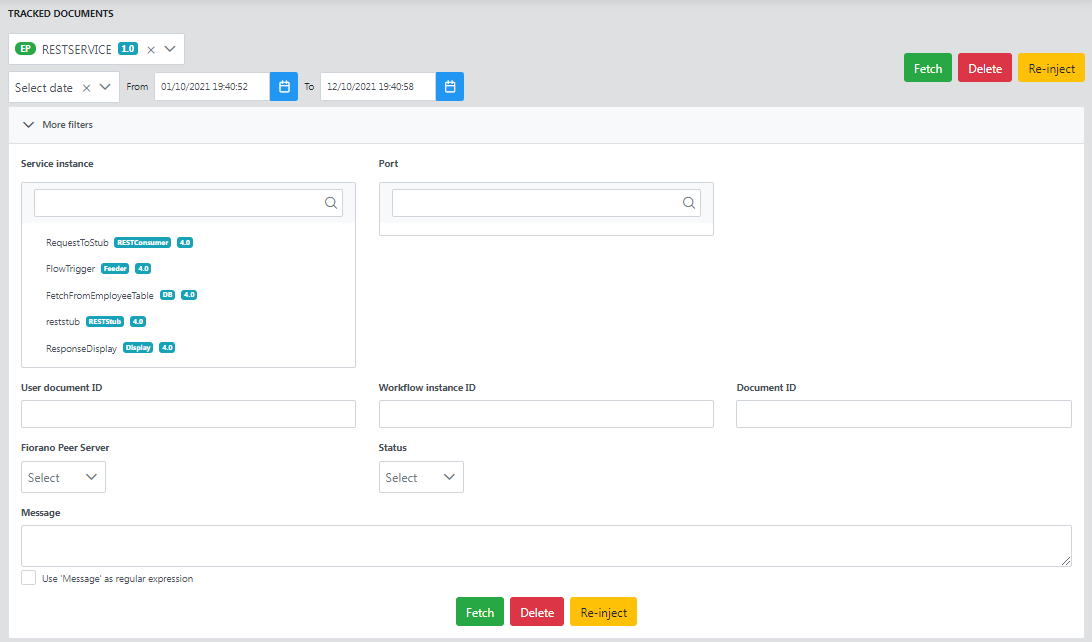
For searching for the tracked documents from eStudio, refer to the Searching SBW Documents section.
Click the details button for a particular workflow instance to see the details of the workflow such as Document ID, User document ID, Service instance Port, Time in, Time out, and Processing time.
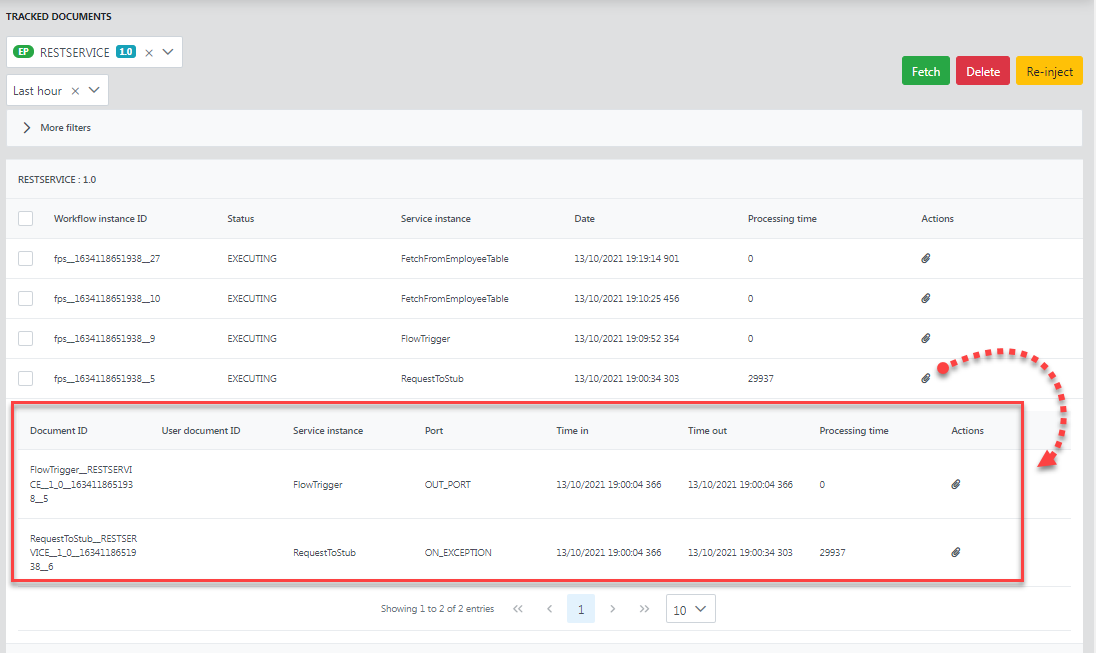
Re-injecting Documents
Documents can be selected as per choice and re-injected using the ReInject Selected Documents button present in the upper-right part of the screen. This is mainly used to re-inject failed documents, that is, the messages that reach the exception port.
Steps
- Click the details icon (see the image above) under the Actions column of a document that is on the exception (ideally, as reinjecting is generally for resolving errors) port to see the details such as message body, general details, properties, carry forward context, application context, attachments, and source contexts.
- Click the Edit to re-inject button to edit the properties mentioned above.
- Make the required changes and click the Reinject button to trigger the edited data.
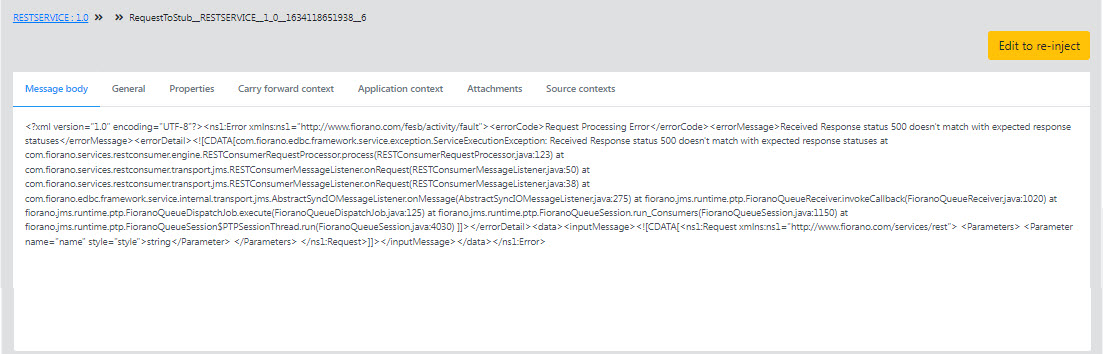
Figure 30: Tracked document
Refer to the Re-injecting Failed Documents page to understand more about failed documents and re-injection.
Deleting Selected Documents
To delete a document or a set of documents, select the record(s) and click the Delete button.
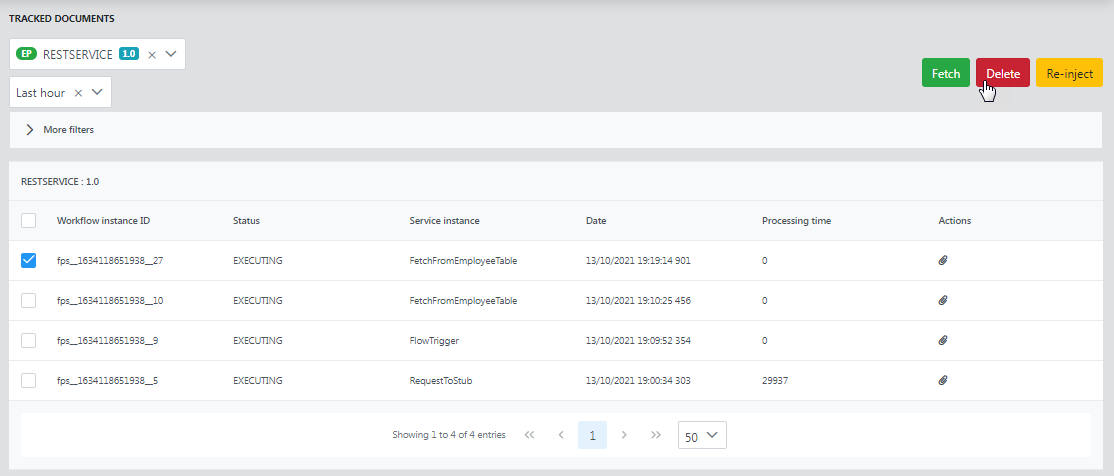
Selecting a document to delete SBW records
Alerts
Event Manager
SMTP
SMTP event alerts can be added and server settings can be changed from this page.
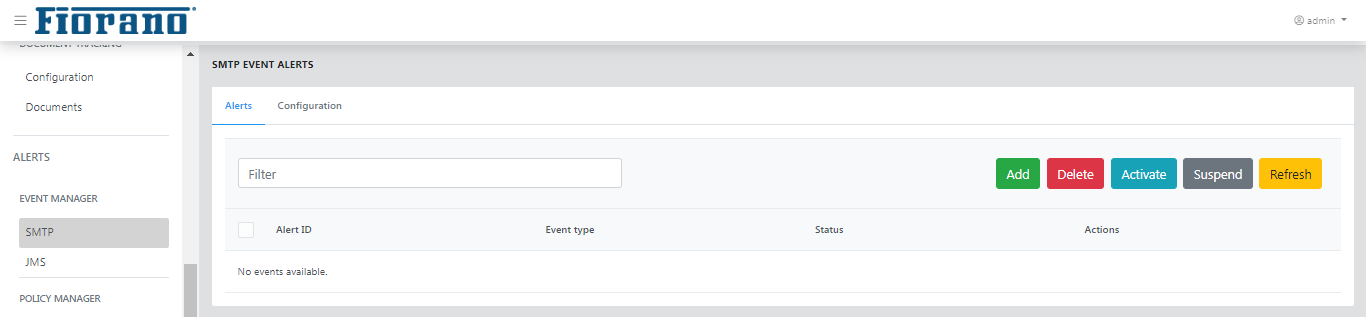
Alerts
This tab allows to add new alerts and edit, activate, suspend, and also to delete an existing alert. All alerts that are added will be listed here.
Adding an alert
To add an alert, click the Add button.
Choose the Event Type and Event Category from the drop-down list and enter the email ID of the recipient in Receiver email field.
- Refer to the List of Events section to see the list of events under each Event Type.
- Select the Periodic alert time interval option and specify the period alert time interval in minutes to configure Periodic Email alert notifications.
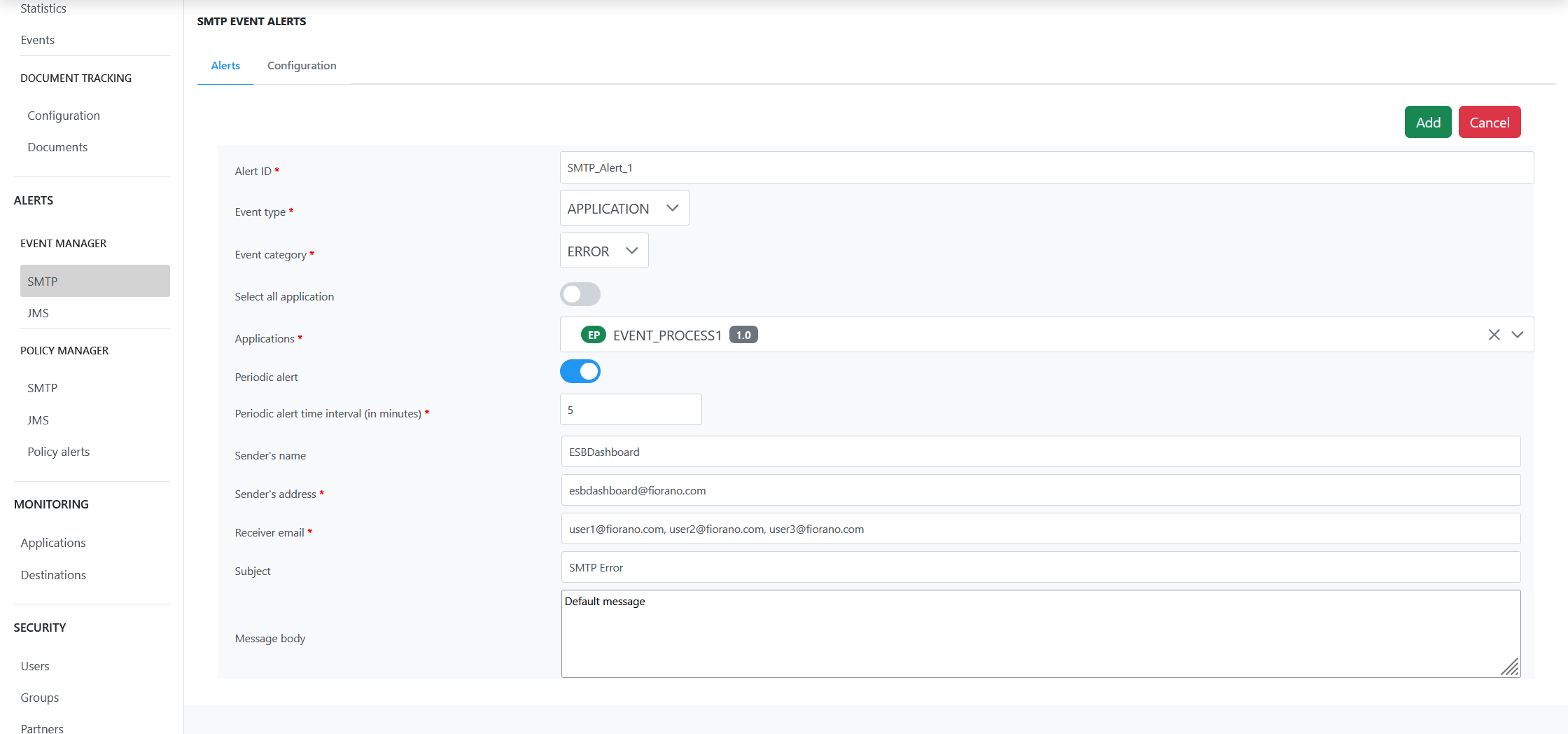
- Click the Add button to save the event.
