API Security
API security involves controlled and authenticated access to APIs, encrypted data, preventing malicious contents and other safety measures. In Fiorano API management, APIs are secured by attaching security policies. These policies enable protection from XML/JSON/Regex threats and provide authentication services as well.
Security policies available are:
- XML Threat Protection
- JSON Threat Protection
- Regex Protection
- Validate JSON
- SAML
- LDAP
- MonitorSLA
- JWS
- Encrypt Message
- Decrypt Message
- Tokenization
XML threat Protection
The XML Threat Protection policy protects API from any possible XML Threats by setting limits to various attributes present in the XML structure.
JSON Threat Protection
JavaScript object notation (JSON) is vulnerable to content-level attacks. Such attacks attempt to use structures that overwhelm JSON parsers to crash a service and induce application-level denial-of-service (DOS) attacks.
The JSON Threat Protection policy minimizes the risk posed by such attacks by enabling specific limits on various JSON structures such as arrays and strings. All settings are optional and should be tuned to optimize service requirements against potential vulnerabilities.
Validate JSON
The Validate JSON policy can be used to validate if a request or response conforms to the schema specified.
LDAP
The LDAP Policy can be used when the user needs to be authenticated while limiting the access to protected resources for certain users. The policy is also designed for retrieving Digital Number (DN) metadata for use in API proxy flows.
For example, an API call may be executed only after a user gets successfully authenticated against LDAP. Then DN attributes may be retrieved optionally for the user after the authentication succeeds.
MonitorSLA
The Monitor SLA policy is for cases where there is a need for monitoring and controlling different aspects of the proxy processing pipeline.
JWS
JWS (JSON Web Signature) policies are used to verify and generate digital signatures (using JSON-based data structures) to secure the content.
Encrypt Message
The Encrypt Message policy helps in encrypting messages before sending them to the target endpoint or an API consumer. Encryption is done based on a key (user-defined) and an algorithm.
Decrypt Message
The Decrypt Message policy helps in decrypting messages received from the target endpoint or an API consumer. To decrypt the data accurately, the correct key and algorithm used in the encryption of data need to be known.
Tokenization
Tokenization helps in storing sensitive Permanent Account Number information such as Credit Card numbers in a secure format to aid PCI DSS compliance.
SAML
Security Assertion Markup Language (SAML) is an XML-based framework that implements a secure method of passing user authentication and authorization between two entities: a Service Provider and an Identity Provider.
When a user logs into a SAML enabled application, the service provider requests an authentication assertion from the appropriate Identity Provider which is responsible to generate the required assertions to indicate that a user has been authenticated. On verifying the assertion, the Service provider lets the user access its service. The SAML policy is used to attach SAML assertions to outbound XML requests.
SAML policy is configured using the following policies:
- SAML Token Generation
- SAML Verification
Threats and counteractions
DOS attacks are counteracted by policies like those defined in API Access Management which can keep the API safe and secure.
Injection attacks (SQL, Xpath, XSS, Xquery)
It is counteracted by
- Input/Parameter validations
- Regex validation
- Monitor SLA (input size, response size)
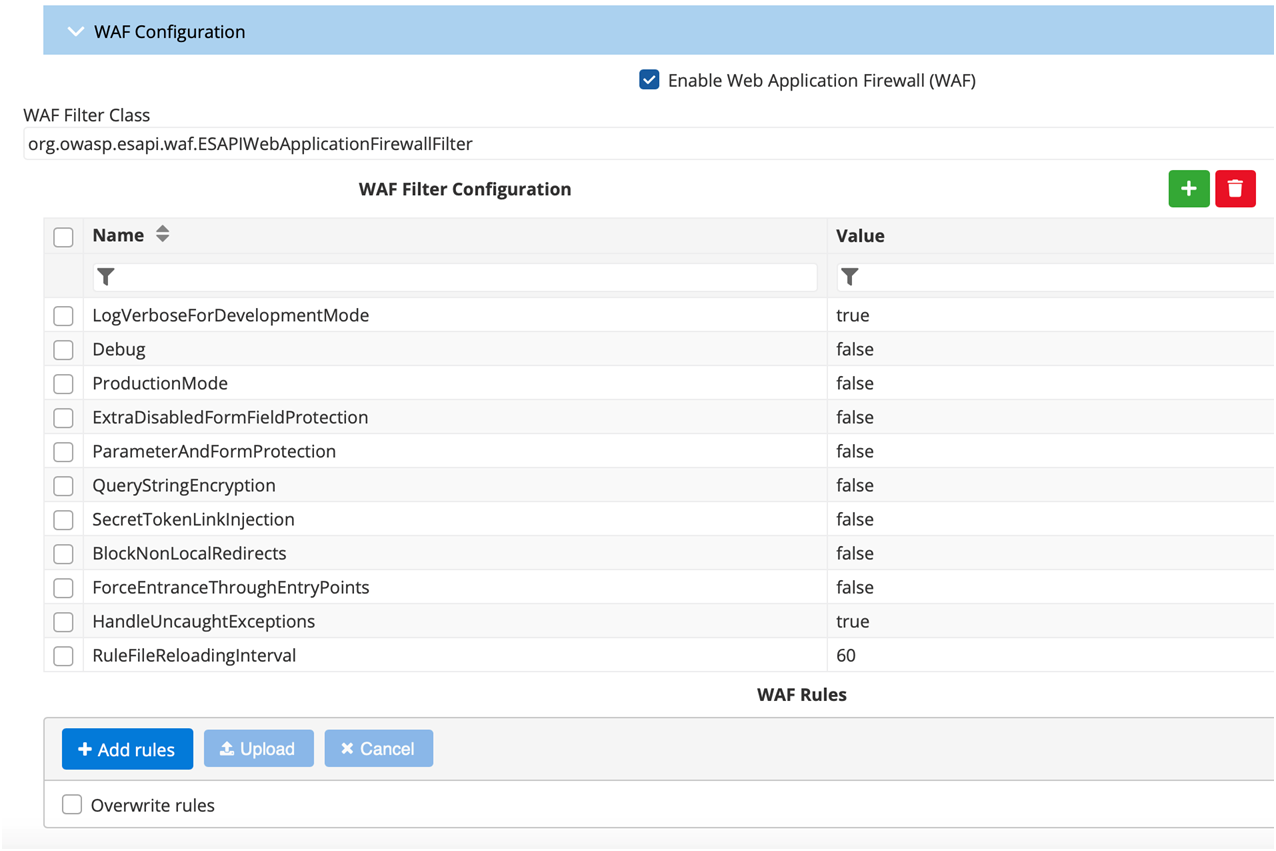
Web Application Firewall (WAF)
Fiorano API management supports pluggable WAF implementations. Rules, including the ones for OWASP Top Ten threats, can be configured for individual APIs.
Refer to the Configuring Web Application Firewall section.
External Integrations
- External/Partner products integration
- IAM solutions such as Apache Syncope
- Service callouts to integrate with any other security products.
