Authentication
The Fiorano Platform users and groups can operate from all available nodes in the Fiorano Network. The Fiorano ESB Dashboard can be used to configure and manage user authentication. A group is identified by a unique name and contains a list of users who inherit all rights assigned to a group. Each user is assigned a unique user name, password, and group membership. Information pertaining to users and groups are utilized while authenticating and enables to determine the resources of a user or a group that is allowed to access.
The Fiorano ESB Dashboard allows you to manage all principals in a Fiorano Network.
To view the list of principals, click the Groups tab under the SECURITY section in the left navigation pane. CLick the respective group to view the principal list.
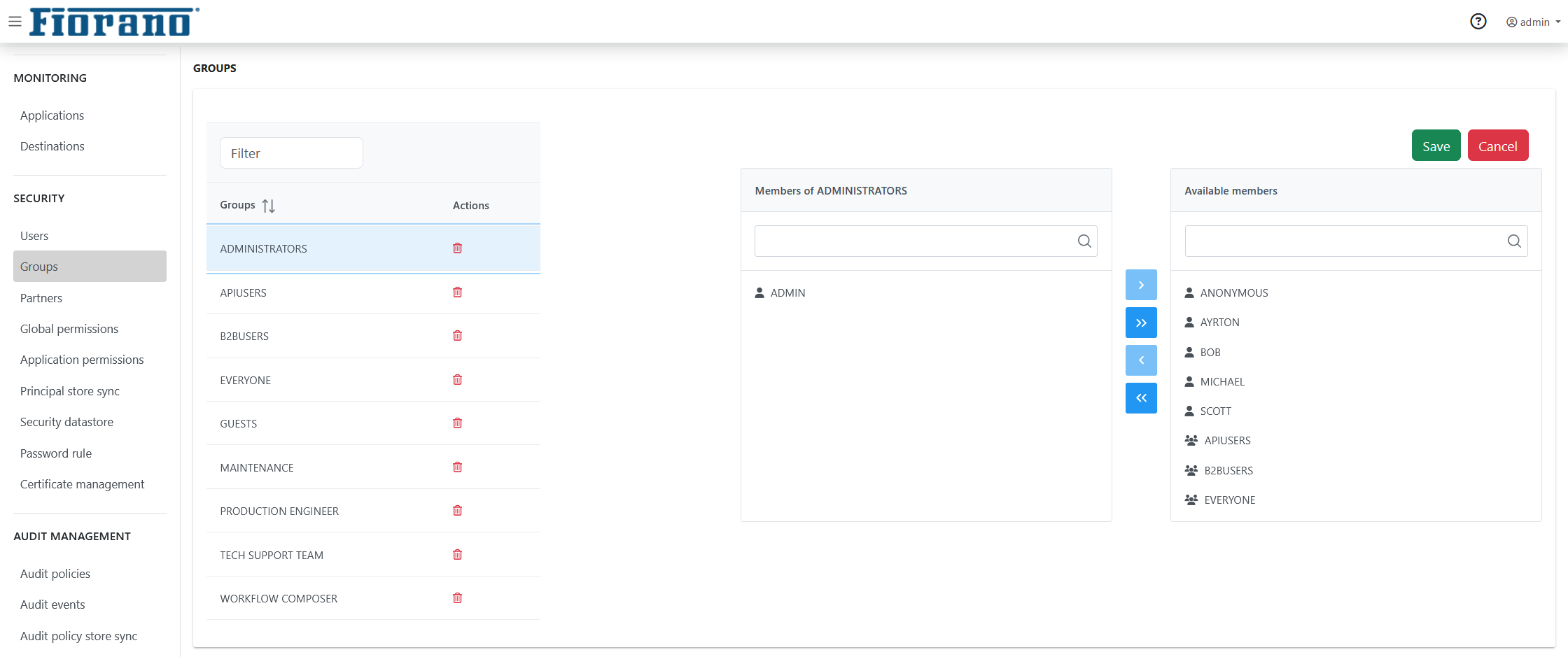
Figure 1: Groups List
You can perform the following management tasks:
- Creating user accounts
- Deleting user accounts
- Changing the password of a user
Similarly, the Groups node allows the administrator to club users into specific groups and provide appropriate levels of Authorization.
Write Security API keys to Cassandra
Fiorano servers provide a feature to store security-based API keys in Cassandra databases. This feature is generally used in cases where the same keys have to be used across multiple environments for authentication.
For the smooth usage of this feature, it is recommended to use the RDBMS-based Security feature to share the same security realm database across multiple environments. Configuration for the same can be checked here.