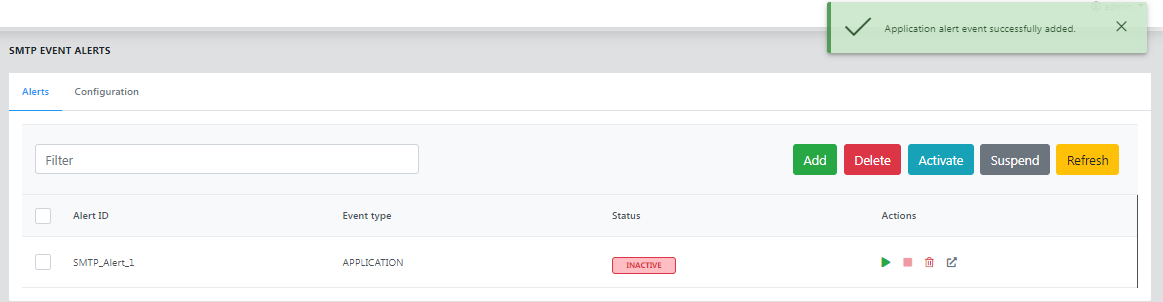
Activating an alert
To activate the alert, click the Activate button.
If there is more than one alert to be activated/suspended, select the alerts and use the Activate/Suspend button.
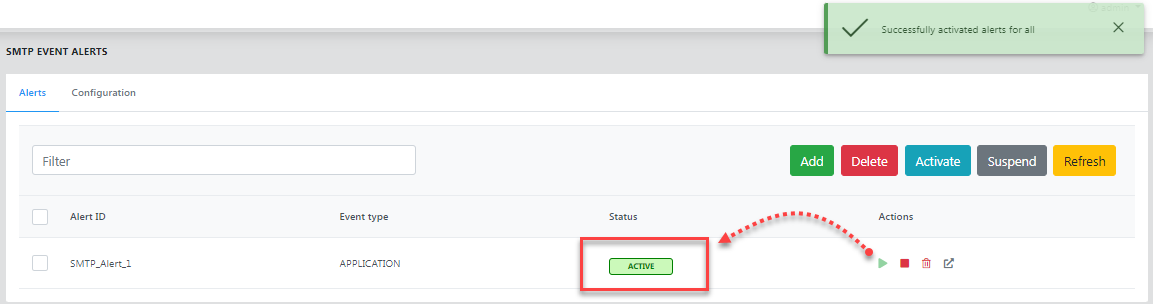
Click the Delete icon to delete an alert and use the Delete button to delete multiple alerts.
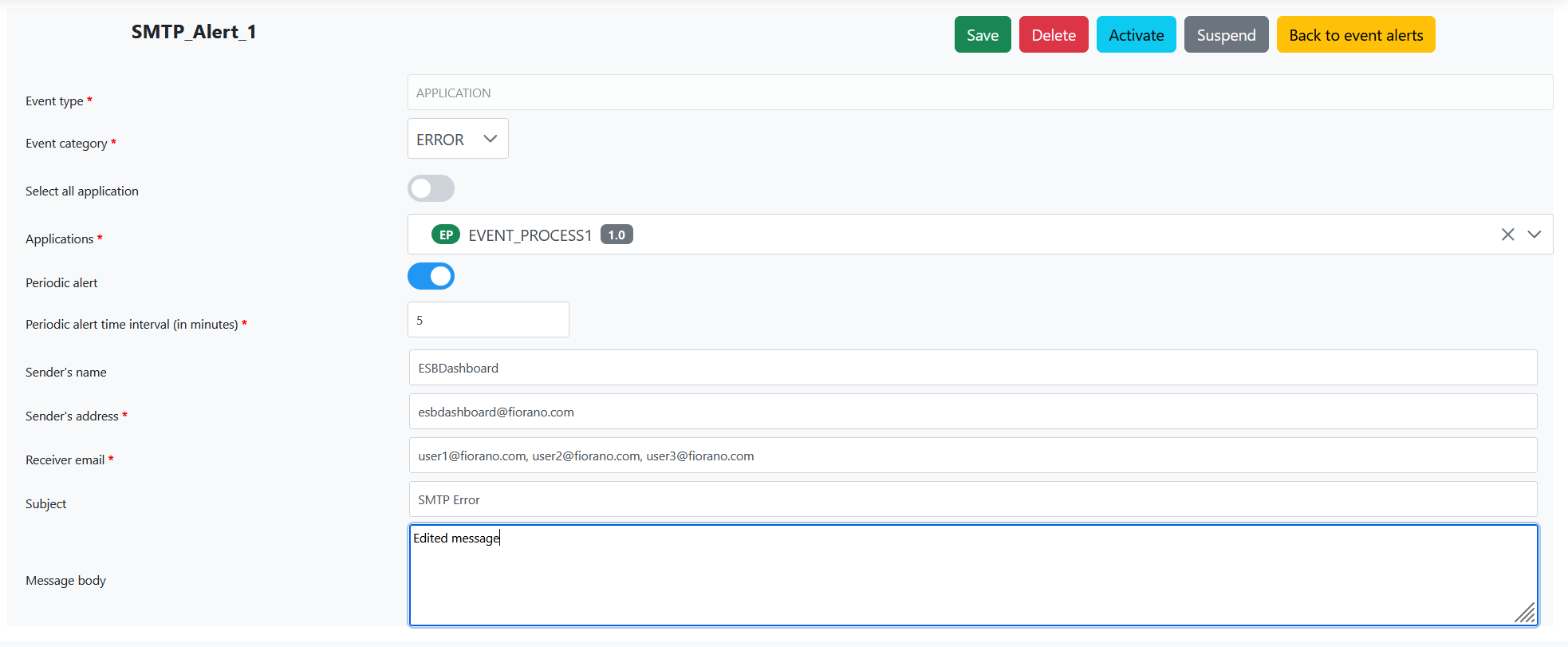
Alert Properties
Properties | Description |
|---|---|
| Alert ID | A unique name representing the alert. |
Event type | Event alert related to one of the following:
The sub-categories mentioned under the event types are the properties that appear as drop-down options when those particular event types are selected. |
Event category | Category of the event alert from one of the following:
|
Select all application/ Select all service | Selects all applications/services for sending alerts. This option is applicable for Application/Service event type. |
Applications/ Service | Select one of the applications/services from the list. This option is applicable for Application/Service event type.
|
| Periodic alert | Whether to send periodic alerts or not. |
| Periodic alert time interval (in minutes) | Specify the period alert time interval in minutes to configure Periodic Email Alert notifications. |
Sender's name | The sender name as it appears on the email client. |
Sender's address | The email address of the sender sending the notification. |
| Receiver email | The email address of the recipient to whom the notification needs to be sent. Multiple email addresses may be used separated by commas. |
| Subject | Short description of the message content. |
| Message body | Long description of the content to be conveyed for the alert |
Editing an alert
- If the alert is in an activated state, click the Suspend icon to inactivate it, because an active alert cannot be edited.
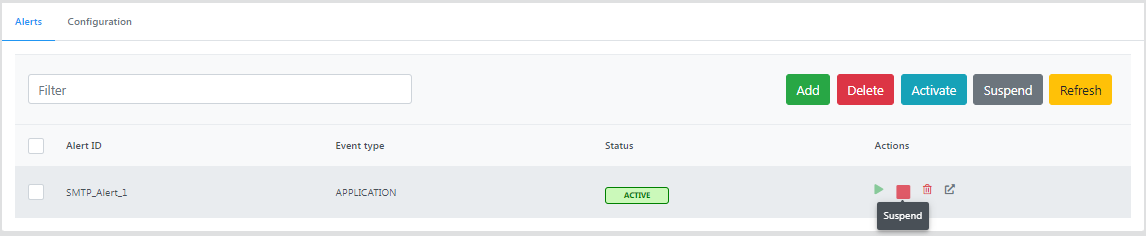
Click the Details icon.
Alerts can be suspended (by clicking the Suspend button inside the Details page) after clicking the Details icon as well.
- Make the changes and click Save.
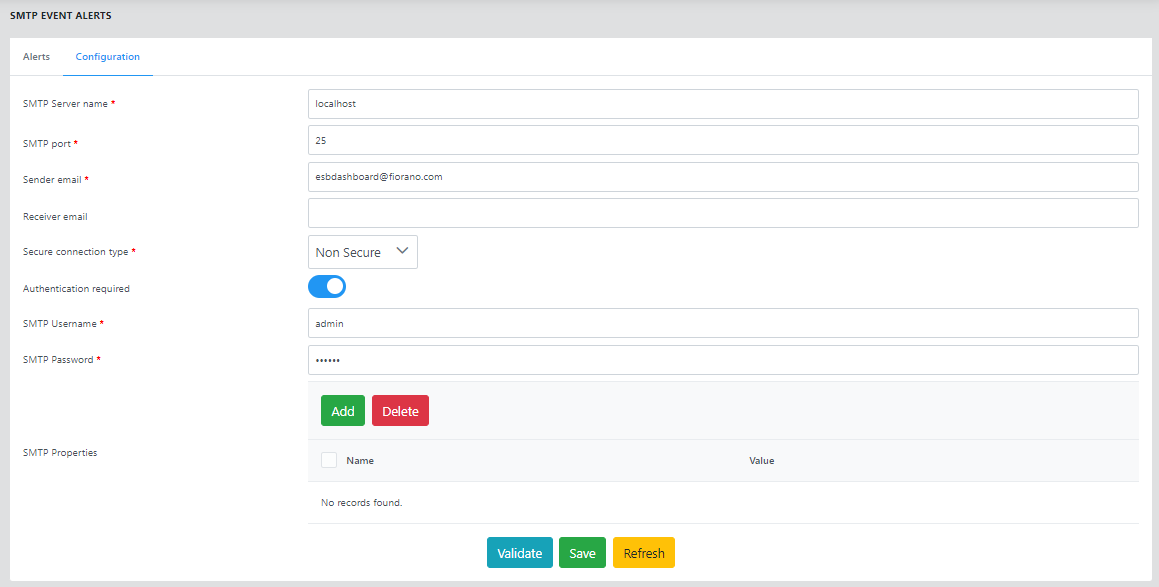
Configuration
You can change the configuration of the mail server settings in the Configure tab. This page also provides an option to specify usernames and passwords in case the mail server requires authentication of these in order to send e-mails. Enable the Authentication required option to provide credentials.
Provide the server details, click Validate to ensure that the connection is established, and click Save to apply the settings.
Refer to the Configuring SMTP and JMS Transports section for property descriptions.
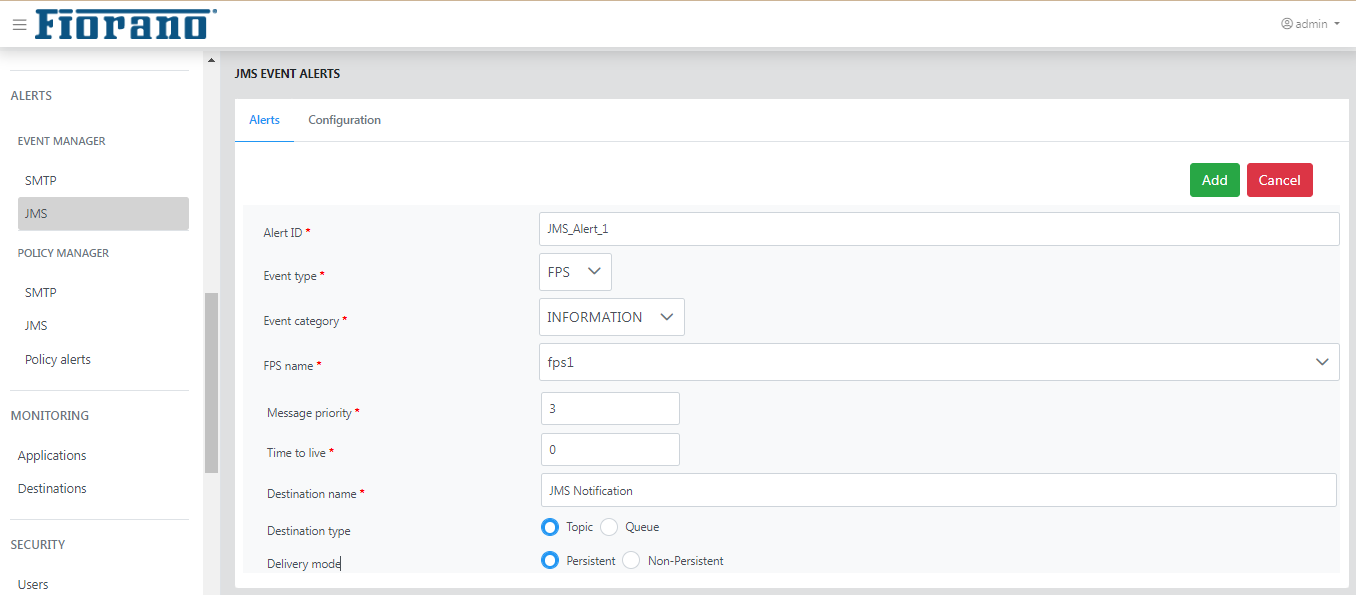
JMS
Alerts
Steps to add and manage a JMS alerts is same as illustrated in the JMS section under the Event Manager section.
Refer to the List of Events section to see the list of events under each Event Type.
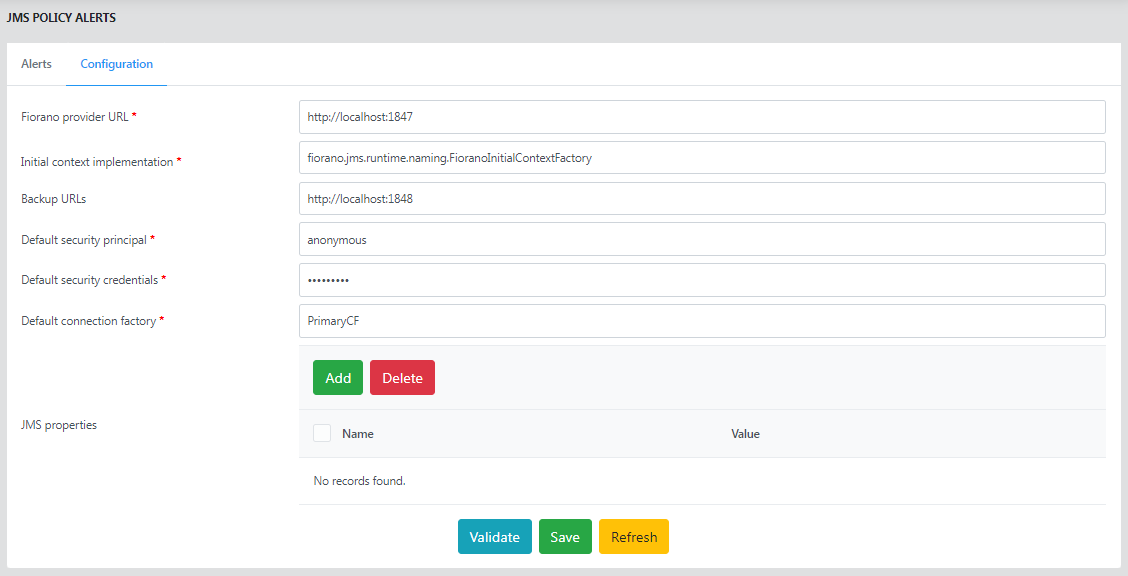
Configuration
Configure the JMS server settings in the Configuration tab. This page also provides an option to specify security credentials in case the JMS server requires authentication.
Refer to the Configuring SMTP and JMS Transports section for property descriptions.
Policy Manager
Alerts are a combination of a message and a transport for delivering that message. A message could be in different formats such as plain text, XML, etc and transports could be any of the supported ones. Alerts created can be reused across different policies.
SMTP
Refer to the SMTP section in the Managing SMTP and JMS Alerts page to know about adding and activating SMTP policy alerts.
JMS
Refer to the JMS section in the Managing SMTP and JMS Alerts page to know about adding and activating JMS policy alerts.
Policy Alerts
This tab shows all the policies that are present in the Fiorano Network. This tab allows you to add the following types of policies, edit or delete an existing policy, activate or suspend existing policies.
- Backlog
- Low Disk
- Server Low Memory
- Component Low Memory
Refer to the Managing Policies section to know about adding policies and adding SMTP/JMS alert to the policy.
Monitoring
The monitoring section helps you to track Applications and destinations in the Fiorano Network. This section helps to monitor the performance of services by enabling monitoring in the respective component CPS.
The Monitoring tab has the following sections:
- Applications
- Destinations
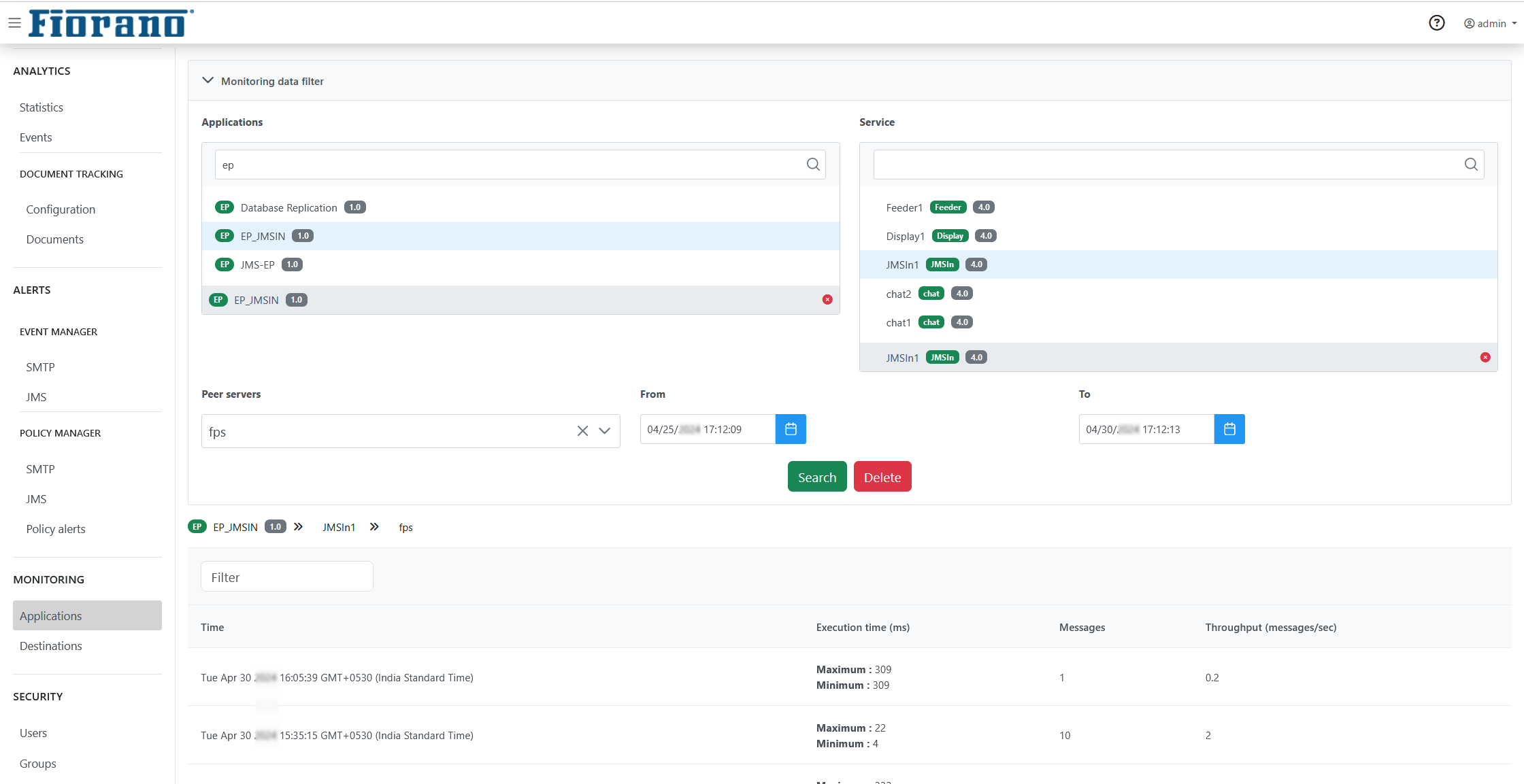
Applications
This view shows the performance based on messages sent by components in data form. Select the components for which monitoring data should be displayed for the selected period to see the performance. The details such as Time, Applications, Service, Peer, Execution time, Messages, and Throughput will be displayed.
To display the monitoring statistics in Dashboard, apart from enabling Monitoring in the CPS, enable the ListenForUserEvents property in the Events Manager section under Advanced Properties.
This can also be done from eStudio Profile Manager. Refer to the Enable ListenForUserEvents parameter for Monitoring Performance section to read through the steps.
Destinations
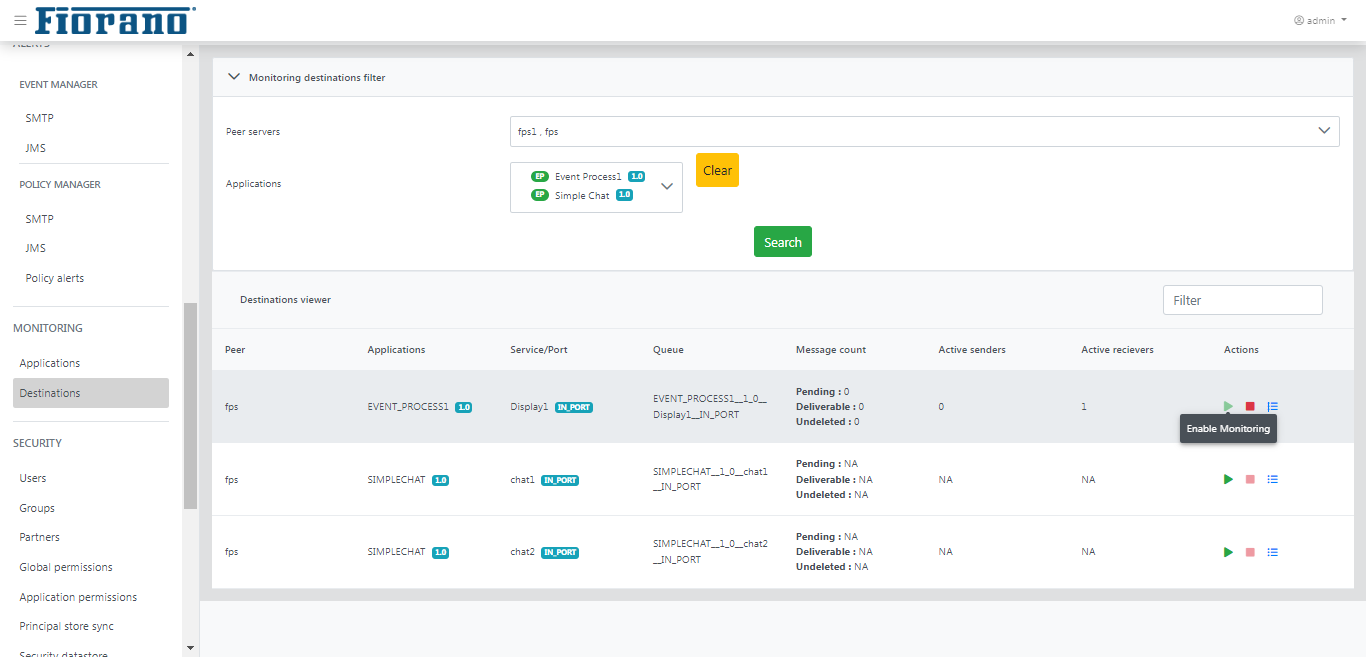
This view allows the user to monitor Peer server name, Applications, Service/Port, Queue, Message count, Active senders, and Active receivers for the queues of applications that are running.
Prerequisite:
To track messages in this section, the EnableMessageMonitoring property needs to be enabled in the Peer Server properties. This needs to be done from the eStudio Profile Manager perspective.
Refer to the Enable Message Monitoring section in the View Message Monitoring Logs section to see how to enable this from the Profile Manager perspective.
After configuring the above, Event Processes running under the respective peer server(s) get populated in the Applications tab.
Select the Peer Server and applications for which logs need to be monitored and click the Search button to see the results under the Destinations viewer section.
Click the Play icon under the Actions column to start monitoring queues of the selected Application.
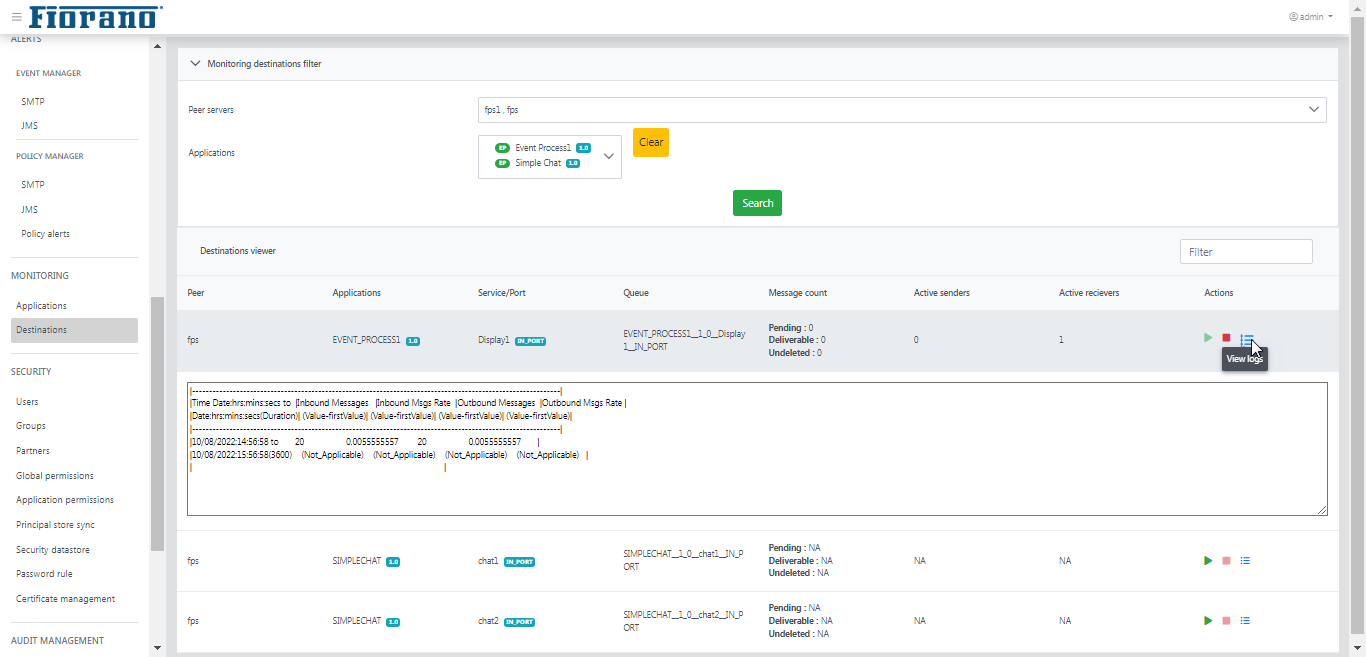
Viewing Message Logs
Click the Logs icon under the Actions column to view logs for monitoring the respective queue.