Enable write of API keys to Cassandra
Steps to enable writing security API keys to the cassandra database:
- Start eStudio, and open FES profile by navigating to Profile Management > <EnterpriseServerProfile> > fes
- In FES profile, navigate to Fiorano > ESB > Security > User > UserSecurityManager
- Configure the Cassandra properties as shown in the figure below:
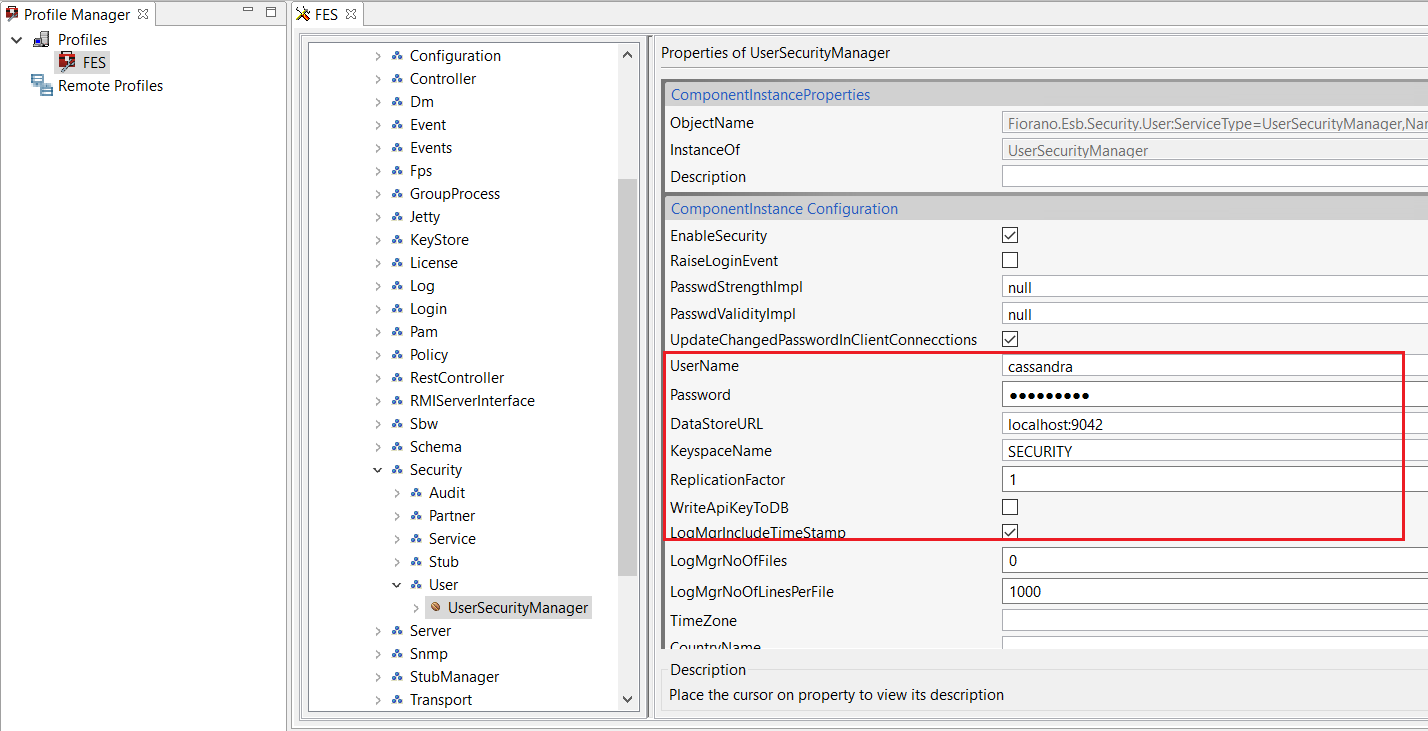
Figure 2: API key to Cassandra DB configuration - Select the WriteApiKeyToDB checkbox, save the profile
Restart the server and check if the new API keys generated after the change are being written into Cassandra. The API keys generated after this change can be directly read from multiple environments that contain the same Cassandra DB configuration.
Password Rules
For security purpose, Fiorano Enterprise Server provides a feature to define the password validity and strength check rules for accepting password while adding a new user or changing the password of existing user.
Password Strength
The strength of a password is defined on a logical scale and suggests the user that how secure is the password provided by him. Password Strength can be categorized into one of the following categories:
- VERY WEAK
- WEAK
- AVERAGE
- ABOVE AVERAGE
- STRONG
- VERY STRONG
Password Validation
Whereas Password Strength Check defines guidelines for choosing a good password, Password Validation checks put restrictions on which passwords are valid and which ones are invalid. Invalid passwords will not be accepted by the system and the user will be prompted to provide a new password.
Password strength and validation rules are defined per profile basis, that is, the rules can be changed per Enterprise Server profile.
To know more about how password validation and strength check rules can be added or deleted refer the Security section.
Custom Password Rule Implementation
Fiorano Enterprise Server provides the user the flexibility to override the default implementation of password rules and execute custom implementation to write customized Java Class for checking both password strength and validity.