Security
Security section gives the security actions that can be performed in the Fiorano Network. These include adding/editing users, groups, application-level or group-level permissions, and validation or strengthen rules for passwords. These also include the principal store synchronization.
The Security tab has seven sections:
- Users
- Groups
- Partners
- Global Permissions
- Application Permissions
- Principal Store Sync
- Security Datastore
- Password Rule
- Certificate Management
Users
This tab shows users presently registered in the Fiorano network. The actions that can be undertaken in this tab include creating new users, deleting an existing user, or changing as well as encrypting a password for an existing user.
- Click the Add user button to add a new user and click the Delete icon present in the corresponding user row to delete that user.
- Click the Encrypt Password button to encrypt a password and click the Edit icon present in the corresponding user row to delete that user.
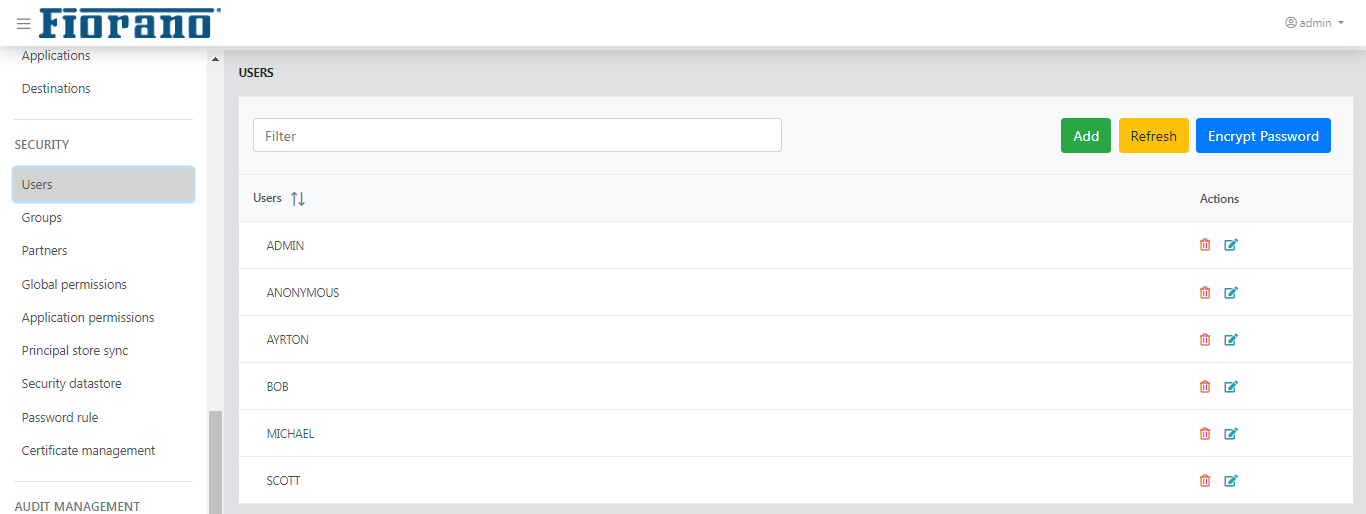
Figure 42: Users
Groups
This tab shows the groups registered in the Fiorano network. Groups allow grouping users together and applying actions on them together. The actions that can be undertaken in this tab include creating new groups, deleting/editing an existing group.
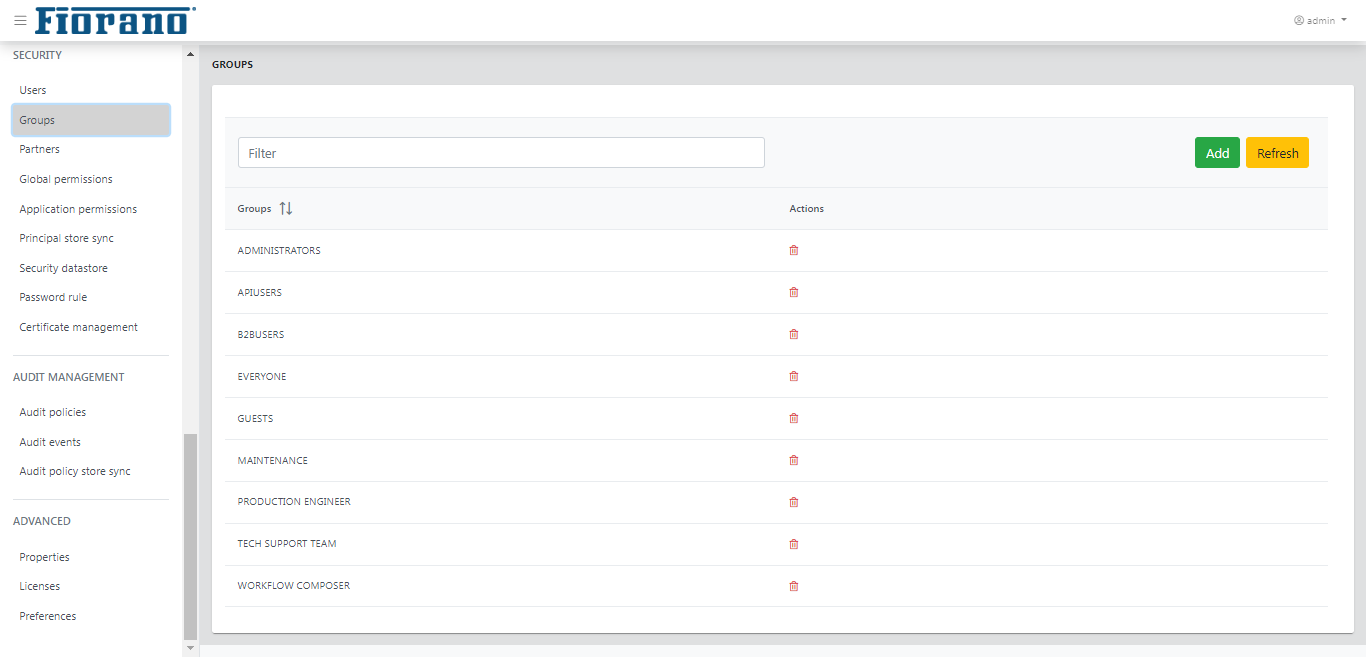
Click a group name to add/remove members. Select the user name and click the move button accordingly to add/remove.
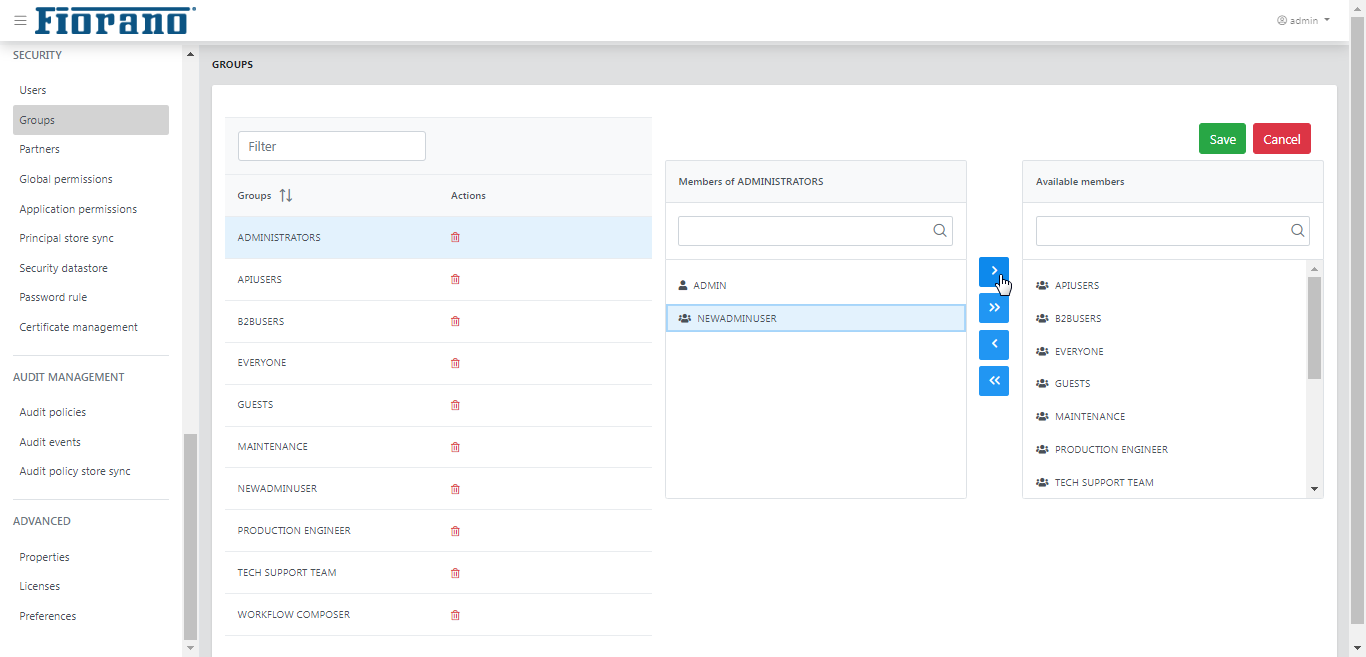
The "NEWADMINUSER" user under Members of ADMINISTRATORS section is created and moved from Available members section for illustration purpose.
Partners
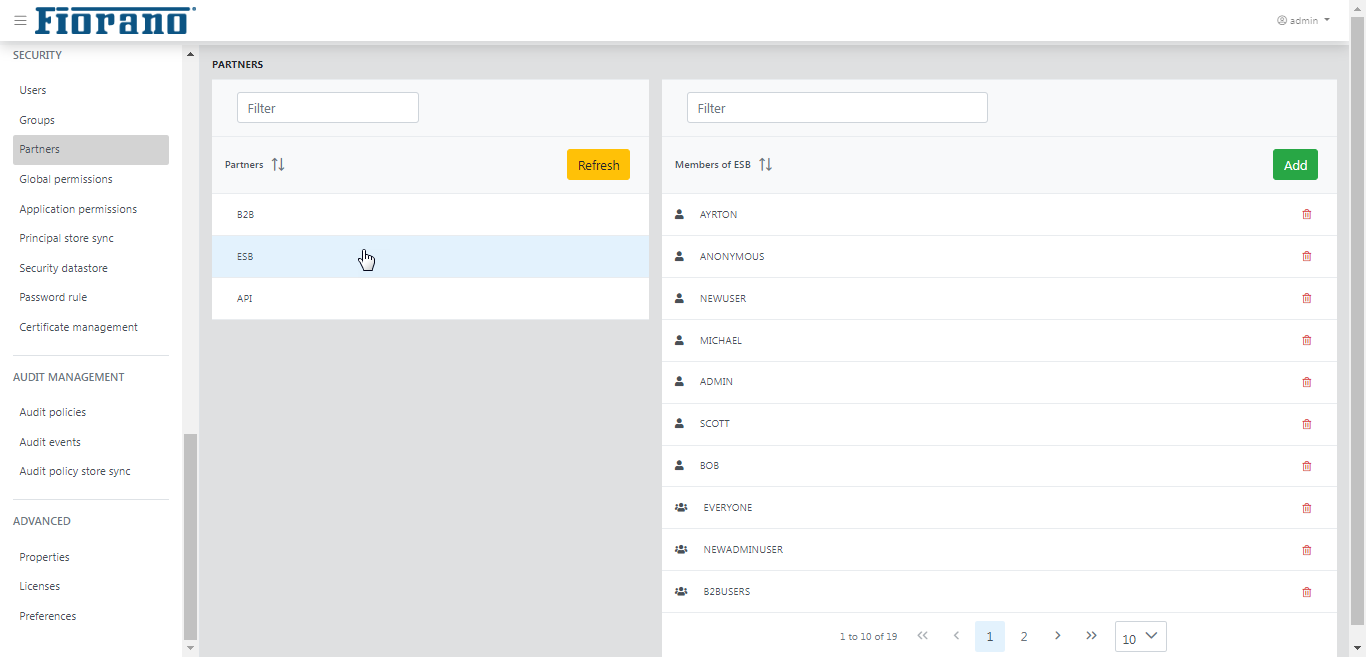
Partners help to create a collaboration of users and groups with other partners.
Click the partner node to see the list of members on the right-side panel. The panel on the right side allows adding as well as deleting its members who can be a user, group, or partner.
Global Permissions
This tab shows the global permissions that are currently available in the Fiorano network.
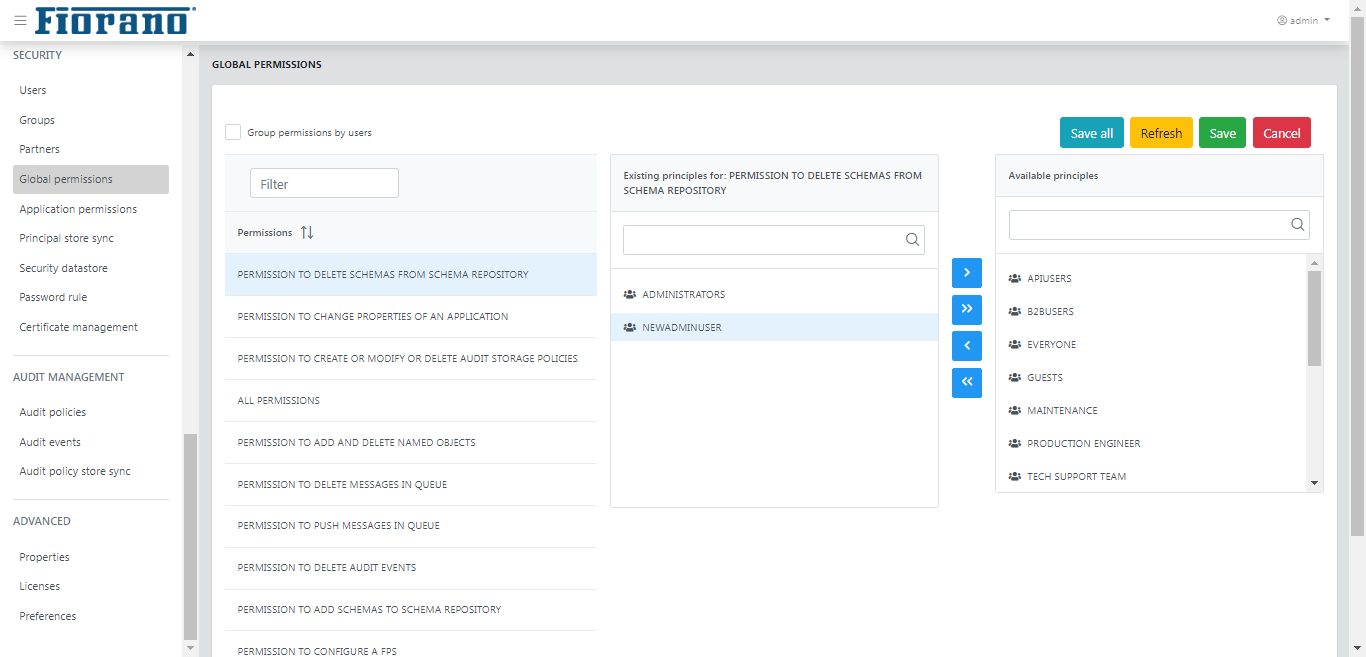
Figure 44: Global Permissions
Permissions can be assigned in ways:
- Selecting a permission and assigning users who need the particular permission.
- Selecting a user and assigning permissions that are required for the particular user. Select the Group permissions by users option to assign permissions based on a user.
List of permissions
| Permission | Description |
|---|---|
| PERMISSION TO ADD AND DELETE NAMED OBJECTS | To delete named configurations |
| PERMISSION TO VIEW AND USE NAMED OBJECTS | To view named configurations |
| PERMISSION TO CHANGE PASSWORD RULES | To change password rules |
| PERMISSION TO DELETE AUDIT EVENTS | To delete audit events |
| PERMISSION TO CREATE OR EDIT AND DELETE A PRINCIPAL | To add, edit, or delete group/user |
| PERMISSION TO REINJECT SBW DOCUMENTS | To reinject SBW documents |
| PERMISSION TO DELETE SBW DOCUMENTS | To view and delete SBW documents |
| PERMISSION TO EDIT APPLICATION LEVEL DOC TRACKING | To edit application-level document tracking configuration |
| PERMISSION TO CREATE OR UPDATE AND DELETE A SERVICE | To add, edit, and delete a microservice |
| ALL PERMISSIONS | To view and perform any action |
| PERMISSION TO CONFIGURE A FPS | To configure FPS |
| PERMISSION TO CREATE OR EDIT AND REMOVE SERVICE ACL | To create or edit and remove service ACL |
| PERMISSION TO VIEW RUNNING AND SAVED APPLICATIONS | To view running and saved applications |
| PERMISSION TO MODIFY EXISTING NAMED OBJECTS | To modify existing named objects |
| PERMISSION TO ADD SCHEMAS TO SCHEMA REPOSITORY | To add schemas to schema repository |
| PERMISSION TO LAUNCH AN APPLICATION | To launch an application |
| PERMISSION TO ADD OR REMOVE APPLICATION BREAKPOINT | To add or remove application breakpoint |
| PERMISSION TO REMOTELY ADMINISTRATE AN APPLICATION | To remotely administrate an application |
| PERMISSION TO KILL AN APPLICATION | To kill an application |
| PERMISSION TO CLEAR USER EVENTS | To clear user events |
| PERMISSION TO CHANGE PROPERTIES OF AN APPLICATION | To change the properties of an application |
| PERMISSION TO COMPOSE AN APPLICATION | To compose an application |
| PERMISSION TO EDIT APPLICATION LEVEL DOC TRACKING | To edit application-level doc tracking |
| PERMISSION TO DELETE AUDIT EVENTS | To delete audit events |
| PERMISSION TO ADD AND DELETE NAMED OBJECTS | To add and delete named objects |
| PERMISSION TO CHANGE PASSWORD RULES | To change password rules |
| PERMISSION TO VIEW AND USE NAMED OBJECTS | To view and use named objects |
| PERMISSION TO ADMINISTRATE A GROUP | To administrate a group |
| PERMISSION TO CREATE OR MODIFY OR DELETE AUDIT STORAGE POLICIES | To create, modify or delete audit storage policies |
| PERMISSION TO CREATE AN ACL | To create an ACL |
| PERMISSION TO CREATE OR EDIT AND DELETE A PRINCIPAL | To create, edit, and delete a principal |
| PERMISSION TO DELETE SCHEMAS FROM SCHEMA REPOSITORY | To delete schemas from the schema repository |
| PERMISSION TO PUSH MESSAGES IN QUEUE | To push messages in the queue |
| PERMISSION TO REINJECT SBW DOCUMENTS | To reinject SBW documents |
| PERMISSION TO CREATE OR UPDATE AND DELETE A SERVICE | To create, update and delete a service |
| PERMISSION TO DELETE SBW DOCUMENTS | To delete SBW documents |
Admin users will have all the permissions.
Application Permissions
This tab shows the application permissions that are available in the Fiorano network. This tab allows to edit the application permissions for a user.
Application-level permissions override global-level permissions. For example, if a user is given launch permission for applications in global permissions, but for a particular application, if the user is not granted permission to launch that application, then the user will not be allowed to launch that particular application.
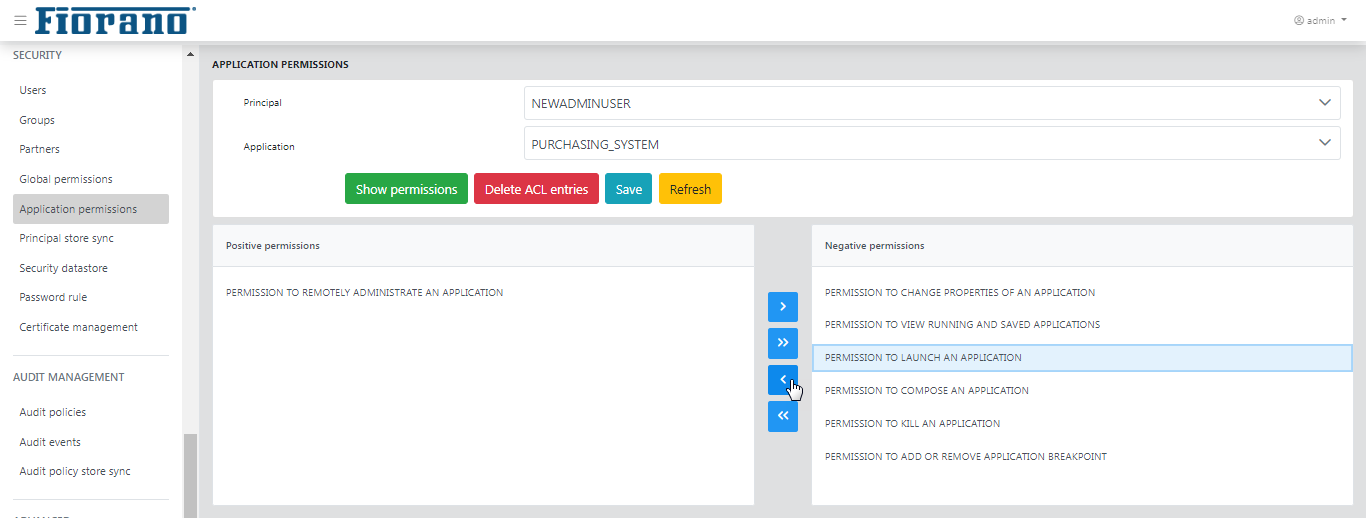
Figure 45: Application Permissions
Principal Store Sync
This tab shows the principal store synchronization status for the connected peers. This also allows you to synchronize the store for a peer.
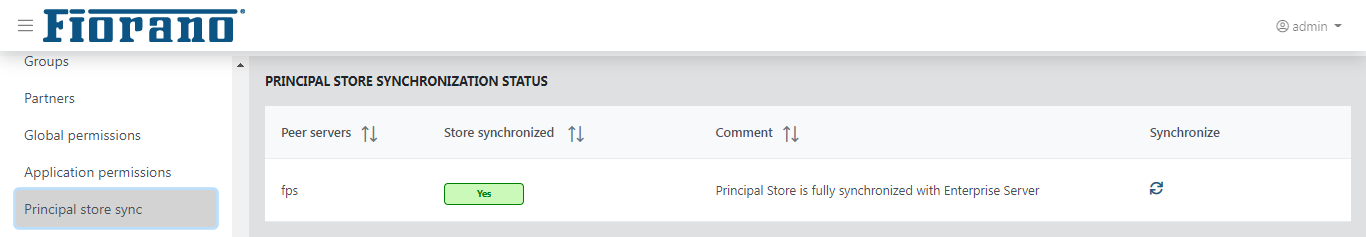
Figure 46: Principal Store Sync
Security Datastore
This tab shows the Security Datastore of the Enterprise Network. It also allows the authorized user to reset the entire Security Datastore viz. the Principals and the ACLs to system default.
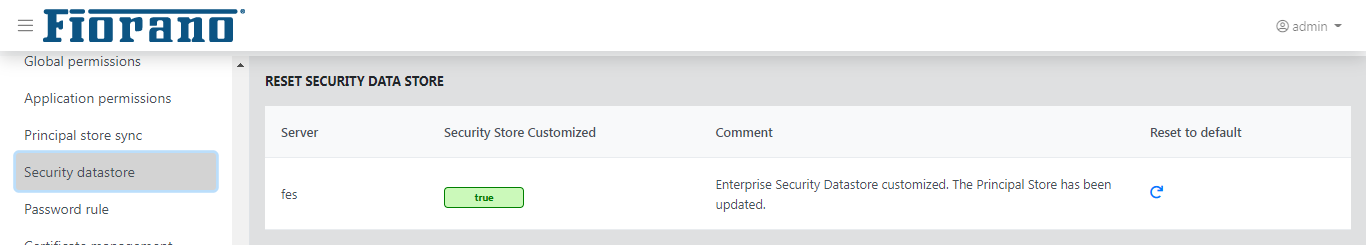
Figure 47: Security Datastore Reset
Password Rules
This tab shows the validation and strength rules that are used for matching the passwords or determining their strengths. This tab allows to add new rules or remove an existing one. By default, Strength rules are available but no validation rules are provided.
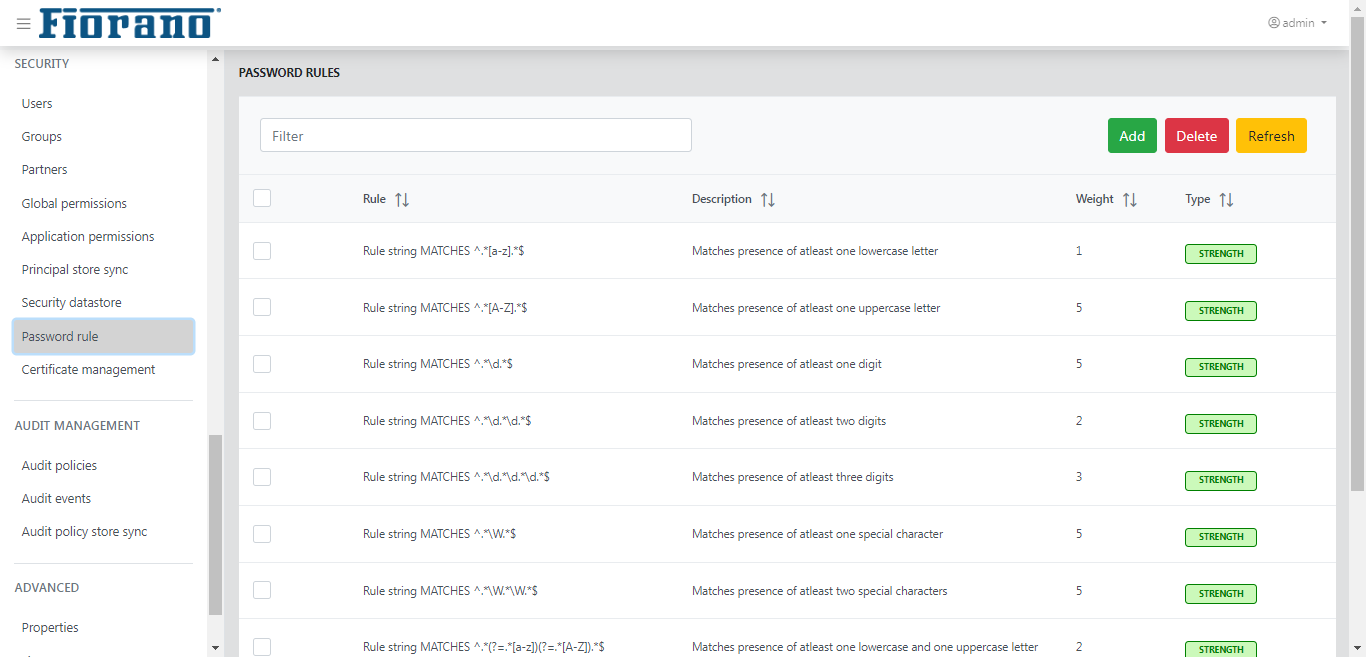
Click the Add rule button to add a new rule with Rule type Validation/Strength and Rule class Length/Match.