Steps to define a custom implementation for checking password strength and validity. Users who wish to override the default implementation and provide their own custom implementation should implement the following interface:
- "IStrengthChecker.java" for password strength check
- "IValidationChecker.java" for password validation check
Both of these interfaces are defined in package "fiorano.tifosi.dmi.rule.passwd.api". For more information please refer to the javadoc of these APIs in $FioranoHome/javadoc/esb/dmi/fiorano/tifosi/dmi/rule/passwd/api/
After defining your own custom implementation for one or both of password strength and validation check, please follow the below-mentioned steps to configure Enterprise Server for overriding the default implementation with your custom implementation:
- Compile the custom class/classes and create a jar of them. Refer link http://java.sun.com/docs/books/tutorial/deployment/jar/build.html to see how jar files are created.
- Include the jar in the classpath of Enterprise Server by adding the full path of the jar in server.conf or fes.conf (depending on you are using server.bat/server.sh or fes.bat/fes.sh for starting Enterprise Server) under the tag <java.classpath> in the conf file.
- Start eStudio, and open FES profile by navigating to Profile Management > <EnterpriseServerProfile> > fes.
- In FES profile, navigate to Fiorano > ESB > Security > User > UserSecurityManager as shown in figure below:
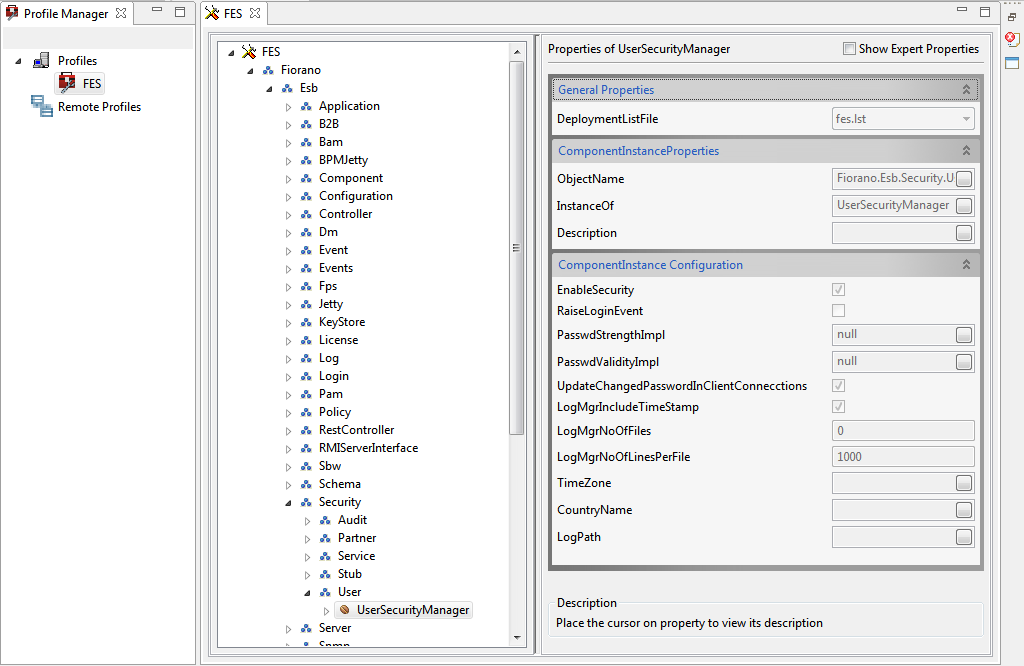
Figure 3: UserSecurityManager option - Click the ellipsis button of "PasswdStrengthImpl" in the Properties of UserSecurityManager panel on the right side of Studio as shown in the figure below, provide the fully qualified classname (<package_name>.<class_name>) of the custom password strength check class. Similarly, for password validity check, click on the ellipsis of "PasswdValidityImpl" and provide the fully qualified classname of the custom password validity check class.
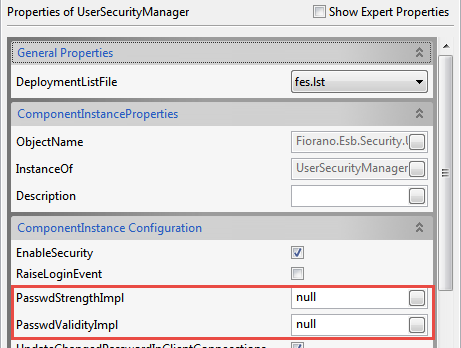
Figure 4: PasswdStrengthImpl and PasswdValidityImpl properties - Save the profile as shown in the figure below:
Figure 5: Saving the profile
The enterprise server starts using custom classes for checking password strength and validity
All the information described above regarding the password rules is valid only if the user is added through Dashboard. If Studio is used for adding a new user, the password rules will not imply as the Studio by default sets the password for the new user the same as the username.