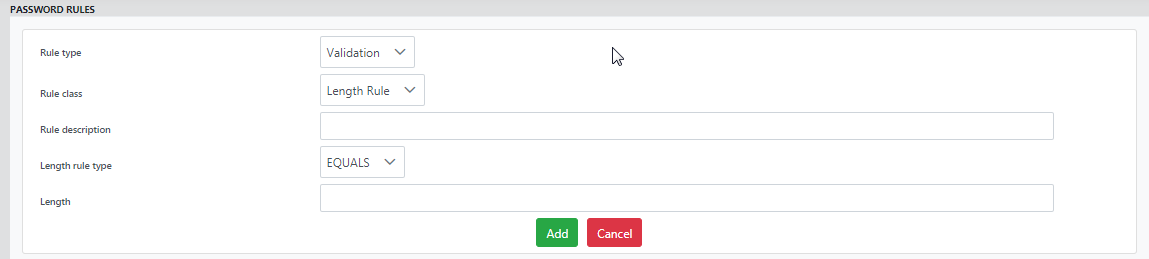
Figure 48: Password Rules
Certificate Management
This feature shows the list of keys of the server's trust store. This also allows to add or remove keys to server's trust store. Click the Add key button to add a key.
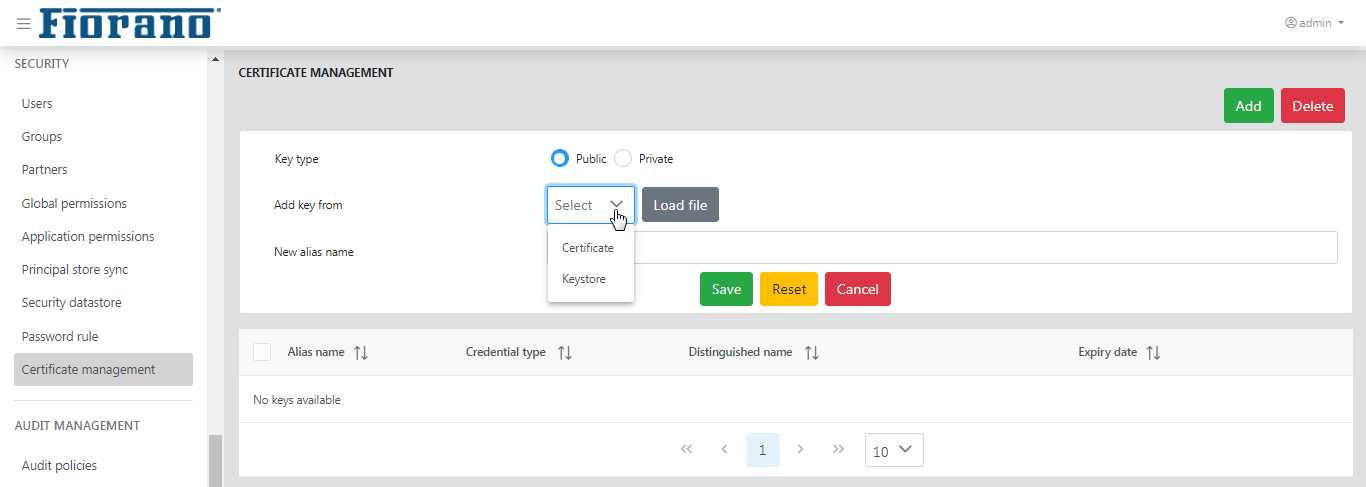
Figure 49: Certificate Management options
To add a key,
Select Private or Public.
In the Add key from drop-down, select "keystore" or "certificate" and click the Load File button to provide further details.
In the Add keystore File dialog box, click the Choose button to add the keystore file and provide the keystore password to load keys from the keystore, and click Upload.
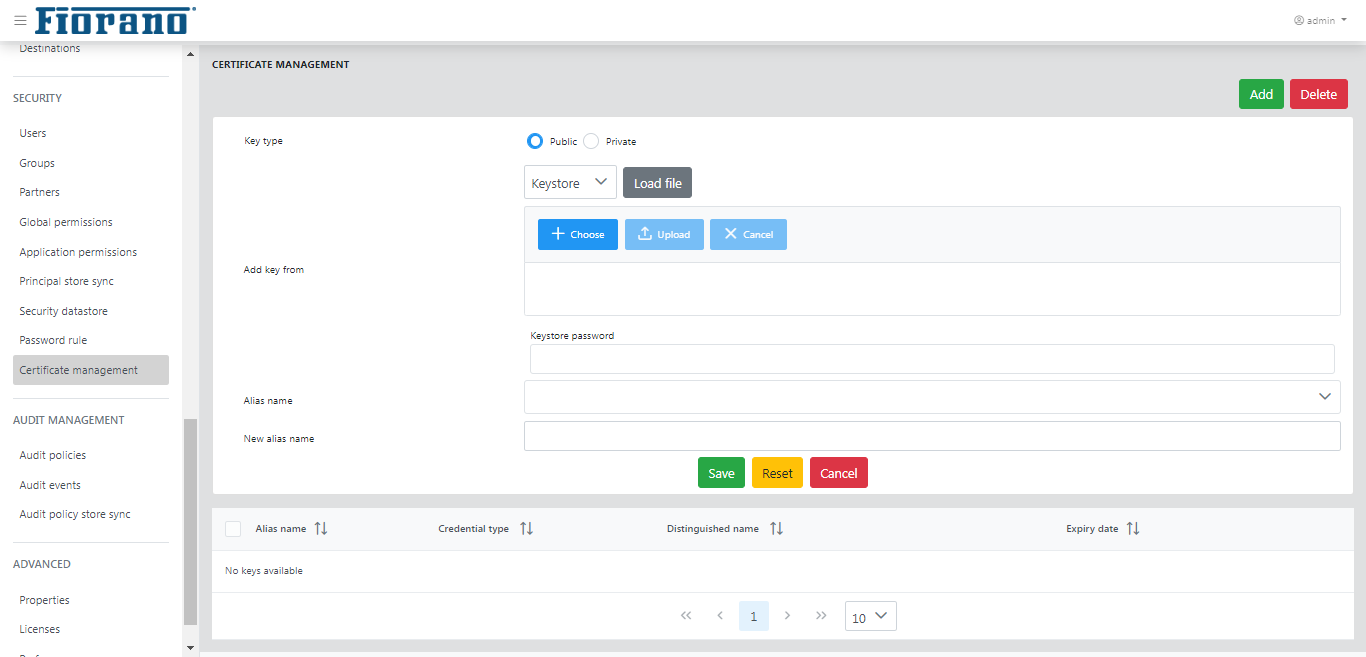
- Select the key from Alias Name drop-down and click the Save button to apply the changes. After successful save, keys get displayed in the key under List of Keys tab.
- To remove keys from trust store, click the Delete button.
Audit Management
Audit Management section in web console allows defining audit policies and searching for audit events as per requirement. This section has been divided into 3 sub-sections.
- Policies
- Events
- Audit policy store sync
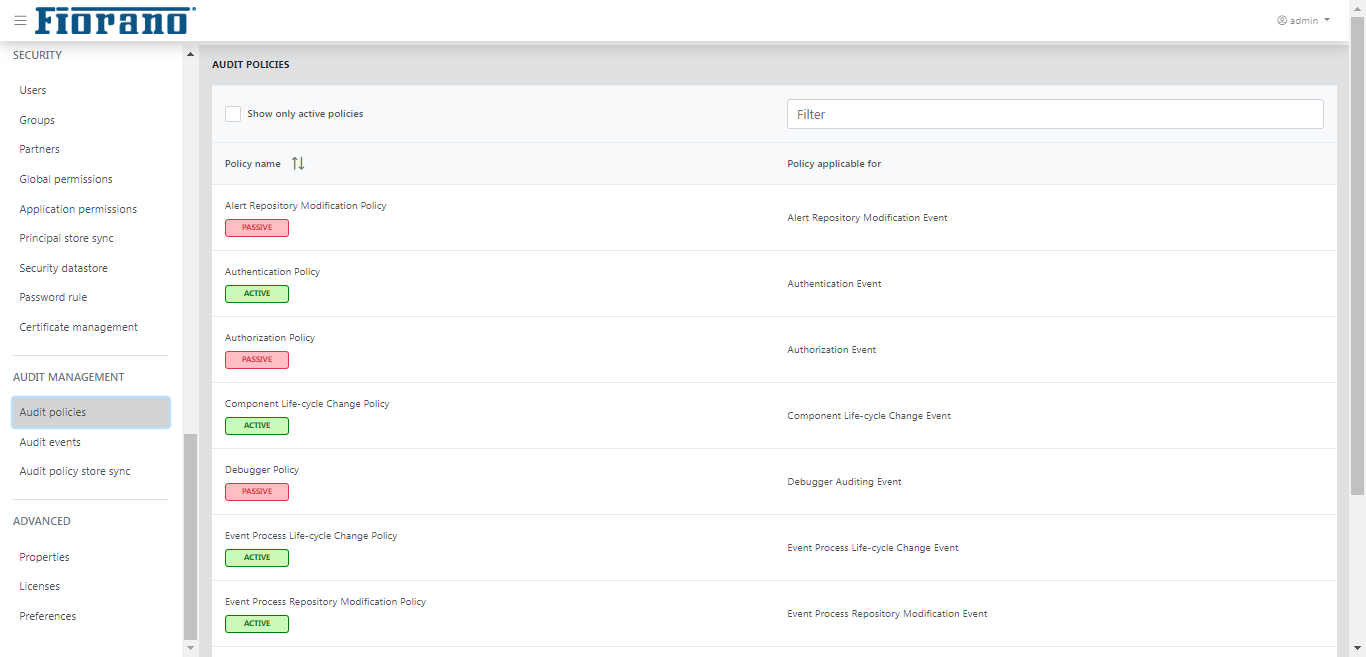
Audit Policies
In this view, you can view/edit available audit policies. These policies define the actions that will be audited by the system. In a fresh installation, all policies are in passive state, meaning none of the action is audited. You can selectively enable the actions that they want to audit.
The Show only active policy option helps to filter active policies.
Click a policy name to set the policy with status and category accordingly.
- Event status
- Success
- Failure
- Event category
- Information
- Error
- Warning
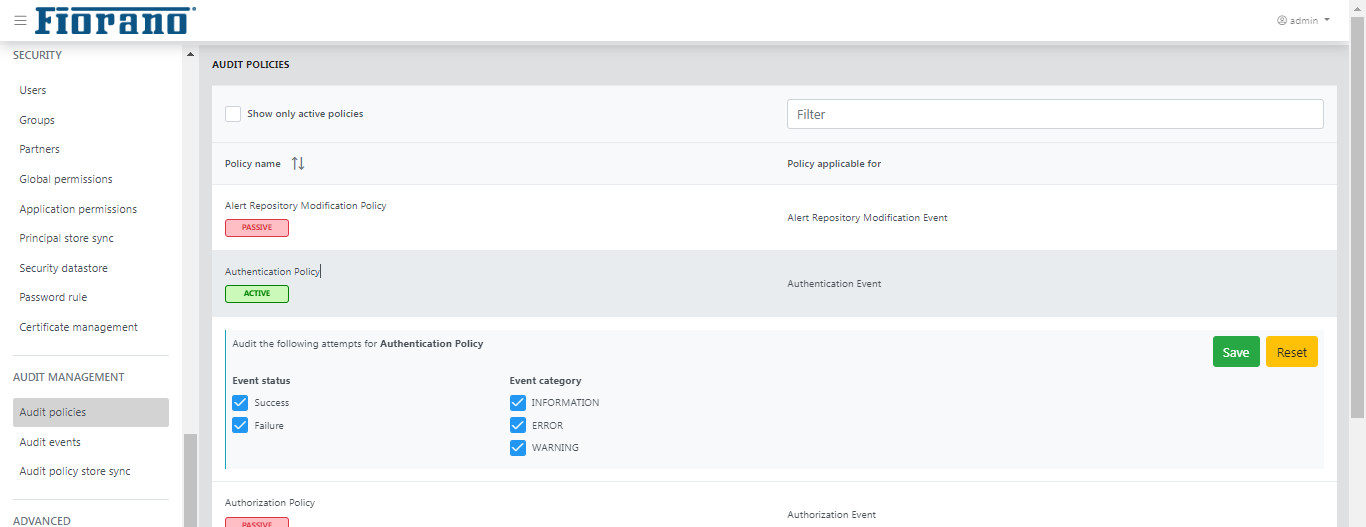
Figure 54: Policies
Audit Events
This view shows audit events based on the specified search criteria. A comprehensive list of audit event filters is available to refine the audit events as per requirement. This view also allows saving search preferences for later use, thus avoiding the painful task of creating audit filters each time you need to search.
Select the required events from the drop-down options and click the Fetch events button to generate the list of audit events. The Delete events button helps to clear the list.
Below is a snapshot of Audit Events page rendered after searching for certain audit events.
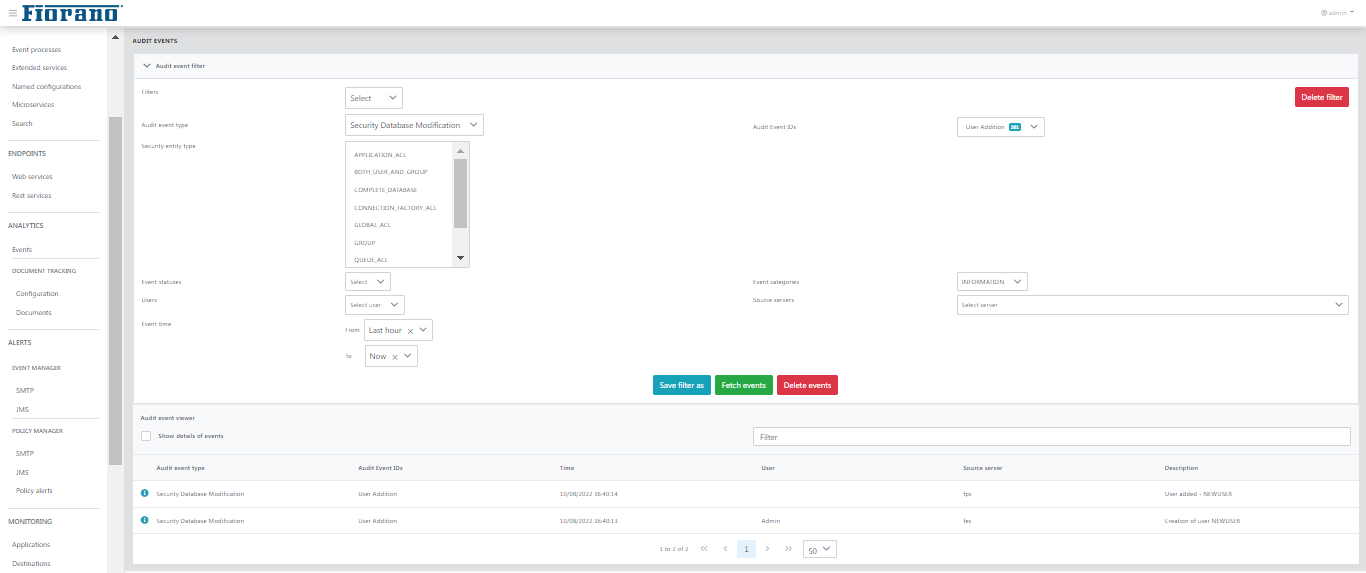
Figure 55: Event Viewer
Audit Policy Store Synchronization
This view shows the result of synchronization of audit policy store operation. A synchronized audit policy store means that the same audit policies (as in Enterprise Server) are active in peer servers as well.
If stores are not synchronized, the status field will display a cross mark in place of a tick mark and the reason for which the synchronization is not achieved will be displayed under the Comment column.

Audit policies can be force re-synchronized with a peer server by clicking the refresh icon under the Actions column.
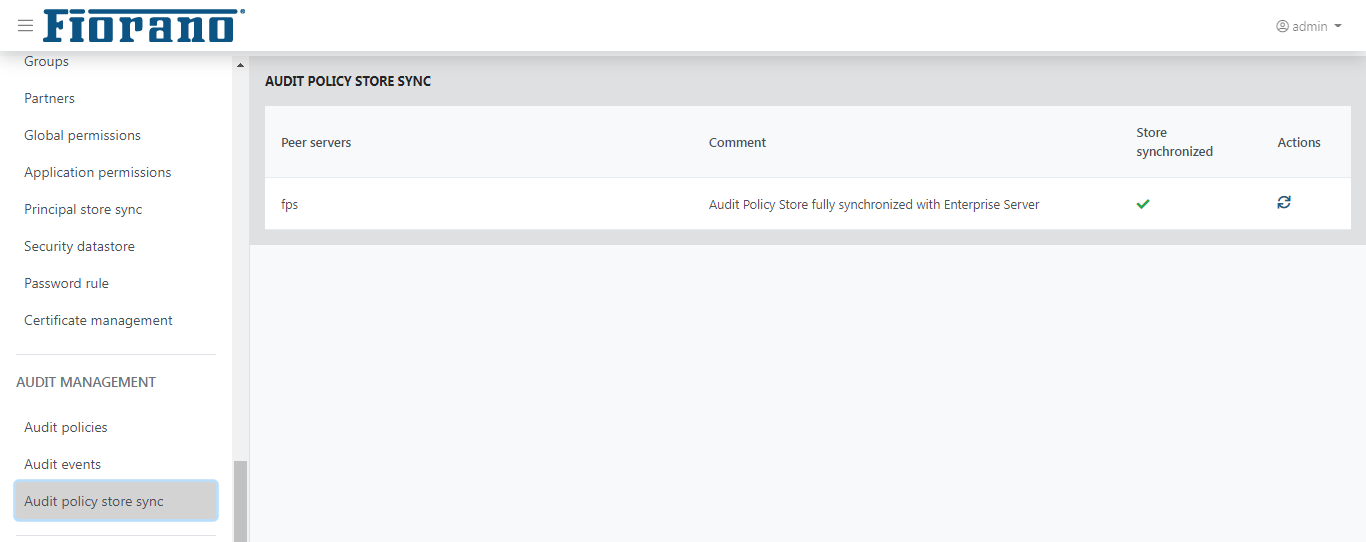
Figure 56: Audit Policy Store Synchronization
Refer to the Monitoring Events and Tracking Performance section for detailed information about the Fiorano Audit Management feature.
Advanced
Properties
This tab allows changing the values of frequently used server properties under the following sections:
Enable the Show description of properties option to display a note describing the purpose of each attribute.
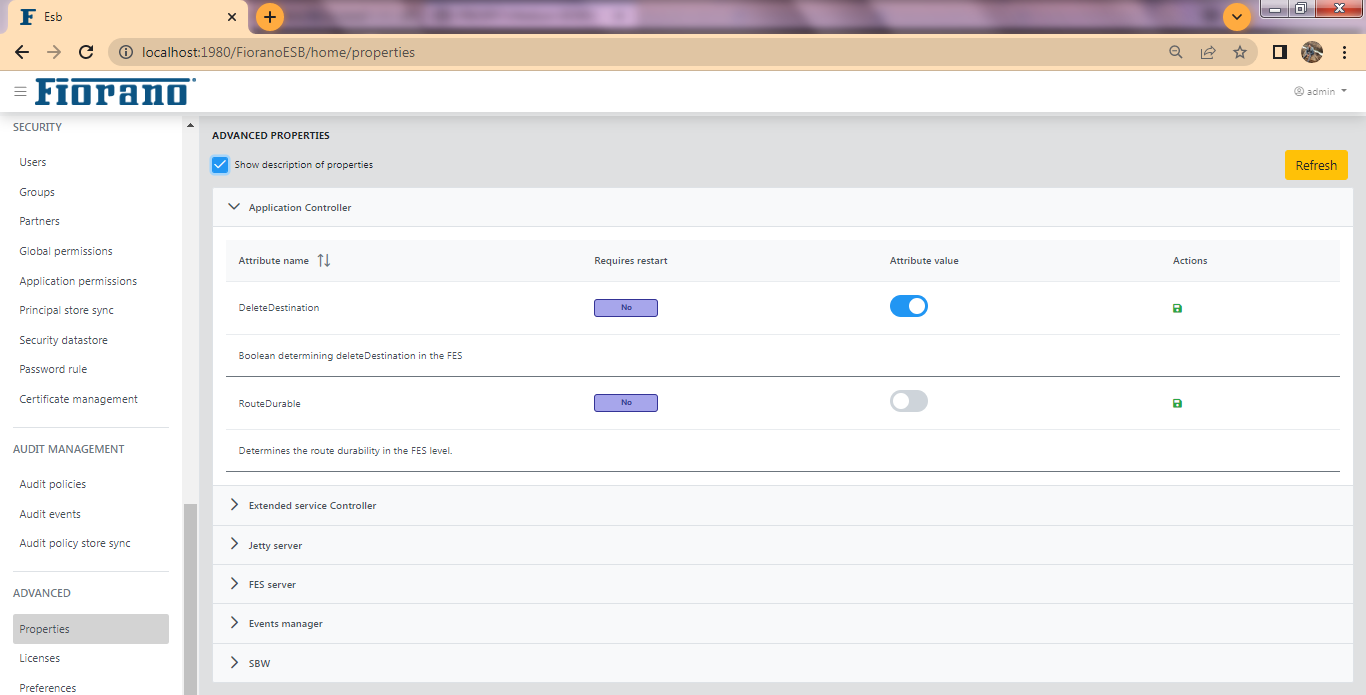
If the restart required option is enabled/disabled for an attribute value, it configures whether or not to restart a server to get that value into effect for the attribute.
It is based on the value present under the Is restrat required column. If the value is No and the Attribute value is enabled, the server needs to be restarted after a value is changed.
Click the Save icon under the Actions column to save a changed configuration and then click the Refresh button to keep the change into effect.
Attributes that can be changed are as follows
Application Controller
See the image above.
- Delete Destination: Boolean determining deleteDestination in the FES
- Route Durable: Determines the route durability in the FES level.
Extended Service Controller
- Delete Destination: Boolean determining deleteDestination in the FES
- Route Durable: Determines the route durability in the FES level.
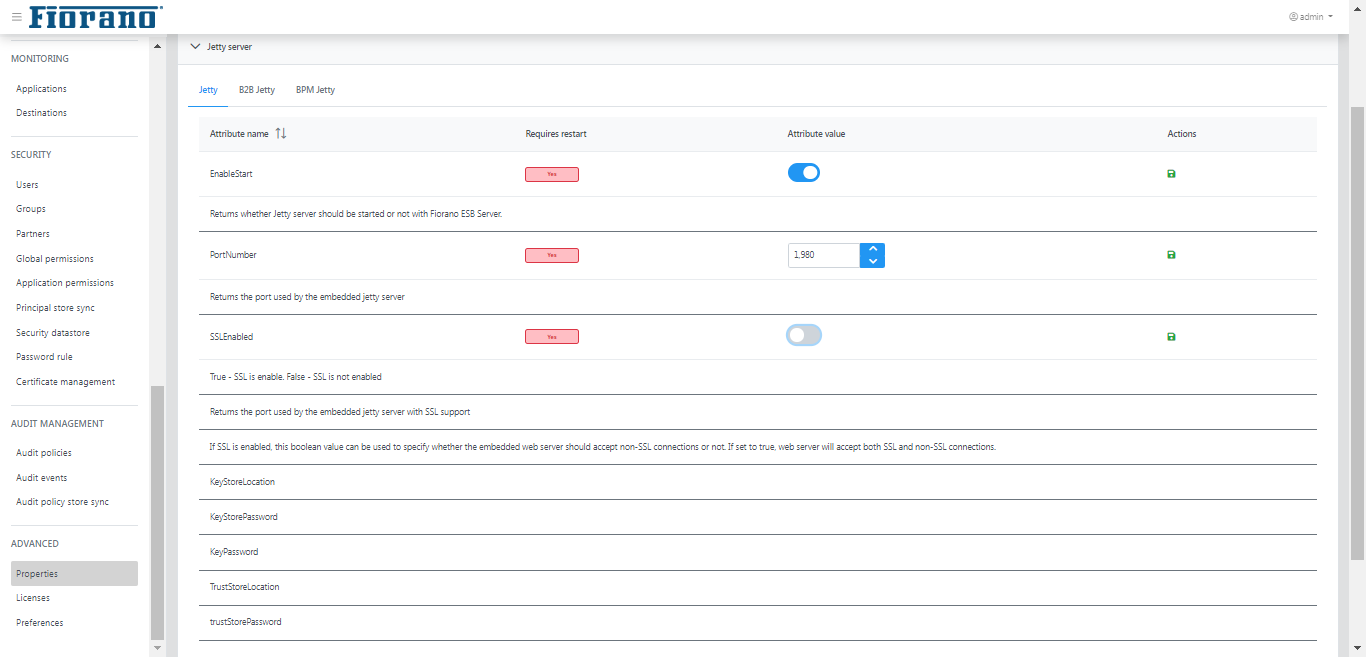
Jetty Server
The Jetty, B2B, and BPM Jetty tabs under Jetty Server section have the following options:
- EnableStart: Returns whether Jetty server should be started or not with Fiorano ESB Server.
- PortNumber: Returns the port used by the embedded jetty server
- DefaultConnectorEnabled: If SSL is enabled, this boolean value can be used to specify whether the embedded web server should accept non-SSL connections or not. If set to true, the web server will accept both SSL and non-SSL connections.
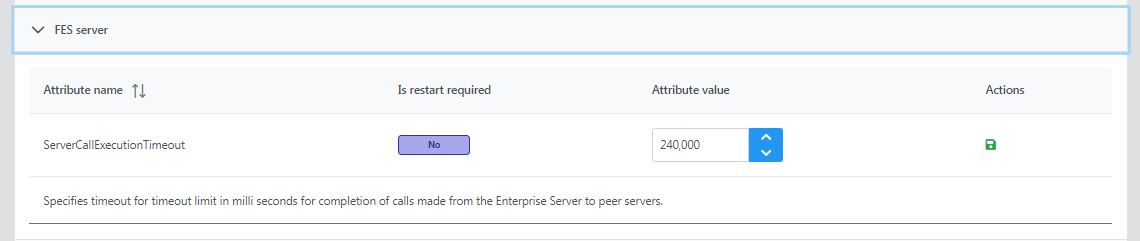
FES Server
ServerCallExecutionTimeout: Specifies timeout for timeout limit in milliseconds for completion of calls made from the Enterprise Server to peer servers.
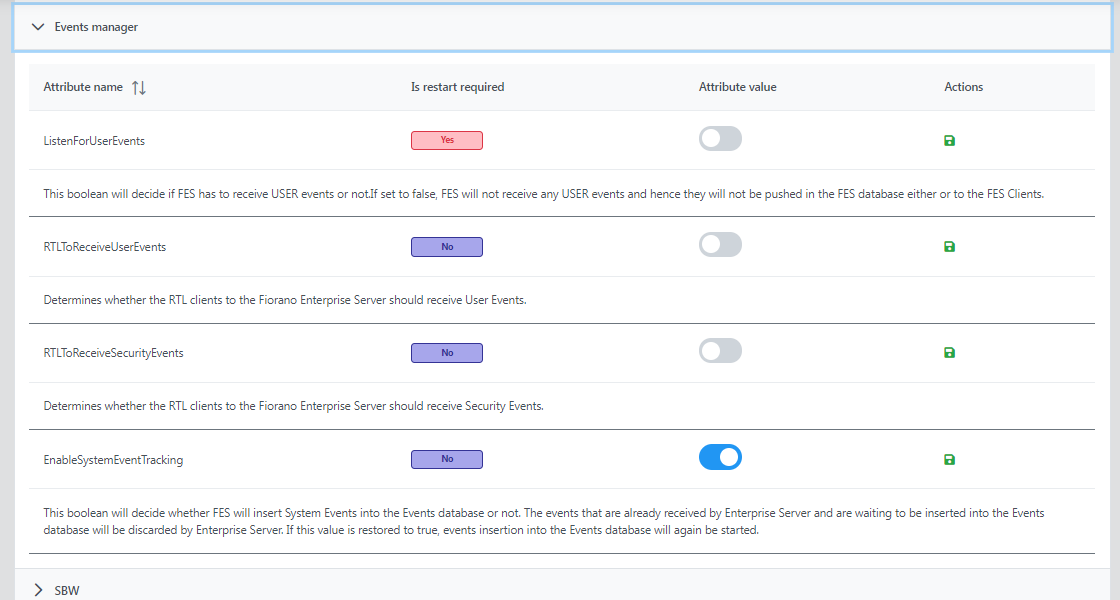
Events Manager
- ListenForUserEvents: This boolean will decide if FES has to receive USER events or not.If set to false, FES will not receive any USER events and hence they will not be pushed in the FES database either or to the FES Clients.
- RTLToReceiveUserEvents: Determines whether the RTL clients to the Fiorano Enterprise Server should receive User Events.
- RTLToReceiveSecurityEvents: Determines whether the RTL clients to the Fiorano Enterprise Server should receive Security Events.
- EnableSystemEventTracking: This boolean will decide whether FES will insert System Events into the Events database or not. The events that are already received by the Enterprise Server and are waiting to be inserted into the Events database will be discarded by the Enterprise Server. If this value is restored to true, events insertion into the Events database will again be started.
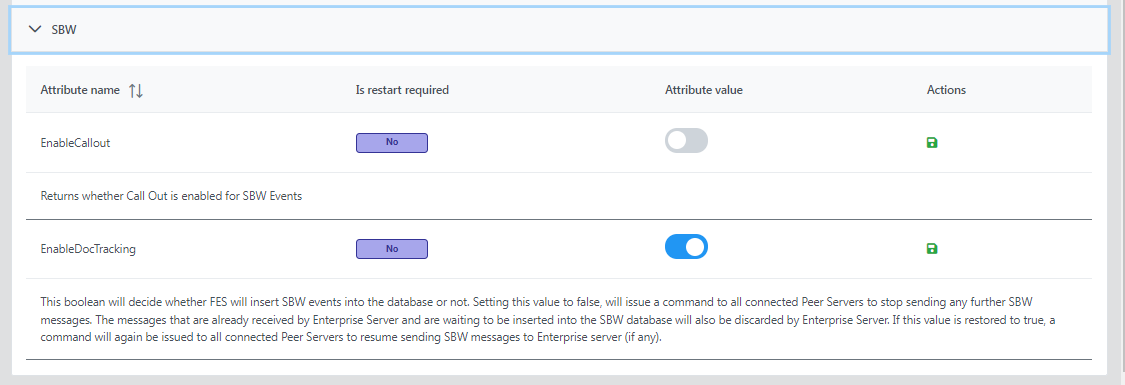
SBW
- EnableCallout: Returns whether Call Out is enabled for SBW Events
- EnableDocTracking: This boolean will decide whether FES will insert SBW events into the database or not. Setting this value to false will issue a command to all connected Peer Servers to stop sending any further SBW messages. The messages that are already received by Enterprise Server and are waiting to be inserted into the SBW database will also be discarded by Enterprise Server. If this value is restored to true, a command will again be issued to all connected Peer Servers to resume sending SBW messages to Enterprise server (if any).
Enabling Fiorano Web Console
The Fiorano Web Console can be enabled from Online as well as Offline mode.
Online mode
To enable Fiorano Web Console in online mode (server running):
- Login to Peer server via JMX(FPS-JMX)
- Navigate to Fiorano > etc > Jetty Server > JettyServer > config and set EnableStart property to 'yes'.
- Right-click on FPS-JMX and click Save Configurations option.
- Shut down both Peer and Enterprise servers.
Offline mode
To enable Fiorano Web Console in offline mode (server not running):
- Open profile in eStudio, browse to Fiorano > etc > Jetty Server > JettyServer > config, and set EnableStart property to 'yes'.
- Save profile.
After editing profile (online or offline), perform the following actions:
Clear peer repository using the following command
CODEclearDBServer.sh -mode fes -profile <fes_profile_Name>- Restart the servers.
While starting the peer server, the port for WMT will be listed as the Dashboard Listening Port.
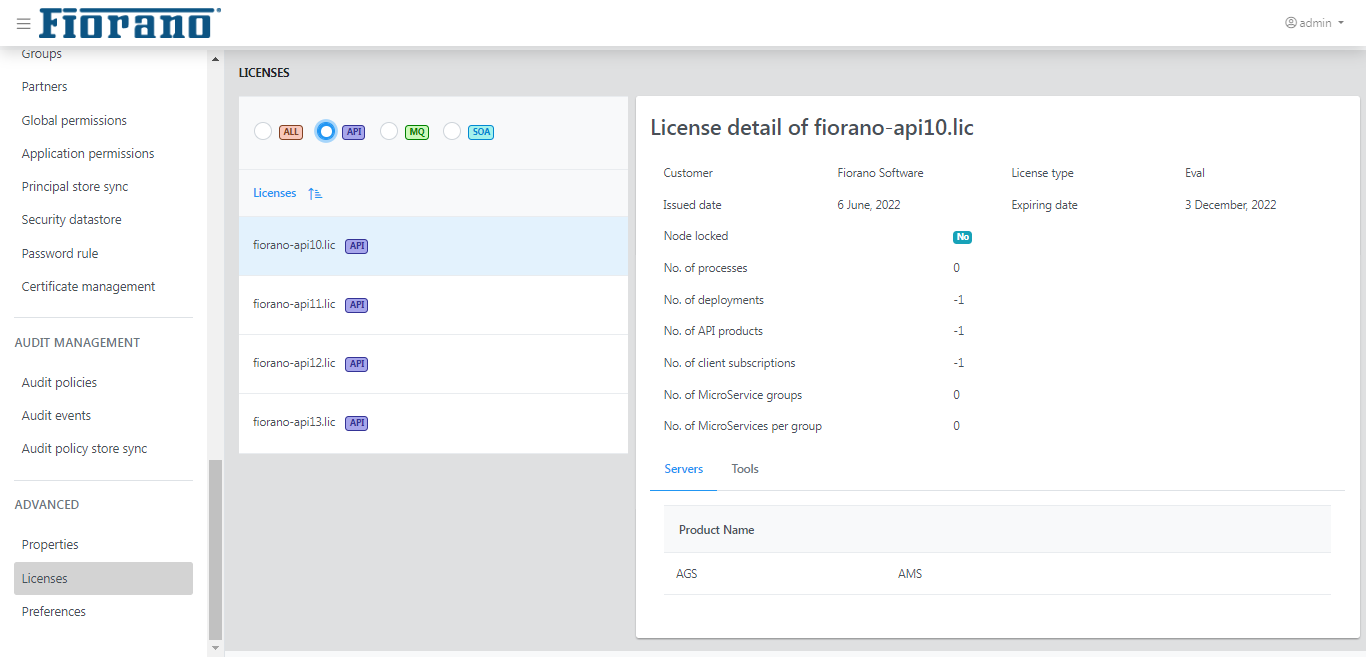
Licenses
This page lists the details of licenses that belong to API, MQ, and SOA of all versions of Fiorano.
Select a license to view the details of a license.
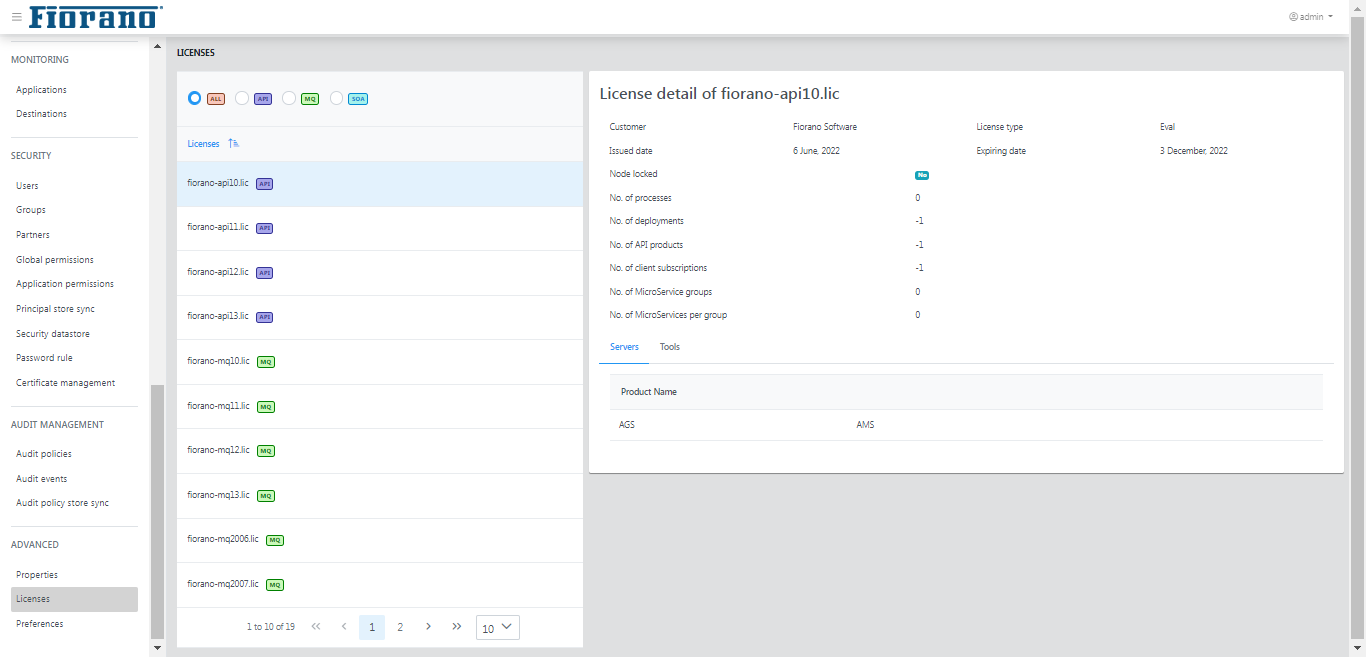
By default, all licenses appear on the page. It can be segregated based on whether it belongs to API, MQ, or SOA.
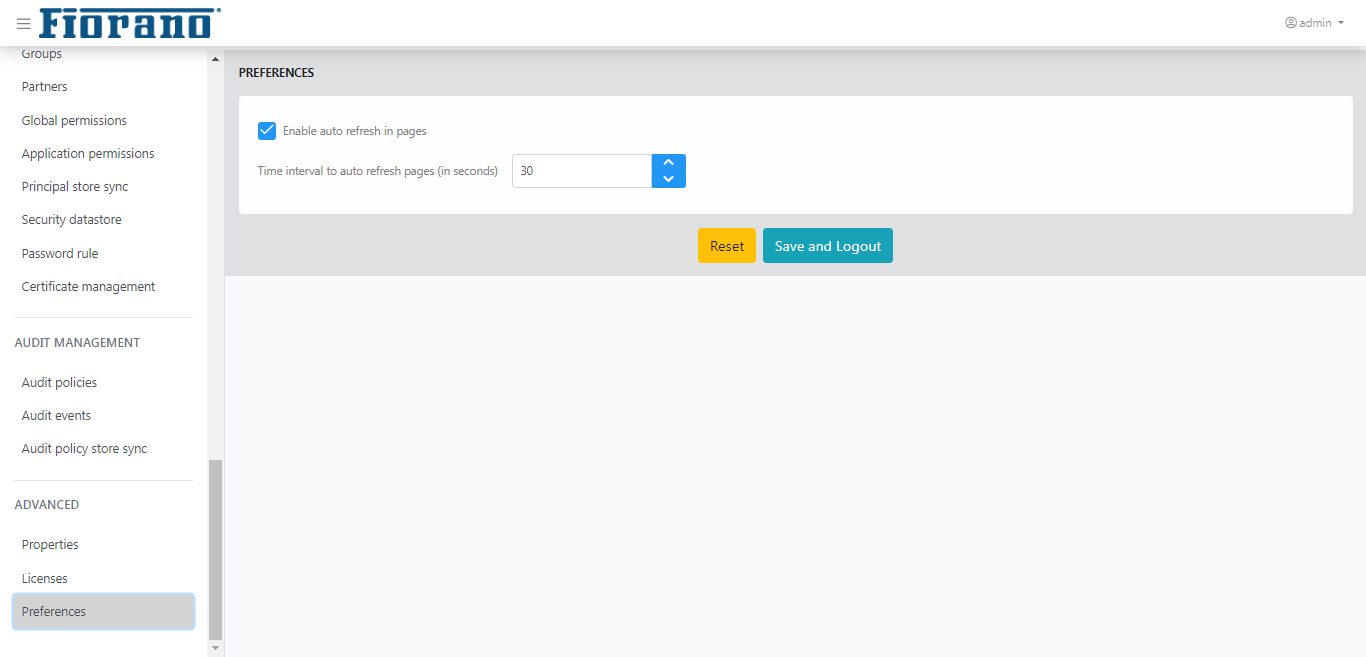
Preferences
The "Enable auto refresh in pages" property helps to refresh the Enterprise servers and Peer servers pages in the ESB dashboard at the interval of time specified in the "Time interval to auto refresh pages (in seconds)" text box.
The default value is 30 seconds. Disable the "Enable auto refresh in pages" property, to disable this functionality.